14 February, 2022
Avant-garde Microsoft 365 Security Administrator MS-500 Preparation Exams
It is impossible to pass Microsoft MS-500 exam without any help in the short term. Come to Certleader soon and find the most advanced, correct and guaranteed Microsoft MS-500 practice questions. You will get a surprising result by our Updated Microsoft 365 Security Administrator practice guides.
Free demo questions for Microsoft MS-500 Exam Dumps Below:
Question 1
HOTSPOT
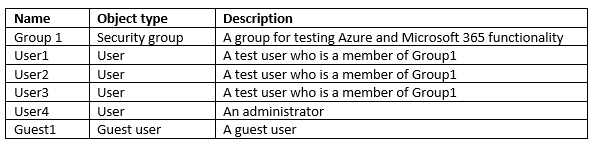
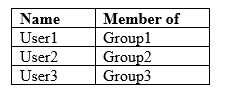
Your company has a Microsoft 365 subscription that contains the users shown in the following table.
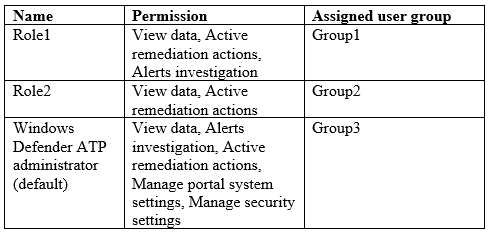
The company implements Windows Defender Advanced Threat Protection (Windows Defender ATP). Windows Defender ATP includes the roles shown in the following table:
Windows Defender ATP contains the machine groups shown in the following table:
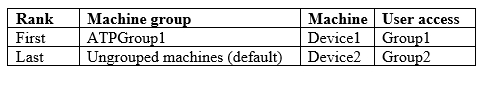
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Solution:
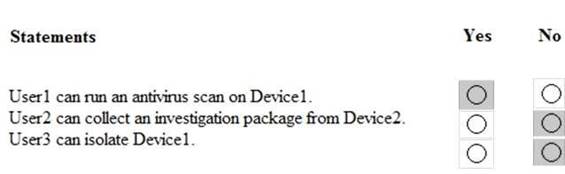
Does this meet the goal?
Your company has a Microsoft 365 subscription that contains the users shown in the following table.

The company implements Windows Defender Advanced Threat Protection (Windows Defender ATP). Windows Defender ATP includes the roles shown in the following table:

Windows Defender ATP contains the machine groups shown in the following table:

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 2
You have a Microsoft 365 subscription.
You need to ensure that users can manually designate which content will be subject to data loss prevention (DLP) policies.
What should you create first?
You need to ensure that users can manually designate which content will be subject to data loss prevention (DLP) policies.
What should you create first?
Question 3
Your company has 500 computers.
You plan to protect the computers by using Windows Defender Advanced Threat Protection (Windows
Defender ATP). Twenty of the computers belong to company executives.
You need to recommend a remediation solution that meets the following requirements: Windows Defender ATP administrators must manually approve all remediation for the executives
Remediation must occur automatically for all other users
What should you recommend doing from Windows Defender Security Center?
You plan to protect the computers by using Windows Defender Advanced Threat Protection (Windows
Defender ATP). Twenty of the computers belong to company executives.
You need to recommend a remediation solution that meets the following requirements: Windows Defender ATP administrators must manually approve all remediation for the executives
Remediation must occur automatically for all other users
What should you recommend doing from Windows Defender Security Center?
Question 4
An administrator configures Azure AD Privileged Identity Management as shown in the following exhibit.
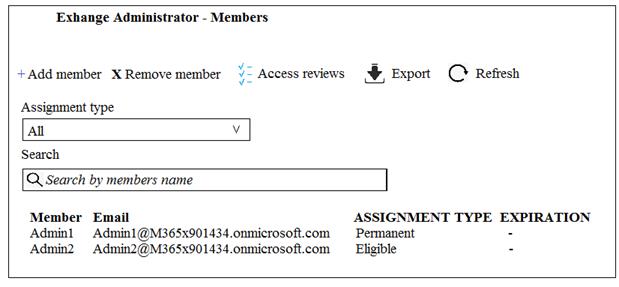
What should you do to meet the security requirements?

What should you do to meet the security requirements?
Question 5
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled $true-AdminAuditLogCmdlets *Mailbox* command. Does that meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled $true-AdminAuditLogCmdlets *Mailbox* command. Does that meet the goal?
Question 6
You have a Microsoft 365 subscription.
You create and run a content search from the Security & Compliance admin center. You need to download the results of the content search.
What should you obtain first?
You create and run a content search from the Security & Compliance admin center. You need to download the results of the content search.
What should you obtain first?
Question 7
HOTSPOT
You have a Microsoft 365 subscription that include three users named User1, User2, and User3.
A file named File1.docx is stored in Microsoft OneDrive. An automated process updates File1.docx every minute.
You create an alert policy named Policy1 as shown in the following exhibit.
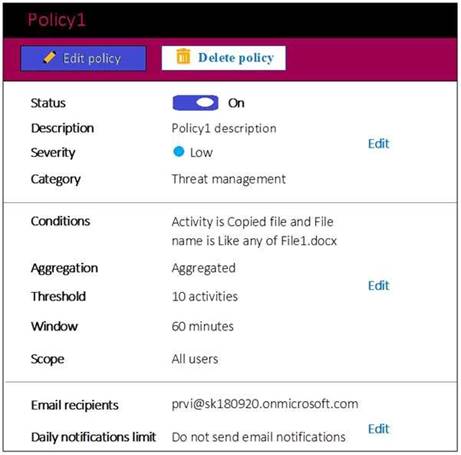
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Solution:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/alert-policies
Does this meet the goal?
You have a Microsoft 365 subscription that include three users named User1, User2, and User3.
A file named File1.docx is stored in Microsoft OneDrive. An automated process updates File1.docx every minute.
You create an alert policy named Policy1 as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Solution:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/alert-policies
Does this meet the goal?
Question 8
You need to meet the technical requirements for User9. What should you do?
Question 9
You need to recommend a solution that meets the technical and security requirements for sharing data with the partners.
What should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
What should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Question 10
HOTSPOT
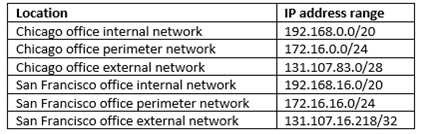
Your company has a Microsoft 365 subscription, a Microsoft Azure subscription, and an Azure Active Directory (Azure AD) tenant named contoso.com.
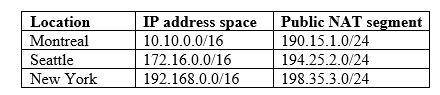
The company has the offices shown in the following table.
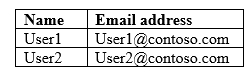
The tenant contains the users shown in the following table.
You create the Microsoft Cloud App Security policy shown in the following exhibit.
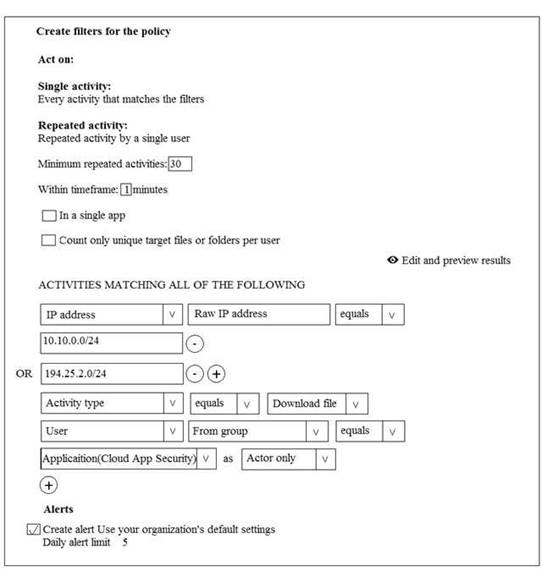
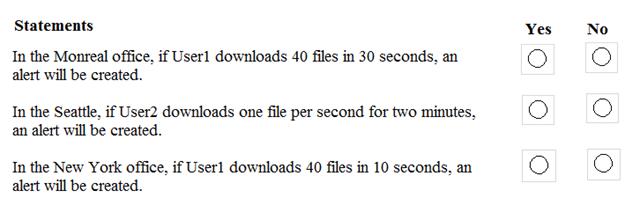
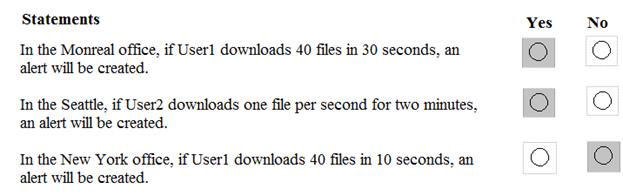
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Solution:
Does this meet the goal?
Your company has a Microsoft 365 subscription, a Microsoft Azure subscription, and an Azure Active Directory (Azure AD) tenant named contoso.com.
The company has the offices shown in the following table.

The tenant contains the users shown in the following table.

You create the Microsoft Cloud App Security policy shown in the following exhibit.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 11
Your company has a Microsoft 365 subscription that includes a user named User1.
You suspect that User1 sent email messages to a competitor detailing company secrets.
You need to recommend a solution to ensure that you can review any email messages sent by User1 to the competitor, including sent items that were deleted.
What should you include in the recommendation?
You suspect that User1 sent email messages to a competitor detailing company secrets.
You need to recommend a solution to ensure that you can review any email messages sent by User1 to the competitor, including sent items that were deleted.
What should you include in the recommendation?
Question 12
You have a Microsoft 365 subscription that includes a user named Admin1.
You need to ensure that Admin1 can preserve all the mailbox content of users, including their deleted items.
The solution must use the principle of least privilege. What should you do?
You need to ensure that Admin1 can preserve all the mailbox content of users, including their deleted items.
The solution must use the principle of least privilege. What should you do?
Question 13
What should User6 use to meet the technical requirements?
Question 14
DRAG DROP
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
You create a Windows Defender machine group named MachineGroupl.
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
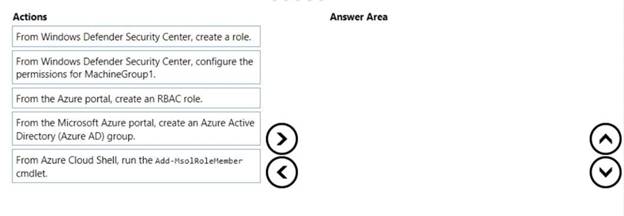
Solution:
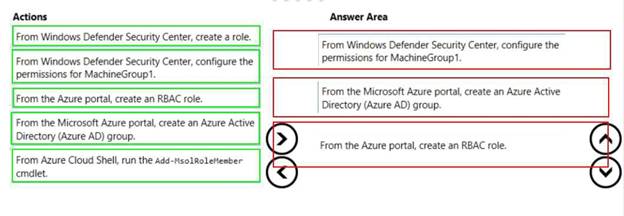
Does this meet the goal?
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
You create a Windows Defender machine group named MachineGroupl.
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Solution:

Does this meet the goal?
Question 15
You have a Microsoft 365 subscription.
You need to be notified by email whenever an administrator starts an eDiscovery search. What should you do from the Security & Compliance admin center?
You need to be notified by email whenever an administrator starts an eDiscovery search. What should you do from the Security & Compliance admin center?
Question 16
You configure several Advanced Threat Protection (ATP) policies in a Microsoft 365 subscription. You need to allow a user named User1 to view ATP reports in the Threat management dashboard. Which role provides User1with the required role permissions?
Question 17
You need to recommend a solution for the user administrators that meets the security requirements for auditing.
Which blade should you recommend using from the Azure Active Directory admin center?
Which blade should you recommend using from the Azure Active Directory admin center?
Question 18
You need to resolve the issue that targets the automated email messages to the IT team. Which tool should you run first?