16 October, 2019
Check Point Certified Security Administrator – GAiA 156-215.77 Braindumps
Want to know ccsa 156 215.77 features? Want to lear more about exam 156 215.77 experience? Study 156 215.77 pdf. Gat a success with an absolute guarantee to pass Check-Point 156-215.77 (Check Point Certified Security Administrator – GAiA) test on your first attempt.
Free demo questions for Check-Point 156-215.77 Exam Dumps Below:
Question 1
Which Client Authentication sign-on method requires the user to first authenticate via the User Authentication mechanism, when logging in to a remote server with Telnet?
Question 2
Select the TRUE statements about the Rule Base shown? Exhibit:
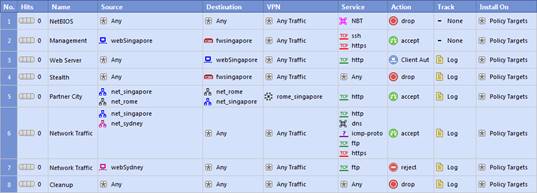
1) HTTP traffic from webrome to websingapore will be encrypted.
2) HTTP traffic from websingapore to webrome will be encrypted.
3) HTTP traffic from webrome to websingapore will be authenticated.
4) HTTP traffic from websingapore to webrome will be blocked.

1) HTTP traffic from webrome to websingapore will be encrypted.
2) HTTP traffic from websingapore to webrome will be encrypted.
3) HTTP traffic from webrome to websingapore will be authenticated.
4) HTTP traffic from websingapore to webrome will be blocked.
Question 3
Which rule position in the Rule Base should hold the Cleanup Rule? Why?
Question 4
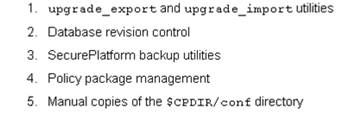
You plan to create a backup of the rules, objects, policies, and global properties from an R77 Security Management Server. Which of the following backup and restore solutions can you use?

Question 5
Static NAT connections, by default, translate on which firewall kernel inspection point?
Question 6
What happens when you select File
Question 7
How can you configure an application to automatically launch on the Security Management Server when traffic is dropped or accepted by a rule in the Security Policy?
Question 8
Which of these Security Policy changes optimize Security Gateway performance?
Question 9
Which of the following is true of the Cleanup rule?
Question 10
What CANNOT be configured for existing connections during a policy install?
Question 11
Your perimeter Security Gateway’s external IP is 200.200.200.3. Your network diagram shows:
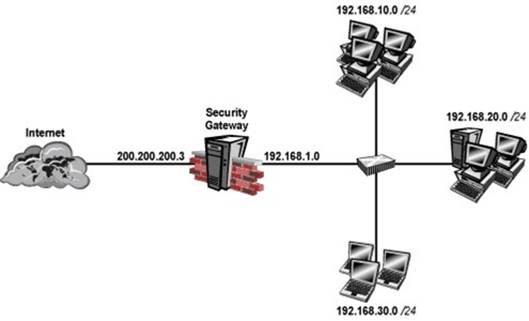
Required. Allow only network 192.168.10.0 and 192.168.20.0 to go out to the Internet, using 200.200.200.5.
The local network 192.168.1.0/24 needs to use 200.200.200.3 to go out to the Internet. Assuming you enable all the settings in the NAT page of Global Properties, how could you
achieve these requirements?

Required. Allow only network 192.168.10.0 and 192.168.20.0 to go out to the Internet, using 200.200.200.5.
The local network 192.168.1.0/24 needs to use 200.200.200.3 to go out to the Internet. Assuming you enable all the settings in the NAT page of Global Properties, how could you
achieve these requirements?
Question 12
Which SmartView Tracker selection would most effectively show who installed a Security Policy blocking all traffic from the corporate network?
Question 13
Which command line interface utility allows the administrator to verify the Security Policy name and timestamp currently installed on a firewall module?
Question 14
A rule is used to prevent all traffic going to the R77 Security Gateway.
Question 15
What command syntax would you use to turn on PDP logging in a distributed environment?
Question 16
SmartView Tracker R77 consists of three different modes. They are:
Question 17
What happens if the identity of a user is known?
Question 18
An internal host initiates a session to the Google.com website and is set for Hide NAT behind the Security Gateway. The initiating traffic is an example of .
Question 19
Which of the following is an authentication method used by Identity Awareness?
Question 20
Which of the following is NOT a valid option when configuring access for Captive Portal?
Question 21
When configuring LDAP authentication, which of the following items should be configured for the Security Management Server?
Question 22
Match the following commands to their correct function. Each command has one function only listed.
Exhibit:
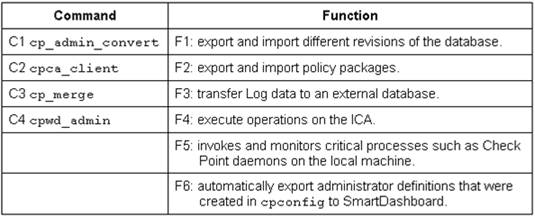
Exhibit:

Question 23
Which SmartConsole component can Administrators use to track changes to the Rule Base?
Question 24
Which command enables IP forwarding on IPSO?
Question 25
Which statement is TRUE about implicit rules?
Question 26
One of your remote Security Gateways suddenly stops sending logs, and you cannot install the Security Policy on the Gateway. All other remote Security Gateways are logging normally to the Security Management Server, and Policy installation is not affected. When you click the Test SIC status button in the problematic Gateway object, you receive an error message. What is the problem?
Question 27
How can you most quickly reset Secure Internal Communications (SIC) between a Security Management Server and Security Gateway?
Question 28
Which of the following items should be configured for the Security Management Server to authenticate via LDAP?
Question 29
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities should you do first?
