15 August, 2021
A Review Of Vivid 156-215.80 Training Tools
Realistic of 156-215.80 free draindumps materials and test preparation for Check-Point certification for IT engineers, Real Success Guaranteed with Updated 156-215.80 pdf dumps vce Materials. 100% PASS Check Point Certified Security Administrator exam Today!
Online Check-Point 156-215.80 free dumps demo Below:
Question 1
- (Exam Topic 2)
The most important part of a site-to-site VPN deployment is the ____.
The most important part of a site-to-site VPN deployment is the ____.
Question 2
- (Exam Topic 1)
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp.
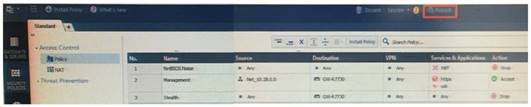
How will you describe the new “Publish” button in R80 Management Console?
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp.

How will you describe the new “Publish” button in R80 Management Console?
Question 3
- (Exam Topic 4)
Fill the blank. IT is Best Practice to have a _____ rule at the end of each policy layer.
Fill the blank. IT is Best Practice to have a _____ rule at the end of each policy layer.
Question 4
- (Exam Topic 2)
When using LDAP as an authentication method for Identity Awareness, the query:
When using LDAP as an authentication method for Identity Awareness, the query:
Question 5
- (Exam Topic 4)
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
Question 6
- (Exam Topic 2)
What does it mean if Bob gets this result on an object search? Refer to the image below. Choose the BEST answer.
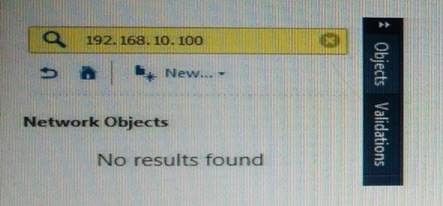
What does it mean if Bob gets this result on an object search? Refer to the image below. Choose the BEST answer.

Question 7
- (Exam Topic 4)
Which of the following is NOT a method used by Identity Awareness for acquiring identity?
Which of the following is NOT a method used by Identity Awareness for acquiring identity?
Question 8
- (Exam Topic 3)
Which the following type of authentication on Mobile Access can NOT be used as the first authentication method?
Which the following type of authentication on Mobile Access can NOT be used as the first authentication method?
Question 9
- (Exam Topic 4)
Access roles allow the firewall administrator to configure Network access according to:
Access roles allow the firewall administrator to configure Network access according to:
Question 10
- (Exam Topic 2)
Fill in the blank: Licenses can be added to the License and Contract repository _____.
Fill in the blank: Licenses can be added to the License and Contract repository _____.
Question 11
- (Exam Topic 3)
What happens if the identity of a user is known?
What happens if the identity of a user is known?
Question 12
- (Exam Topic 4)
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enable which path is handling the traffic?
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enable which path is handling the traffic?
Question 13
- (Exam Topic 1)
View the rule below. What does the lock-symbol in the left column mean? Select the BEST answer.

View the rule below. What does the lock-symbol in the left column mean? Select the BEST answer.

Question 14
- (Exam Topic 1)
Which of the following is NOT a SecureXL traffic flow?
Which of the following is NOT a SecureXL traffic flow?
Question 15
- (Exam Topic 4)
How would you determine the software version from the CLI?
How would you determine the software version from the CLI?
Question 16
- (Exam Topic 4)
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
Question 17
- (Exam Topic 1)
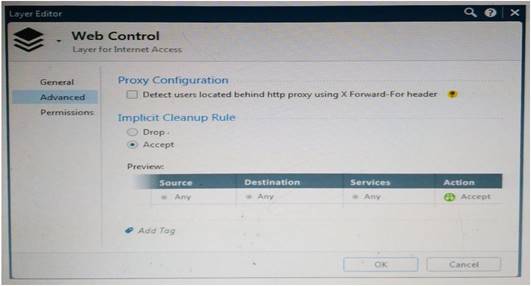
WeBControl Layer has been set up using the settings in the following dialogue:
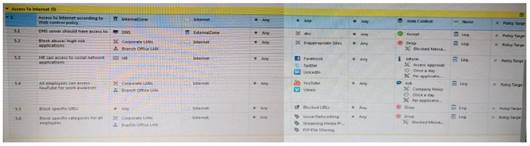
Consider the following policy and select the BEST answer.
WeBControl Layer has been set up using the settings in the following dialogue:

Consider the following policy and select the BEST answer.

Question 18
- (Exam Topic 1)
To optimize Rule Base efficiency, the most hit rules should be where?
To optimize Rule Base efficiency, the most hit rules should be where?
Question 19
- (Exam Topic 2)
Your manager requires you to setup a VPN to a new business partner site. The administrator from the partner site gives you his VPN settings and you notice that he setup AES 128 for IKE phase 1 and AES 256 for IKE phase 2. Why is this a problematic setup?
Your manager requires you to setup a VPN to a new business partner site. The administrator from the partner site gives you his VPN settings and you notice that he setup AES 128 for IKE phase 1 and AES 256 for IKE phase 2. Why is this a problematic setup?
Question 20
- (Exam Topic 4)
Which Threat Prevention Profile is not included by default in R80 Management?
Which Threat Prevention Profile is not included by default in R80 Management?
Question 21
- (Exam Topic 2)
Can a Check Point gateway translate both source IP address and destination IP address in a given packet?
Can a Check Point gateway translate both source IP address and destination IP address in a given packet?
Question 22
- (Exam Topic 1)
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
Question 23
- (Exam Topic 3)
What is the benefit of Manual NAT over Automatic NAT?
What is the benefit of Manual NAT over Automatic NAT?
