30 December, 2020
How Many Questions Of 1Z0-821 Exam Price
Cause all that matters here is passing the Oracle 1Z0-821 exam. Cause all that you need is a high score of 1Z0-821 Oracle Solaris 11 System Administrator exam. The only one thing you need to do is downloading Examcollection 1Z0-821 exam study guides now. We will not let you down with our money-back guarantee.
Check 1Z0-821 free dumps before getting the full version:
Question 1
Which two accurately identify features of a Solaris 10 branded zone?
Question 2
You are using AI to install a new system. You have added to following information to the AI manifest:
source = “http://sysA.example.com/zone_cfg/zone.cfg”/> Which statement is true with regard to the zone.cfg?
Question 3
You upgraded your server to Oracle Solaris 11 and you imported zpool (pool1) that was created in Solaris 10. You need to create an encrypted ZFS file system in pool1, but first you need to make sure that your server supports ZFS encryption.
Which four statements are true for support of ZFS encryption?
Which four statements are true for support of ZFS encryption?
Question 4
You are installing the Solaris 11 Operation System by using the Text Installer. A panel
prompts you to create a root password and a user account.
Which four describe your options for completing this panel of the Installation?
prompts you to create a root password and a user account.
Which four describe your options for completing this panel of the Installation?
Question 5
A user jack, using a korn shell, requests a directory listing as follows:
jack@solaris:/export/home/jack $ 1s File filea Filea fileb Fileb filec Filec
Which two statements are correct?
jack@solaris:/export/home/jack $ 1s File filea Filea fileb Fileb filec Filec
Which two statements are correct?
Question 6
View the Exhibit.
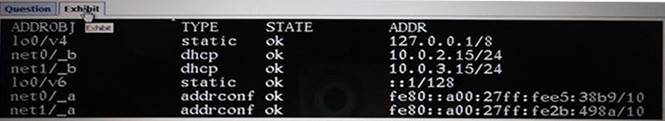
After Installing the OS, you need to verify the network interface information. Which command was used to display the network interface information in the exhibit?

After Installing the OS, you need to verify the network interface information. Which command was used to display the network interface information in the exhibit?
Question 7
You display the IP interface information with ipmpstat -i.
Which two characteristics are indicated by characters that may be included in the FLAGS column?
Which two characteristics are indicated by characters that may be included in the FLAGS column?
Question 8
The /usr/bin/p7zip file that is part of the p7zip package has been overwritten. This server is critical to production and cannot be rebooted. Identify the command that would restore the file without requiring a reboot.
Question 9
You have a ZFS file system named /dbase/oral and you want to guarantee that 10 GB of storage space is available to that dataset for all data, snapshots, and clones.
Which option would you choose?
Which option would you choose?
Question 10
You want to deploy Oracle Solaris 11 with the Automated Installer (AI). You need to make sure that your server and network meet the requirements for using AI.
Identify two requirements for using AI.
Identify two requirements for using AI.
Question 11
Which operation will fail if the DNS configuration is incorrect?
Question 12
You are installing the Oracle Solaris 11 Operating System by using the Text Installer. Which two options describe the features associated with the Text Installer?
Question 13
The core dump configuration for your system is:
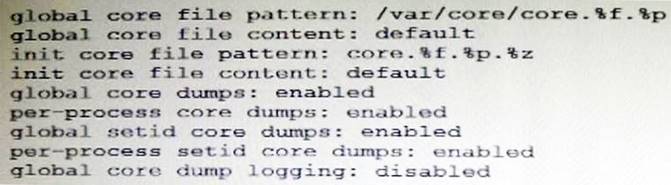
A user is running a process in the global zone and the process crashes. The process information is:
User1 2663 2618 0 17:46:42 pts/2 0:00 /usr/bin/bash
The server host name is: zeus
What will the per-process core file be named?

A user is running a process in the global zone and the process crashes. The process information is:
User1 2663 2618 0 17:46:42 pts/2 0:00 /usr/bin/bash
The server host name is: zeus
What will the per-process core file be named?
Question 14
The advantage of core tiles is that they allow you an opportunity to examine the cause of problems, so that they can be resolved.
However, core files must be managed because they .
However, core files must be managed because they .
Question 15
Which two SMF milestones can be specified at boot time?
Question 16
You are the administrator of a system that a large number of developers work on. These developers crash the system, and their applications, on a regular basis.
What command would you use to configure where the core files are saved?
What command would you use to configure where the core files are saved?
Question 17
Which two options are accurate regarding the non-global zone console?
Question 18
Subnets are created by using .
Question 19
A user jack, using a bash shell, requests a directory listing as follows:
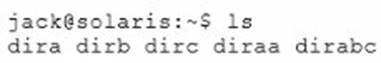
Which three statements are correct?
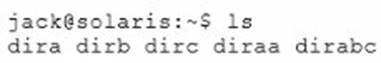
Which three statements are correct?
Question 20
Review the non-global zone configuration displayed below:
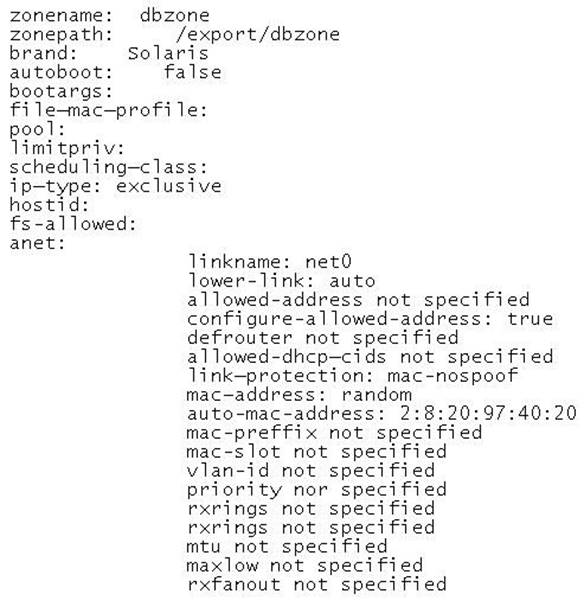
The global zone has 1024 MB of physical memory. You need to limit the non-global zone so that it uses no more than 500 MB of the global zone's physical memory. Which option would you choose?
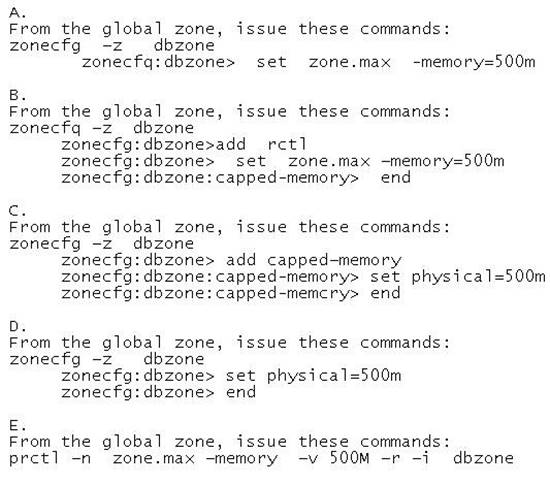

The global zone has 1024 MB of physical memory. You need to limit the non-global zone so that it uses no more than 500 MB of the global zone's physical memory. Which option would you choose?

