12 August, 2021
How Many Questions Of 156-215.80 Questions
Cause all that matters here is passing the Check-Point 156-215.80 exam. Cause all that you need is a high score of 156-215.80 Check Point Certified Security Administrator exam. The only one thing you need to do is downloading Pass4sure 156-215.80 exam study guides now. We will not let you down with our money-back guarantee.
Online 156-215.80 free questions and answers of New Version:
Question 1
- (Exam Topic 2)
Which command is used to obtain the configuration lock in Gaia?
Which command is used to obtain the configuration lock in Gaia?
Question 2
- (Exam Topic 4)
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
Question 3
- (Exam Topic 2)
Message digests use which of the following?
Message digests use which of the following?
Question 4
- (Exam Topic 2)
Choose what BEST describes a Session.
Choose what BEST describes a Session.
Question 5
- (Exam Topic 3)
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities sh you do first?
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities sh you do first?
Question 6
- (Exam Topic 1)
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point products protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point products protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
Question 7
- (Exam Topic 4)
Fill in the blank: Authentication rules are defined for ____ .
Fill in the blank: Authentication rules are defined for ____ .
Question 8
- (Exam Topic 1)
Fill in the blank: To build an effective Security Policy, use a _____ and _____ rule.
Fill in the blank: To build an effective Security Policy, use a _____ and _____ rule.
Question 9
- (Exam Topic 2)
Where do we need to reset the SIC on a gateway object?
Where do we need to reset the SIC on a gateway object?
Question 10
- (Exam Topic 4)
Which of the following is NOT a component of Check Point Capsule?
Which of the following is NOT a component of Check Point Capsule?
Question 11
- (Exam Topic 4)
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
Question 12
- (Exam Topic 1)
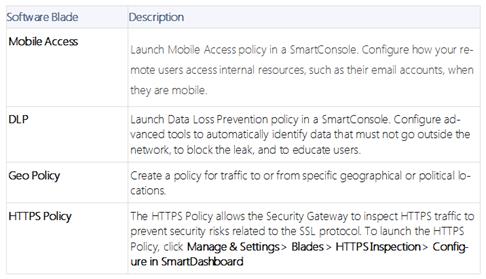
DLP and Geo Policy are examples of what type of Policy?
DLP and Geo Policy are examples of what type of Policy?
Question 13
- (Exam Topic 2)
Fill in the blank: Once a license is activated, a ____ should be installed.
Fill in the blank: Once a license is activated, a ____ should be installed.
Question 14
- (Exam Topic 1)
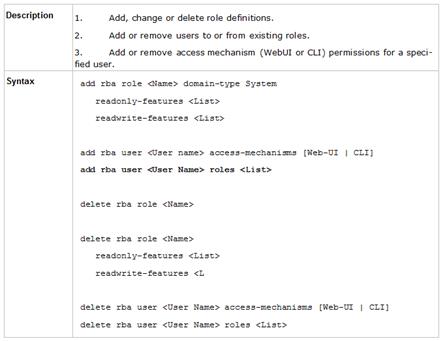
Which command is used to add users to or from existing roles?
Which command is used to add users to or from existing roles?
Question 15
- (Exam Topic 2)
Fill in the blank: A ____ is used by a VPN gateway to send traffic as if it were a physical interface.
Fill in the blank: A ____ is used by a VPN gateway to send traffic as if it were a physical interface.
Question 16
- (Exam Topic 1)
Fill in the blank: With the User Directory Software Blade, you can create R80 user definitions on a(an) ______ Server.
Fill in the blank: With the User Directory Software Blade, you can create R80 user definitions on a(an) ______ Server.
Question 17
- (Exam Topic 1)
Which of the following ClusterXL modes uses a non-unicast MAC address for the cluster IP address?
Which of the following ClusterXL modes uses a non-unicast MAC address for the cluster IP address?
Question 18
- (Exam Topic 4)
What is the SOLR database for?
What is the SOLR database for?
Question 19
- (Exam Topic 3)
What component of R80 Management is used for indexing?
What component of R80 Management is used for indexing?
Question 20
- (Exam Topic 1)
You are the administrator for ABC Corp. You have logged into your R80 Management server. You are making some changes in the Rule Base and notice that rule No.6 has a pencil icon next to it.

What does this mean?
You are the administrator for ABC Corp. You have logged into your R80 Management server. You are making some changes in the Rule Base and notice that rule No.6 has a pencil icon next to it.

What does this mean?
Question 21
- (Exam Topic 2)
Choose the SmartLog property that is TRUE.
Choose the SmartLog property that is TRUE.
Question 22
- (Exam Topic 3)
What port is used for communication to the User Center with SmartUpdate?
What port is used for communication to the User Center with SmartUpdate?
Question 23
- (Exam Topic 1)
Which of the following is TRUE regarding Gaia command line?
Which of the following is TRUE regarding Gaia command line?