22 July, 2021
Down To Date 200-201 Question For Understanding Cisco Cybersecurity Operations Fundamentals Certification
Want to know Pass4sure 200-201 Exam practice test features? Want to lear more about Cisco Understanding Cisco Cybersecurity Operations Fundamentals certification experience? Study 100% Correct Cisco 200-201 answers to Regenerate 200-201 questions at Pass4sure. Gat a success with an absolute guarantee to pass Cisco 200-201 (Understanding Cisco Cybersecurity Operations Fundamentals) test on your first attempt.
Free 200-201 Demo Online For Cisco Certifitcation:
Question 1
Drag and drop the security concept on the left onto the example of that concept on the right.
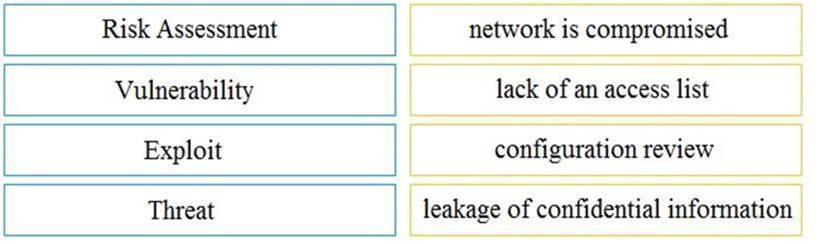
Solution:

Does this meet the goal?

Solution:

Does this meet the goal?
Question 2
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
Question 3
Refer to the exhibit.
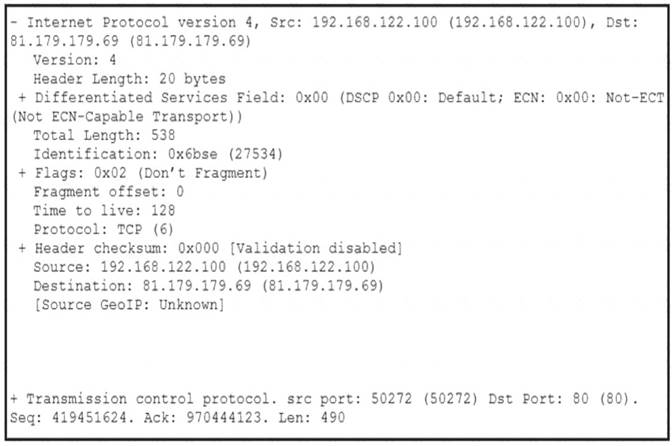
What should be interpreted from this packet capture?

What should be interpreted from this packet capture?
Question 4
What makes HTTPS traffic difficult to monitor?
Question 5
Refer to the exhibit.

In which Linux log file is this output found?

In which Linux log file is this output found?
Question 6
What is a difference between inline traffic interrogation and traffic mirroring?
Question 7
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
Question 8
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
Which technology makes this behavior possible?
Question 9
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
Question 10
Refer to the exhibit.
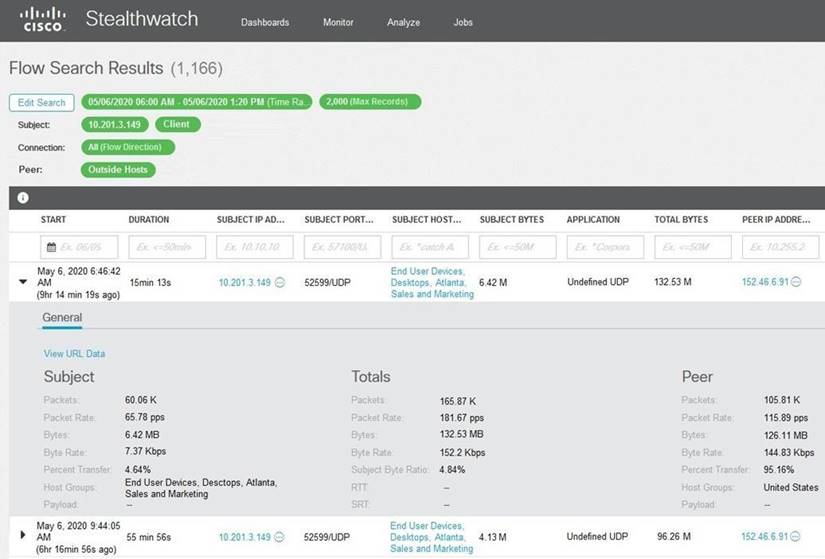
What is the potential threat identified in this Stealthwatch dashboard?

What is the potential threat identified in this Stealthwatch dashboard?
Question 11
What is a benefit of agent-based protection when compared to agentless protection?
Question 12
Refer to the exhibit.
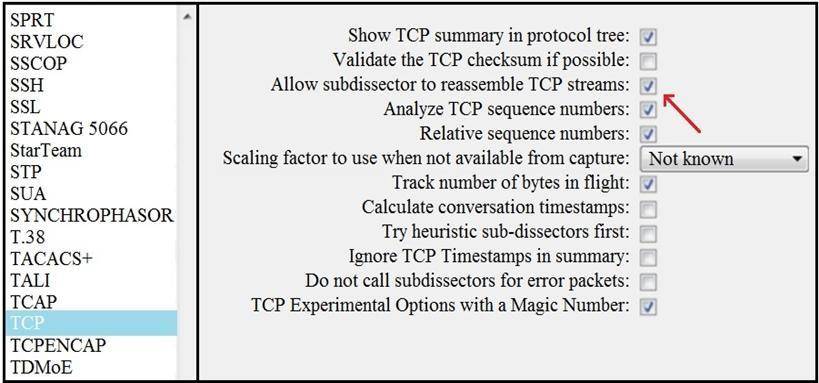
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?

What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Question 13
What is the difference between an attack vector and attack surface?
Question 14
Which action prevents buffer overflow attacks?
Question 15
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
Question 16
Refer to the exhibit.
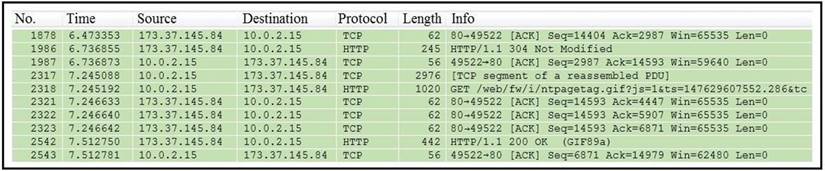
Which packet contains a file that is extractable within Wireshark?

Which packet contains a file that is extractable within Wireshark?
Question 17
What is the difference between deep packet inspection and stateful inspection?
Question 18
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
