28 November, 2019
Microsoft 365 Mobility And Security (beta) MS-101 Courses
Your success in Microsoft MS-101 is our sole target and we develop all our MS-101 braindumps in a way that facilitates the attainment of this target. Not only is our MS-101 study material the best you can find, it is also the most detailed and the most updated. MS-101 Practice Exams for Microsoft {category} MS-101 are written to the highest standards of technical accuracy.
Question 1
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online.
In the mailbox of a user named User 1. You need to preserve a copy of all the email messages that contain the word Project X.
WDM should you do?
All users have their email stored in Microsoft Exchange Online.
In the mailbox of a user named User 1. You need to preserve a copy of all the email messages that contain the word Project X.
WDM should you do?
Question 2
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You have three applications named App1, App2, and App3 that have the same file format.
Your company uses Windows Information Protection (WIP). WIP has the following configurations: Windows Information Protection mode: Silent
Protected apps: App1 Exempt apps: App2
From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
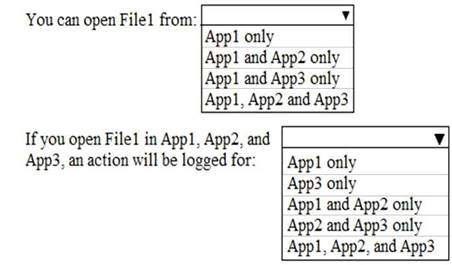
Solution:
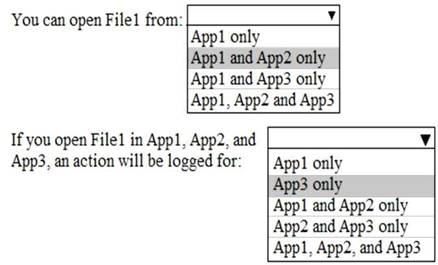
Does this meet the goal?
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You have three applications named App1, App2, and App3 that have the same file format.
Your company uses Windows Information Protection (WIP). WIP has the following configurations: Windows Information Protection mode: Silent
Protected apps: App1 Exempt apps: App2
From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 3
You have a Microsoft 365 subscription. You have a user named User1. You need to ensure that User1 can place a hold on all mailbox content. Which rote should you assign to User1?
Question 4
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals- Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint shoring policy to prevent sharing outside your organization.
You need to be notified if the SharePoint sharing policy is modified m the future. Solution: From the SharePoint admin center, you modify the sharing settings. Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint shoring policy to prevent sharing outside your organization.
You need to be notified if the SharePoint sharing policy is modified m the future. Solution: From the SharePoint admin center, you modify the sharing settings. Does this meet the goal?
Question 5
Your network contains an on premises Active Directory domain.
Your company has a security policy that prevents additional software from txnrwj installed on domain controllers.
You need to monitor a domain controller by using Microsoft Azure Advanced Threat Protection (ATP). What should you do? More than one answer choice may achieve the goal. Select the BEST answer.
Your company has a security policy that prevents additional software from txnrwj installed on domain controllers.
You need to monitor a domain controller by using Microsoft Azure Advanced Threat Protection (ATP). What should you do? More than one answer choice may achieve the goal. Select the BEST answer.
Question 6
DRAG DROP
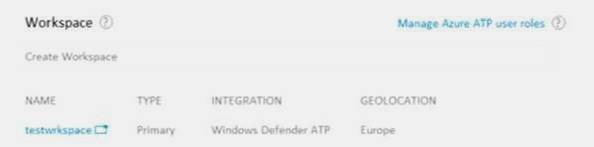
You have the Microsoft Azure Advanced Threat Protection (ATP) workspace shown in the Workspace exhibit. (Click the Workspace tab.)
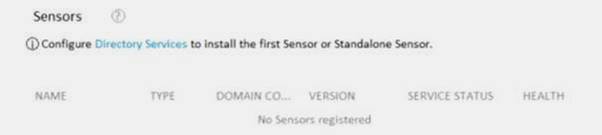
The sensors settings for the workspace are configured as shown in the Sensors exhibit. (Click the Sensors tab.)
You need to ensure that Azure ATP stores data in Asia.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
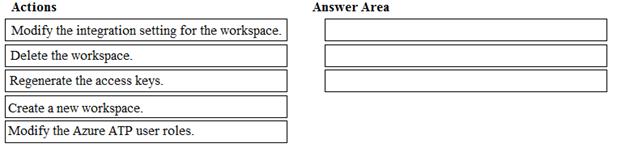
Solution:
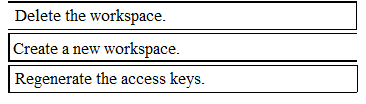
Does this meet the goal?
You have the Microsoft Azure Advanced Threat Protection (ATP) workspace shown in the Workspace exhibit. (Click the Workspace tab.)

The sensors settings for the workspace are configured as shown in the Sensors exhibit. (Click the Sensors tab.)

You need to ensure that Azure ATP stores data in Asia.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Solution:

Does this meet the goal?
Question 7
HOTSPOT
You have three devices enrolled in Microsoft Intune as shown in the following table.
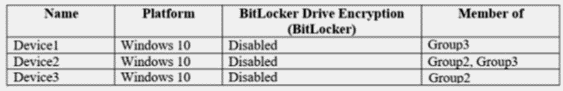
The device compliance policies in Intune are configured as shown in the following table.
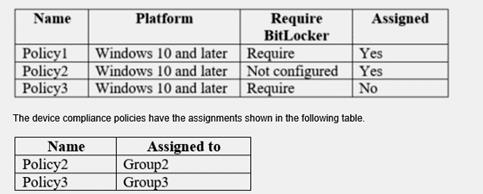
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Solution:

Does this meet the goal?
You have three devices enrolled in Microsoft Intune as shown in the following table.

The device compliance policies in Intune are configured as shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 8
DRAG DROP
You have a Microsoft 365 subscription.
You have the devices shown in the following table.

You need to onboard the devices to Windows Defender Advanced Threat Protection (ATP). The solution must avoid installing software on the devices whenever possible.
Which onboarding method should you use for each operating system? To answer, drag the appropriate methods to the correct operating systems. Each method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
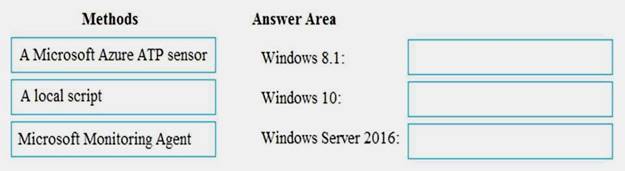
Solution:
References:
hHYPERLINK "https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/onboard-downlevel-windows-defender-advanced-threat-protection"ttps://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/onboard-downlevel-windows-defender-advanced-threat-protection https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/configure-endpoints-windows-defender-advanced-threat-protection https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/configure-server-endpoints-HYPERLINK "https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/configure-server-endpoints-windows-defender-advanced-threat-protection"windows-defender-advanced-threat-protection
Does this meet the goal?
You have a Microsoft 365 subscription.
You have the devices shown in the following table.

You need to onboard the devices to Windows Defender Advanced Threat Protection (ATP). The solution must avoid installing software on the devices whenever possible.
Which onboarding method should you use for each operating system? To answer, drag the appropriate methods to the correct operating systems. Each method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

Solution:
References:
hHYPERLINK "https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/onboard-downlevel-windows-defender-advanced-threat-protection"ttps://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/onboard-downlevel-windows-defender-advanced-threat-protection https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/configure-endpoints-windows-defender-advanced-threat-protection https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/configure-server-endpoints-HYPERLINK "https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/configure-server-endpoints-windows-defender-advanced-threat-protection"windows-defender-advanced-threat-protection
Does this meet the goal?
Question 9
You need to meet the technical requirement for the EU PII data. What should you create?
Question 10
The users at your company use Dropbox to store documents. The users access Dropbox by using the MyApps portal.
You need to ensure that user access to Dropbox is authenticated by using a Microsoft 365 identify. The documents must be protected if the data is downloaded to an untrusted device.
What should you do?
You need to ensure that user access to Dropbox is authenticated by using a Microsoft 365 identify. The documents must be protected if the data is downloaded to an untrusted device.
What should you do?
Question 11
You have computers that run Windows 10 Enterprise and are joined to the domain.
You plan to delay the installation of new Windows builds so that the IT department can test application
compatibility.
You need to prevent Windows from being updated for the next 30 days.
Which two Group Policy settings should you configure? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You plan to delay the installation of new Windows builds so that the IT department can test application
compatibility.
You need to prevent Windows from being updated for the next 30 days.
Which two Group Policy settings should you configure? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Question 12
Your company has 5,000 Windows 10 devices. All the devices are protected by using Windows Defender
Advanced Threat Protection (ATP).
You need to view which Windows Defender ATP alert events have a high severity and occurred during the last seven days.
What should you use in Windows Defender ATP?
Advanced Threat Protection (ATP).
You need to view which Windows Defender ATP alert events have a high severity and occurred during the last seven days.
What should you use in Windows Defender ATP?
Question 13
Your company has five security information and event management (SIEM) appliances. The traffic logs from each appliance are saved to a file share named Logs.
You need to analyze the traffic logs.
What should you do from Microsoft Cloud App Security?
You need to analyze the traffic logs.
What should you do from Microsoft Cloud App Security?
Question 14
HOTSPOT
From the Security & Compliance admin center, you create a retention policy named Policy1. You need to prevent all users from disabling the policy or reducing the retention period.
Which command should you run? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
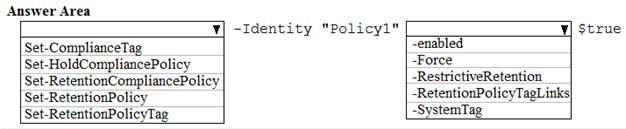
Solution:
References:
https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-retention/set-retentioncompliancepolicy?view=exchange-pHYPERLINK "https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-retention/set-retentioncompliancepolicy?view=exchange-ps"s
Does this meet the goal?
From the Security & Compliance admin center, you create a retention policy named Policy1. You need to prevent all users from disabling the policy or reducing the retention period.
Which command should you run? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

Solution:
References:
https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-retention/set-retentioncompliancepolicy?view=exchange-pHYPERLINK "https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-retention/set-retentioncompliancepolicy?view=exchange-ps"s
Does this meet the goal?
Question 15
Your company has a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You sign for Microsoft Store for Business.
The tenant contains the users shown in the following table.
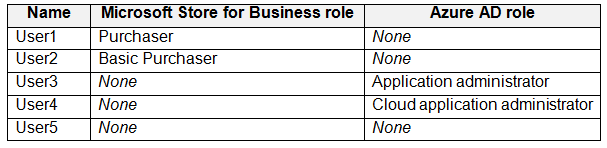
Microsoft Store for Business has the following Shopping behavior settings: Allow users to shop is set to On
Make everyone a Basic Purchaser is set to Off
You need to identify which users can install apps from the Microsoft for Business private store.
Which users should you identify?
The tenant contains the users shown in the following table.

Microsoft Store for Business has the following Shopping behavior settings: Allow users to shop is set to On
Make everyone a Basic Purchaser is set to Off
You need to identify which users can install apps from the Microsoft for Business private store.
Which users should you identify?
Question 16
You need to ensure that the support technicians can meet the technical requirement for the Montreal office mobile devices.
What is the minimum of dedicated support technicians required?
What is the minimum of dedicated support technicians required?
Question 17
You need to create the Microsoft Store for Business. Which user can create the store?
Question 18
You configure a conditional access policy. The locations settings are configured as shown in the Locations exhibit. (Click the Locations tab.)
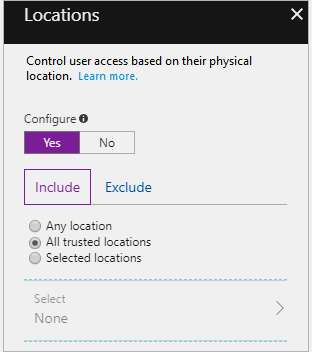
The users and groups settings are configured as shown in the Users and Groups exhibit. (Click Users and Groups tab.)
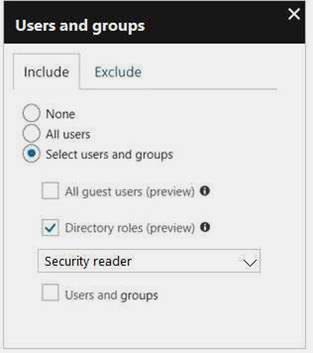
Members of the Security reader group report that they cannot sign in to Microsoft Active Directory (Azure AD) on their device while they are in the office.
You need to ensure that the members of the Security reader group can sign in in to Azure AD on their device while they are in the office. The solution must use the principle of least privilege.
What should you do?

The users and groups settings are configured as shown in the Users and Groups exhibit. (Click Users and Groups tab.)

Members of the Security reader group report that they cannot sign in to Microsoft Active Directory (Azure AD) on their device while they are in the office.
You need to ensure that the members of the Security reader group can sign in in to Azure AD on their device while they are in the office. The solution must use the principle of least privilege.
What should you do?
Question 19
You have a Microsoft 365 subscription
All users are assigned a Microsoft 365 E3 License. You enable auditing for your organization.
What is the maximum amount of time data will be retained in the Microsoft 365 audit log?
All users are assigned a Microsoft 365 E3 License. You enable auditing for your organization.
What is the maximum amount of time data will be retained in the Microsoft 365 audit log?
Question 20
HOTSPOT
You have a document in Microsoft OneDrive that is encrypted by using Microsoft Azure Information Protection as shown in the following exhibit.
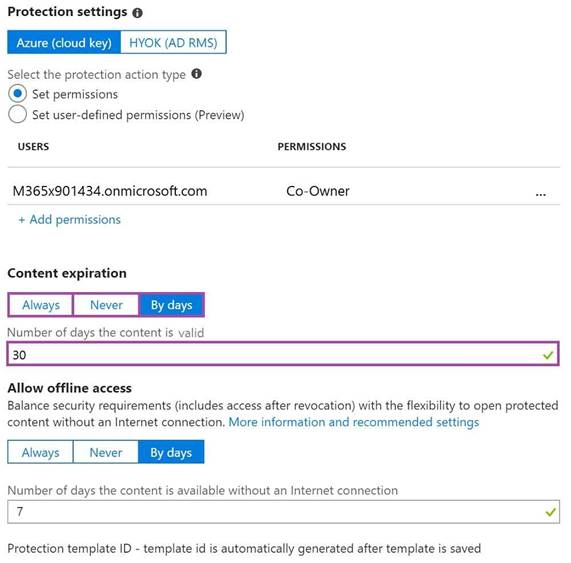
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
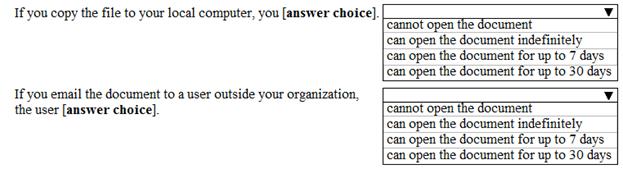
Solution:
References:
https://docs.microsoft.com/en-us/azure/information-protection/configure-policy-protection
Does this meet the goal?
You have a document in Microsoft OneDrive that is encrypted by using Microsoft Azure Information Protection as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Solution:
References:
https://docs.microsoft.com/en-us/azure/information-protection/configure-policy-protection
Does this meet the goal?
Question 21
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Azure Active Directory admin center, you create a trusted location and a conditional access policy.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Azure Active Directory admin center, you create a trusted location and a conditional access policy.
Does this meet the goal?
