10 October, 2020
All About Refined 300-430 Training
It is more faster and easier to pass the Cisco 300-430 exam by using Best Quality Cisco Implementing Cisco Enterprise Wireless Networks (ENWLSI) questuins and answers. Immediate access to the Renew 300-430 Exam and find the same core area 300-430 questions with professionally verified answers, then PASS your exam with a high score now.
Check 300-430 free dumps before getting the full version:
Question 1
Refer to the exhibit.
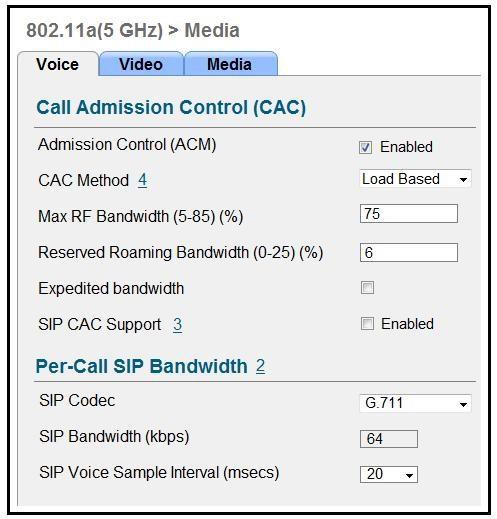
Which two items must be supported on the VoWLAN phones to take full advantage of this WLAN configuration? (Choose two.)

Which two items must be supported on the VoWLAN phones to take full advantage of this WLAN configuration? (Choose two.)
Question 2
When using a Cisco Catalyst 9800 Series Wireless Controller, which statement about AutoQoS is true?
Question 3
Where is a Cisco OEAP enabled on a Cisco Catalyst 9800 Series Wireless Controller?
Question 4
What is the default NMSP echo interval between Cisco MSE and a Wireless LAN Controller?
Question 5
An engineer completed the basic installation for two Cisco CMX servers and is in the process of configuring high availability, but it fails. Which two statements about the root of the issue are true? (Choose two.)
Question 6
An engineer must implement rogue containment for an SSID. What is the maximum number of APs that should be used for containment?
Question 7
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
Question 8
During the EAP process and specifically related to the client authentication session, which encrypted key is sent from the RADIUS server to the access point?
Question 9
A customer is experiencing performance issues with its wireless network and asks a wireless engineer to provide information about all sources of interference and their impacts to the wireless network over the past few days. Where can the requested information be accessed?
Question 10
A network engineer observes a spike in controller CPU overhead and overall network utilization after multicast is enabled on a controller with 500 APs. Which feature connects the issue?
Question 11
What is the default IEEE 802.1x AP authentication configuration on a Cisco Catalyst 9800 Series Wireless Controller?
Question 12
An engineer configured a Cisco AireOS controller with two TACACS+ servers. The engineer notices that when the primary TACACS+ server fails, the WLC starts using the secondary server as expected, but the WLC does not use the primary server again until the secondary server fails or the controller is rebooted. Which cause of this issue is true?
Question 13
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
Question 14
Where is Cisco Hyperlocation enabled on a Cisco Catalyst 9800 Series Wireless Controller web interface?
Question 15
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
Question 16
Which devices can be tracked with the Cisco Context Aware Services?
Question 17
Branch wireless users report that they can no longer access services from head office but can access services locally at the site. New wireless users can associate to the wireless while the WAN is down. Which three elements (Cisco FlexConnect state, operation mode, and authentication method) are seen in this scenario? (Choose three.)
Question 18
For security purposes, an engineer enables CPU ACL and chooses an ACL on the Security > Access Control Lists > CPU Access Control Lists menu. Which kind of traffic does this change apply to, as soon as the change is made?
Question 19
A new MSE with wIPS service has been installed and no alarm information appears to be reaching the MSE from controllers. Which protocol must be allowed to reach the MSE from the controllers?
Question 20
Which two protocols are used to communicate between the Cisco MSE and the Cisco Prime Infrastructure network management software? (Choose two.)
Question 21
Which two events are outcomes of a successful RF jamming attack? (Choose two.)
Question 22
An engineer is performing a Cisco Hyperlocation accuracy test and executes the cmxloc start command on Cisco CMX. Which two parameters are relevant? (Choose two.)
Question 23
Refer to the exhibit. A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations?
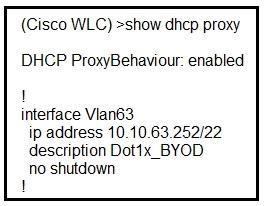

Question 24
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
