19 July, 2021
All About High Value 200-201 Practice Question
It is more faster and easier to pass the Cisco 200-201 exam by using Vivid Cisco Understanding Cisco Cybersecurity Operations Fundamentals questuins and answers. Immediate access to the Abreast of the times 200-201 Exam and find the same core area 200-201 questions with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for Cisco 200-201 Exam Dumps Below:
Question 1
Which process is used when IPS events are removed to improve data integrity?
Question 2
What is the difference between statistical detection and rule-based detection models?
Question 3
How is attacking a vulnerability categorized?
Question 4
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Question 5
What does cyber attribution identity in an investigation?
Question 6
Which two elements are used for profiling a network? (Choose two.)
Question 7
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
Which kind of evidence is this IP address?
Question 8
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Question 9
Drag and drop the access control models from the left onto the correct descriptions on the right.
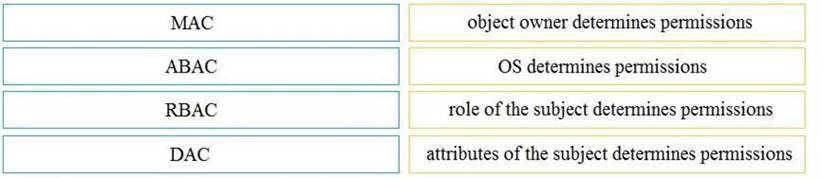
Solution:
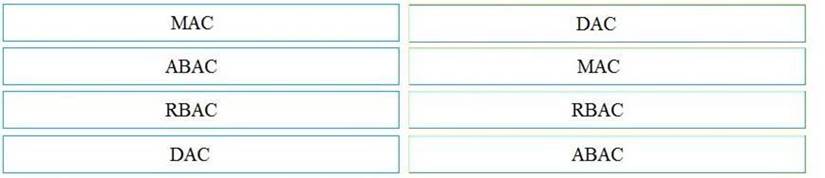
Does this meet the goal?

Solution:

Does this meet the goal?
Question 10
Which signature impacts network traffic by causing legitimate traffic to be blocked?
Question 11
Which piece of information is needed for attribution in an investigation?
Question 12
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
Question 13
Which artifact is used to uniquely identify a detected file?
Question 14
What does an attacker use to determine which network ports are listening on a potential target device?
Question 15
Which event artifact is used to identify HTTP GET requests for a specific file?
Question 16
Which evasion technique is a function of ransomware?
Question 17
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Question 18
What is personally identifiable information that must be safeguarded from unauthorized access?
