26 October, 2021
A Review Of Tested 350-701 Study Guides
Validated of 350-701 exam question materials and free draindumps for Cisco certification for IT specialist, Real Success Guaranteed with Updated 350-701 pdf dumps vce Materials. 100% PASS Implementing and Operating Cisco Security Core Technologies exam Today!
Question 1
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention System?
Question 2
What is a characteristic of Cisco ASA Netflow v9 Secure Event Logging?
Question 3
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
Question 4
How does Cisco Umbrella archive logs to an enterprise- owned storage?
Question 5
Which two mechanisms are used to control phishing attacks? (Choose two.)
Question 6
What provides visibility and awareness into what is currently occurring on the network?
Question 7
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
Question 8
Which VPN technology can support a multivendor environment and secure traffic between sites?
Question 9
Which information is required when adding a device to Firepower Management Center?
Question 10
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
Question 11
DRAG DROP
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.
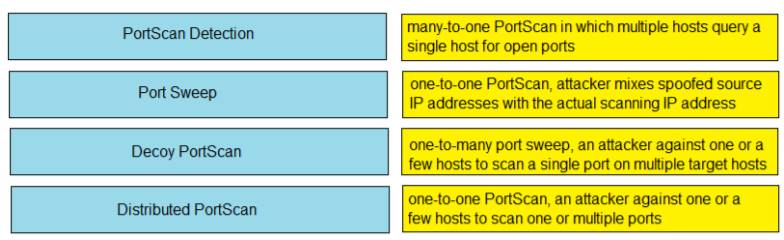
Solution:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
Does this meet the goal?
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.

Solution:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
Does this meet the goal?
Question 12
What are two Detection and Analytics Engines of Cognitive Threat Analytics? (Choose two.)
Question 13
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center?
Question 14
Which benefit does endpoint security provide the overall security posture of an organization?
Question 15
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view of activity?
Question 16
Which SNMPv3 configuration must be used to support the strongest security possible?
Question 17
What can be integrated with Cisco Threat Intelligence Director to provide information about security threats, which allows the SOC to proactively automate responses to those threats?
Question 18
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)
