26 December, 2019
MTA Security Fundamentals Practice Test 98-367 Pdf
We provide real 98-367 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Microsoft 98-367 Exam quickly & easily. The 98-367 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Microsoft 98-367 dumps pdf and vce product and material, you can easily pass the 98-367 exam.
Question 1
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:
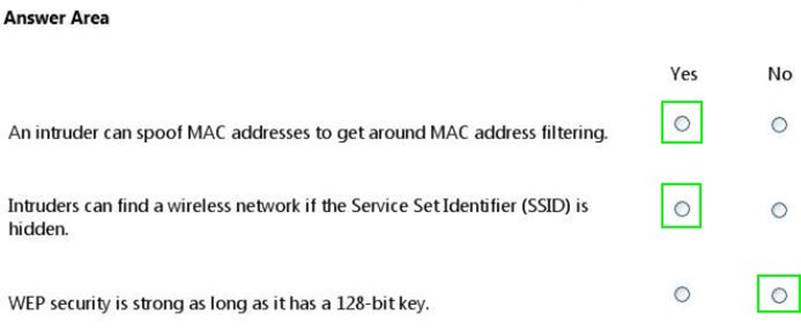
Does this meet the goal?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 2
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
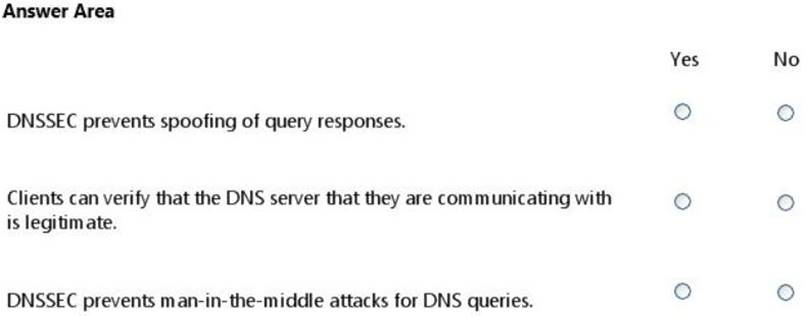
Solution:
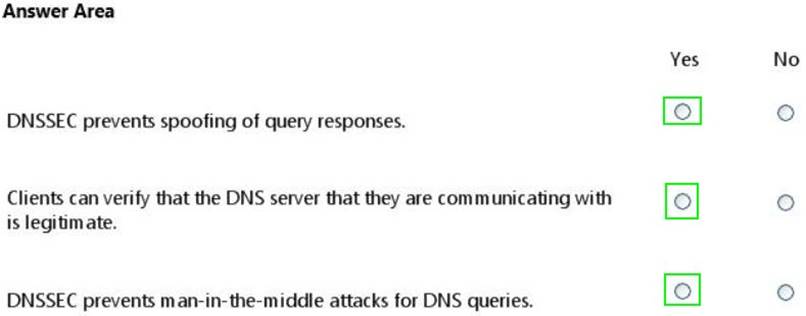
Does this meet the goal?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 3
What does NAT do?
Question 4
Your password is 1Vu*cI!8sT.
Which attack method is your password vulnerable to?
Which attack method is your password vulnerable to?
Question 5
Windows Firewall is a built-in. host-based, stateless firewall.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
Question 6
You need to limit the programs that can run on client computers to a specific list. Which technology should you implement?
Question 7
The default password length for a Windows Server domain controller is:
Question 8
E-mail bombing attacks a specific entity by:
Question 9
Creating MD5 hash for files is an example of ensuring what?
Question 10
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 11
How does the sender policy framework (SPF) aim to reduce spoofed email?
Question 12
You are an intern and are working remotely.
You need a solution that meets the following requirements:
✑ Allows you to access data on the company network securely
✑ Gives you the same privileges and access as if you were in the office
What are two connection methods you could use? (Choose two.)
You need a solution that meets the following requirements:
✑ Allows you to access data on the company network securely
✑ Gives you the same privileges and access as if you were in the office
What are two connection methods you could use? (Choose two.)
Question 13
In Internet Explorer 8, the InPrivate Browsing feature prevents:
Question 14
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select
No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
For each of the following statements, select Yes if the statement is true. Otherwise, select
No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 15
You have a Windows 7 desktop computer, and you create a Standard User account for your roommate so that he can use the desktop from time to time. Your roommate has forgotten his password.
Which two actions can you take to reset the password? (Choose two.)
Which two actions can you take to reset the password? (Choose two.)
Question 16
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 17
You need to grant a set of users write access to a file on a network share. You should add the users to:
Question 18
You are volunteering at an organization that gets a brand new web server. To make the server more secure, you should add a second administrator account.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
Question 19
Bridging is a process of sending packets from source to destination on OSI layer 3.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
Question 20
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
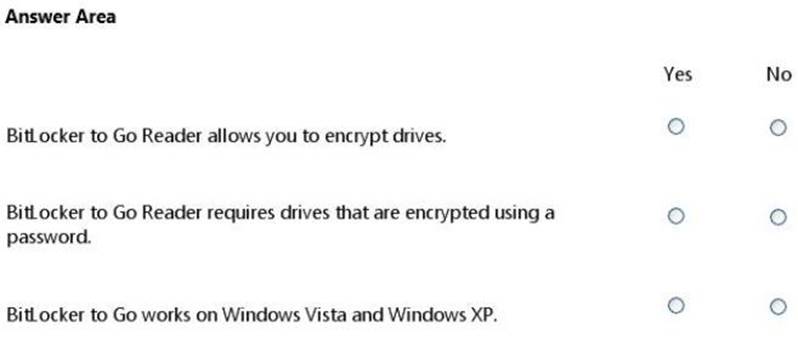
Solution:
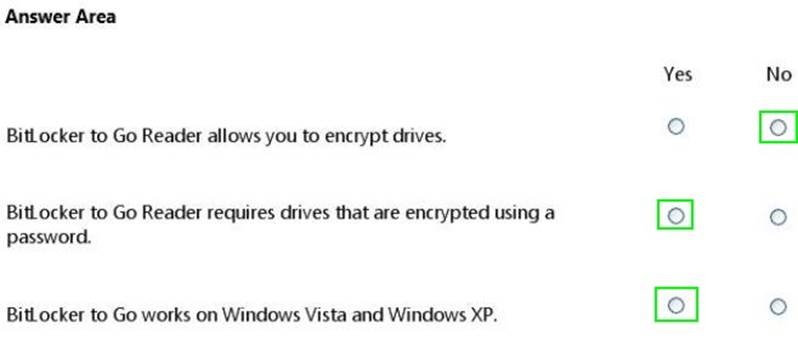
Does this meet the goal?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Solution:

Does this meet the goal?
Question 21
HOTSPOT
You are preparing an audit policy for the workstations at Contoso, Ltd. Currently, no advanced auditing is enabled. The workstations are not members of the domain.
The settings of your Advanced Audit Policy Configuration are shown in the following image:
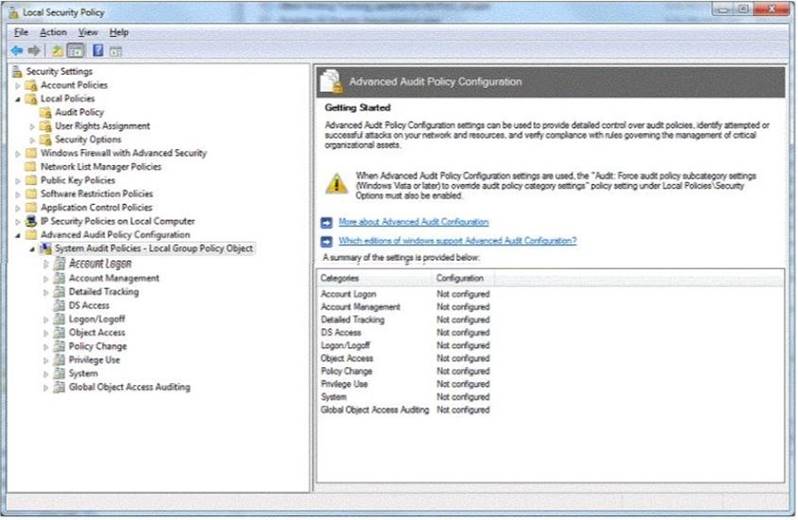
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
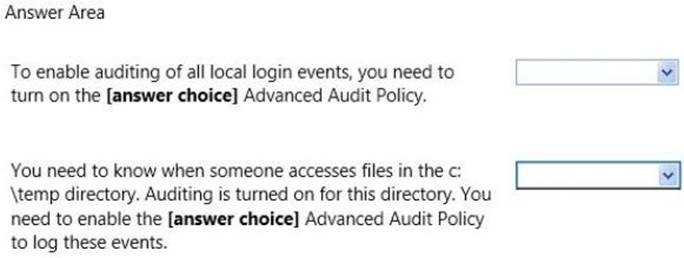
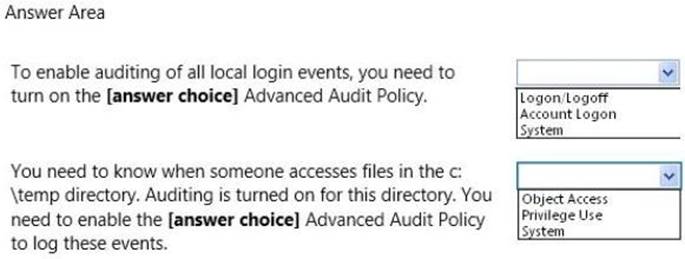
Solution:
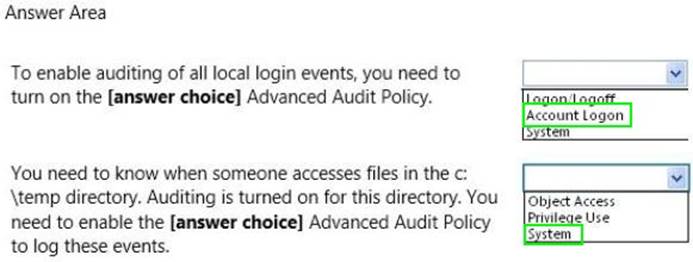
Does this meet the goal?
You are preparing an audit policy for the workstations at Contoso, Ltd. Currently, no advanced auditing is enabled. The workstations are not members of the domain.
The settings of your Advanced Audit Policy Configuration are shown in the following image:

Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.


Solution:

Does this meet the goal?
Question 22
Which three elements does HTTPS encrypt? (Choose three.)
