25 October, 2023
How Many Questions Of SCS-C01 Actual Exam
It is more faster and easier to pass the Amazon-Web-Services SCS-C01 exam by using Download Amazon-Web-Services AWS Certified Security- Specialty questuins and answers. Immediate access to the Renewal SCS-C01 Exam and find the same core area SCS-C01 questions with professionally verified answers, then PASS your exam with a high score now.
Online Amazon-Web-Services SCS-C01 free dumps demo Below:
Question 1
You are building a large-scale confidential documentation web server on AWSand all of the documentation for it will be stored on S3. One of the requirements is that it cannot be publicly accessible from S3 directly, and you will need to use Cloud Front to accomplish this. Which of the methods listed below would satisfy the requirements as outlined? Choose an answer from the options below
Please select:
Please select:
Question 2
A company wants to have an Intrusion detection system available for their VPC in AWS. They want to have complete control over the system. Which of the following would be ideal to implement?
Please select:
Please select:
Question 3
A Security Administrator has a website hosted in Amazon S3. The Administrator has been given the following requirements:
 Users may not access the website directly by using an Amazon S3 URL.
Users may not access the website directly by using an Amazon S3 URL.
Which configurations will support these requirements? (Choose two.)
 Users may not access the website directly by using an Amazon S3 URL.
Users may not access the website directly by using an Amazon S3 URL.Which configurations will support these requirements? (Choose two.)
Question 4
Development teams in your organization use S3 buckets to store the log files for various applications hosted ir development environments in AWS. The developers want to keep the logs for one month for troubleshooting purposes, and then purge the logs. What feature will enable this requirement?
Please select:
Please select:
Question 5
While securing the connection between a company's VPC and its on-premises data center, a Security Engineer sent a ping command from an on-premises host (IP address 203.0.113.12) to an Amazon EC2 instance (IP address 172.31.16.139). The ping command did not return a response. The flow log in the VPC showed the following:
2 123456789010 eni-1235b8ca 203.0.113.12 172.31.16.139 0 0 1 4 336 1432917027 1432917142 ACCEPT OK
2 123456789010 eni-1235b8ca 172.31.16.139 203.0.113.12 0 0 1 4 336 1432917094 1432917142 REJECT OK
What action should be performed to allow the ping to work?
2 123456789010 eni-1235b8ca 203.0.113.12 172.31.16.139 0 0 1 4 336 1432917027 1432917142 ACCEPT OK
2 123456789010 eni-1235b8ca 172.31.16.139 203.0.113.12 0 0 1 4 336 1432917094 1432917142 REJECT OK
What action should be performed to allow the ping to work?
Question 6
You currently have an S3 bucket hosted in an AWS Account. It holds information that needs be accessed by a partner account. Which is the MOST secure way to allow the partner account to access the S3 bucket in your account? Select 3 options.
Please select:
Please select:
Question 7
Amazon CloudWatch Logs agent is successfully delivering logs to the CloudWatch Logs service. However, logs stop being delivered after the associated log stream has been active for a specific number of hours.
What steps are necessary to identify the cause of this phenomenon? (Choose two.)
What steps are necessary to identify the cause of this phenomenon? (Choose two.)
Question 8
A Security Engineer is working with the development team to design a supply chain application that stores sensitive inventory data in an Amazon S3 bucket. The application will use an AWS KMS customer master key (CMK) to encrypt the data on Amazon S3. The inventory data on Amazon S3 will be shared of vendors. All vendors will use AWS principals from their own AWS accounts to access the data on Amazon S3. The vendor list may change weekly, and the solution must support cross-account access.
What is the MOST efficient way to manage access control for the KMS CMK7?
What is the MOST efficient way to manage access control for the KMS CMK7?
Question 9
A company will store sensitive documents in three Amazon S3 buckets based on a data classification scheme of “Sensitive,” “Confidential,” and “Restricted.” The security solution must meet all of the following requirements:
 Each object must be encrypted using a unique key.
Each object must be encrypted using a unique key.
 AWS KMS must automatically rotate encryption keys annually.
AWS KMS must automatically rotate encryption keys annually.
Which of the following meets these requirements?
 Each object must be encrypted using a unique key.
Each object must be encrypted using a unique key. AWS KMS must automatically rotate encryption keys annually.
AWS KMS must automatically rotate encryption keys annually.Which of the following meets these requirements?
Question 10
The Security Engineer has discovered that a new application that deals with highly sensitive data is storing Amazon S3 objects with the following key pattern, which itself contains highly sensitive data.
Pattern: "randomID_datestamp_PII.csv" Example:
"1234567_12302017_000-00-0000 csv"
The bucket where these objects are being stored is using server-side encryption (SSE). Which solution is the most secure and cost-effective option to protect the sensitive data?
Pattern: "randomID_datestamp_PII.csv" Example:
"1234567_12302017_000-00-0000 csv"
The bucket where these objects are being stored is using server-side encryption (SSE). Which solution is the most secure and cost-effective option to protect the sensitive data?
Question 11
A Security Engineer must design a solution that enables the Incident Response team to audit for changes to a user’s IAM permissions in the case of a security incident.
How can this be accomplished?
How can this be accomplished?
Question 12
You have several S3 buckets defined in your AWS account. You need to give access to external AWS accounts to these S3 buckets. Which of the following can allow you to define the permissions for the external accounts? Choose 2 answers from the options given below
Please select:
Please select:
Question 13
An organization policy states that all encryption keys must be automatically rotated every 12 months. Which AWS Key Management Service (KMS) key type should be used to meet this requirement?
Question 14
An EC2 Instance hosts a Java based application that access a DynamoDB table. This EC2 Instance is currently serving production based users. Which of the following is a secure way of ensuring that the EC2 Instance access the Dynamo table
Please select:
Please select:
Question 15
What is the result of the following bucket policy?
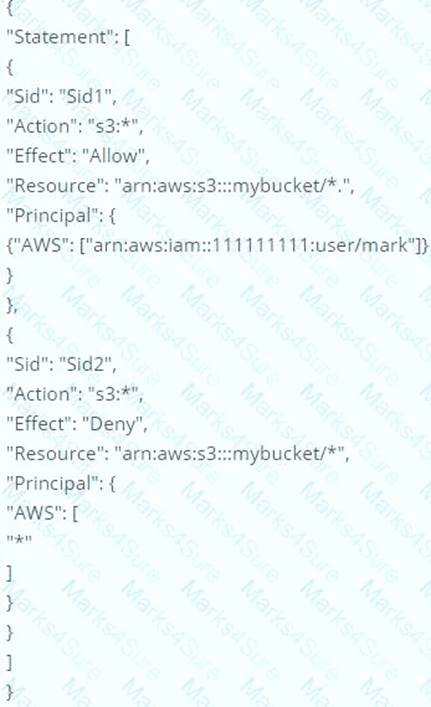
Choose the correct answer
Please select:

Choose the correct answer
Please select:
Question 16
A new application will be deployed on EC2 instances in private subnets. The application will transfer sensitive data to and from an S3 bucket. Compliance requirements state that the data must not traverse the public internet. Which solution meets the compliance requirement?
Please select:
Please select:
Question 17
You need to ensure that the cloudtrail logs which are being delivered in your AWS account is encrypted. How can this be achieved in the easiest way possible?
Please select:
Please select:
Question 18
A company hosts a critical web application on the AWS Cloud. This is a key revenue generating application for the company. The IT Security team is worried about potential DDos attacks against the web site. The senior management has also specified that immediate action needs to be taken in case of a potential DDos attack. What should be done in this regard?
Please select:
Please select:
Question 19
Your company use AWS KMS for management of its customer keys. From time to time, there is a requirement to delete existing keys as part of housekeeping activities. What can be done during the deletion process to verify that the key is no longer being used.
Please select:
Please select:
Question 20
You need to inspect the running processes on an EC2 Instance that may have a security issue. How can you achieve this in the easiest way possible. Also you need to ensure that the process does not interfere with the continuous running of the instance.
Please select:
Please select:
Question 21
Your company is planning on using bastion hosts for administering the servers in AWS. Which of the
following is the best description of a bastion host from a security perspective? Please select:
following is the best description of a bastion host from a security perspective? Please select:
Question 22
A company plans to move most of its IT infrastructure to AWS. The company wants to leverage its existing on-premises Active Directory as an identity provider for AWS.
Which steps should be taken to authenticate to AWS services using the company's on-premises Active Directory? (Choose three).
Which steps should be taken to authenticate to AWS services using the company's on-premises Active Directory? (Choose three).
Question 23
An application outputs logs to a text file. The logs must be continuously monitored for security incidents. Which design will meet the requirements with MINIMUM effort?
Question 24
A company has Windows Amazon EC2 instances in a VPC that are joined to on-premises Active Directory servers for domain services. The security team has enabled Amazon GuardDuty on the AWS account to alert on issues with the instances.
During a weekly audit of network traffic, the Security Engineer notices that one of the EC2 instances is attempting to communicate with a known command-and-control server but failing. This alert does not show up in GuardDuty.
Why did GuardDuty fail to alert to this behavior?
During a weekly audit of network traffic, the Security Engineer notices that one of the EC2 instances is attempting to communicate with a known command-and-control server but failing. This alert does not show up in GuardDuty.
Why did GuardDuty fail to alert to this behavior?
Question 25
An application has been built with Amazon EC2 instances that retrieve messages from Amazon SQS. Recently, IAM changes were made and the instances can no longer retrieve messages.
What actions should be taken to troubleshoot the issue while maintaining least privilege. (Select two.)
What actions should be taken to troubleshoot the issue while maintaining least privilege. (Select two.)