17 October, 2020
How Many Questions Of NSE8_810 Preparation
Cause all that matters here is passing the Fortinet NSE8_810 exam. Cause all that you need is a high score of NSE8_810 Fortinet Network Security Expert 8 Written Exam (810) exam. The only one thing you need to do is downloading Exambible NSE8_810 exam study guides now. We will not let you down with our money-back guarantee.
Fortinet NSE8_810 Free Dumps Questions Online, Read and Test Now.
Question 1
Exhibit
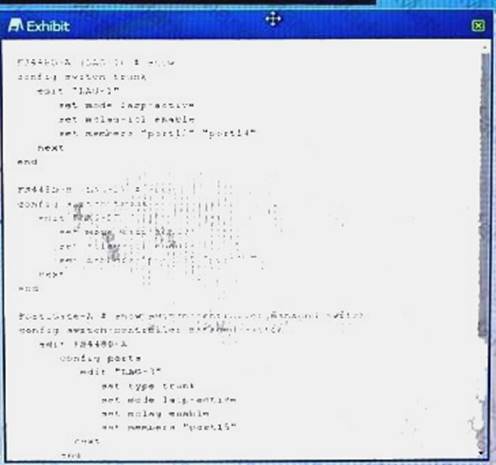
Referring to the exhibit, which two statements are true? (Choose two.)

Referring to the exhibit, which two statements are true? (Choose two.)
Question 2
Exhibit
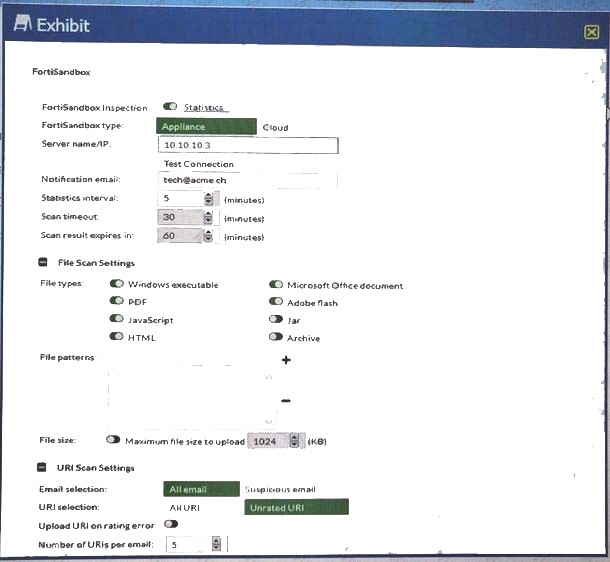
You have installed a FortiSandbox and configured it in your FortiMail. Referring to the exhibit, which two statements are correct? (Choose two.)

You have installed a FortiSandbox and configured it in your FortiMail. Referring to the exhibit, which two statements are correct? (Choose two.)
Question 3
Exhibit

What are two ways to establish communication between an existing NAT VDOM and a new transparent VDOM? (Choose two.)

What are two ways to establish communication between an existing NAT VDOM and a new transparent VDOM? (Choose two.)
Question 4
Exhibit
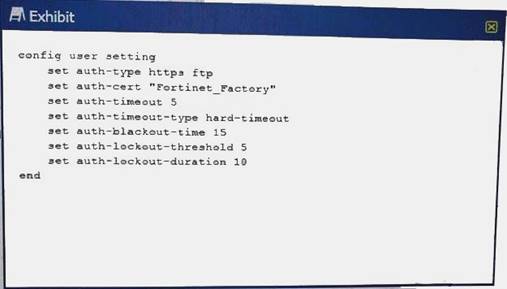
Referring to the exhibit, which two statements are true about local authentication? (Choose two.)

Referring to the exhibit, which two statements are true about local authentication? (Choose two.)
Question 5
A FortOS devices is used for termination of VPNs for number of remote spoke VPN units (designated group A spokes) using a phase 1 main mode dial-up tunnel using pre-shared. Your company recently acquired another organization. You are asked establish VPN correctively for the newly acquired organization's sites which new devices will be provisioned (designated Group B spokes). Both exiting (Group A) and new (Group B) spoke units are dynamically addressed. You are asked to ensure that spokes from the acquired organization (Group B) have different access permission than your existing VPN spokes (Group A).
Which two solutions meet the represents for the new spoke group? (Choose two.)
Which two solutions meet the represents for the new spoke group? (Choose two.)
Question 6
Exhibit

The exhibit shows the steps for creating a URL rewrite policy on a FortWet-Which statement represents the purpose of this policy?

The exhibit shows the steps for creating a URL rewrite policy on a FortWet-Which statement represents the purpose of this policy?
Question 7
Exhibit

You need to apply the security feature below to the network shown in the exhibit.
-- high grade DDoS protection
-- Web security and load balacng for Server 1 and Server
-- Solution must be PCI DSS compliant'
-- enhanced security to DNS 1 and DNS 2 What are three solutio for the scenario?

You need to apply the security feature below to the network shown in the exhibit.
-- high grade DDoS protection
-- Web security and load balacng for Server 1 and Server
-- Solution must be PCI DSS compliant'
-- enhanced security to DNS 1 and DNS 2 What are three solutio for the scenario?
Question 8
Exhibit

You ate trying to configure Link-Aggregation Group (LAG), but ports A and B do not appear on the list of member options. Referring to the exhibit, which statement is correct in this situation?

You ate trying to configure Link-Aggregation Group (LAG), but ports A and B do not appear on the list of member options. Referring to the exhibit, which statement is correct in this situation?
Question 9
You want to manage a FortiCloud service. The FortiGate shows up in your list devices on the FortiCloud Web site, but all management functions are either missing or grayed out.
Which statement a correct in this scenario?
Which statement a correct in this scenario?
Question 10
You have a customer experiencing problem with a legacy L3L4 firewall device and IPV6 SIP VoIP traffic. They devices is dropping SIP packets, consequently, it process SIP voice calls. Which solution would solve the customer's problem?
Question 11
Exhibit

You have configured an HA cluster with Two FortiGates You want to make sore that you are able to manage the individual duster members using ports3.
Referring to the exhibit, what are two ways to accomplish this task? (Choose two.)

You have configured an HA cluster with Two FortiGates You want to make sore that you are able to manage the individual duster members using ports3.
Referring to the exhibit, what are two ways to accomplish this task? (Choose two.)
Question 12
Exhibit

The exhibit shows a full-mesh topology between Fortigates FortiSwitches. To deploy configuration, two requirements must be met:
-- 20 Gbps full duplex connectivity is available between each FortiGate and the FortiSwitches.
--the FortiGate HA must be in AP mode.
Referring to the exhibit, what are two actions that wil fulfill the requirements?

The exhibit shows a full-mesh topology between Fortigates FortiSwitches. To deploy configuration, two requirements must be met:
-- 20 Gbps full duplex connectivity is available between each FortiGate and the FortiSwitches.
--the FortiGate HA must be in AP mode.
Referring to the exhibit, what are two actions that wil fulfill the requirements?
Question 13
Exhibit
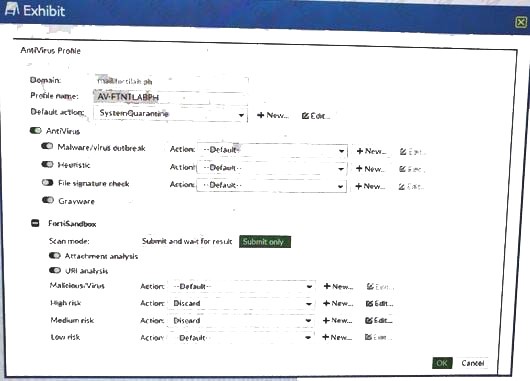
Referring to the exhibit, what will happen if FortiSandbox categorizes an e-mail attachment submitted by FortiMarf as a high risk?

Referring to the exhibit, what will happen if FortiSandbox categorizes an e-mail attachment submitted by FortiMarf as a high risk?
Question 14
Exhibit
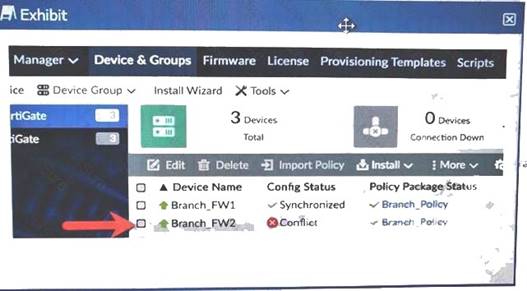
You log into FortiManager, look at the Device Manager window and notice that one of you managed devices is not in normal status.
Referring to the exhibit, which two statements correctly describe the affected device's status and result? (Choose two.)

You log into FortiManager, look at the Device Manager window and notice that one of you managed devices is not in normal status.
Referring to the exhibit, which two statements correctly describe the affected device's status and result? (Choose two.)
Question 15
Exhibit
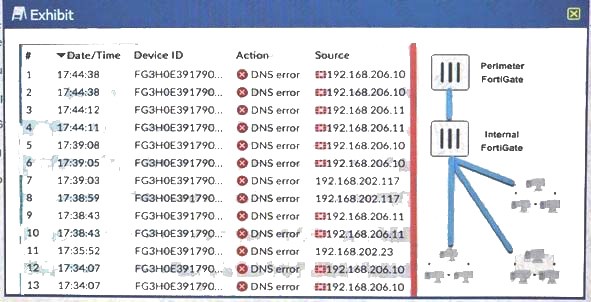
You have deployed several perimeter FortiGates wilh terminal segmentation FortiGates befwid them All ForbGale devices are logging to Fortianaluzer. When you search the logs in FortiAnatyzer (or denied traffic,
you see numerous log messages, as shown in the exhibit, on your perimeter FortiGates only. Which two actions would reduce the number pt these log message? (Choose two)

You have deployed several perimeter FortiGates wilh terminal segmentation FortiGates befwid them All ForbGale devices are logging to Fortianaluzer. When you search the logs in FortiAnatyzer (or denied traffic,
you see numerous log messages, as shown in the exhibit, on your perimeter FortiGates only. Which two actions would reduce the number pt these log message? (Choose two)
Question 16
You cannot the FortiGales default gateway 10.10.10 .1 from the FortiGate CLI. The FortiGate interface facing the default gateway is wan 1 and its IP address 10.10 .10 K74 During the troubleshooting, tests, you confirmed that you can plug other IP addresses in the 10.10.10. 0/24 subnet from the FortiGAte CLI without packets lost.
Which two CLI commands will help you to troubleshoot this problem? (Choose two.)
Which two CLI commands will help you to troubleshoot this problem? (Choose two.)
Question 17
Exhibit

Your organization has a FortrGate cluster that is connected to two independent ISPs. You must configure the FortiGate failover for a single ISP failure to occur without disruption.
Referring to the exhibit, which two FortiGate BGP features would be used to accomplish this task' (Choose two.)

Your organization has a FortrGate cluster that is connected to two independent ISPs. You must configure the FortiGate failover for a single ISP failure to occur without disruption.
Referring to the exhibit, which two FortiGate BGP features would be used to accomplish this task' (Choose two.)
Question 18
Exhibit
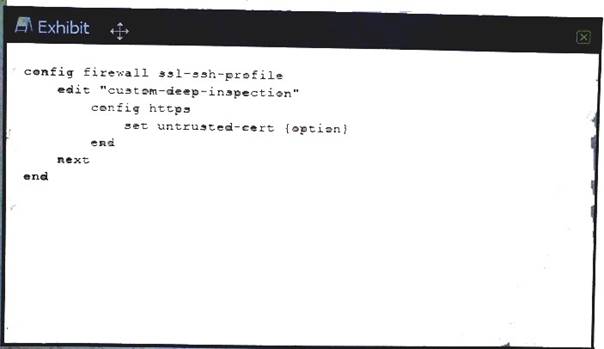
Referring to the exhibit, which command-line option for deep inspection SSL would have the FortiGAte re=sign all untrusted self-signed certificates with the trusted Fortinet_CA_SSl certificate?

Referring to the exhibit, which command-line option for deep inspection SSL would have the FortiGAte re=sign all untrusted self-signed certificates with the trusted Fortinet_CA_SSl certificate?
Question 19
You deploy a FortiGate device in a remote office based on the requirements shown below.
-- Due to company's security policy, management IP of your FortiGate is not allowed to access the Internet.
-- Apply Web Filtering, Antivirus, IPS and Application control to the protected subnet.
-- Be managed by a central FortiManager in the head office. Which action will help to achieve the requirements?
-- Due to company's security policy, management IP of your FortiGate is not allowed to access the Internet.
-- Apply Web Filtering, Antivirus, IPS and Application control to the protected subnet.
-- Be managed by a central FortiManager in the head office. Which action will help to achieve the requirements?
Question 20
Exhibit
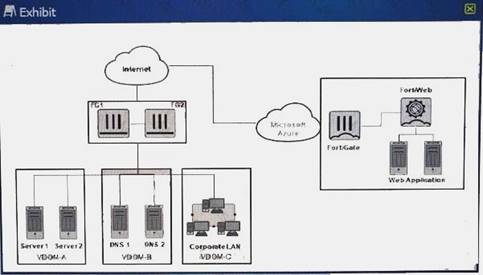
A customer gas just finished their Azure deployment to ensure a Web application behind a FortiWeb. Now they want to add components to protect against advance threats (zero day attacks), centrally the entire environment, and centrally monitor Fortinet and non-Fortinet products.
Which Fortinet will standby these requirements?

A customer gas just finished their Azure deployment to ensure a Web application behind a FortiWeb. Now they want to add components to protect against advance threats (zero day attacks), centrally the entire environment, and centrally monitor Fortinet and non-Fortinet products.
Which Fortinet will standby these requirements?
Question 21
FortiMail configured with the protected domain "internal lab".
Which two envelopes addresses will need an access control rule to relay e-mail sent for unauthenticated users? (Choose two.)
Which two envelopes addresses will need an access control rule to relay e-mail sent for unauthenticated users? (Choose two.)
