16 February, 2020
Pinpoint Cisco 300-375 Paper
Master the 300-375 Securing Cisco Wireless Enterprise Networks content and be ready for exam day success quickly with this Passleader 300-375 test questions. We guarantee it!We make it a reality and give you real 300-375 questions in our Cisco 300-375 braindumps.Latest 100% VALID Cisco 300-375 Exam Questions Dumps at below page. You can use our Cisco 300-375 braindumps and pass your exam.
Free demo questions for Cisco 300-375 Exam Dumps Below:
Question 1
Which two options are types of MFP that can be performed? (Choose two.)
Question 2
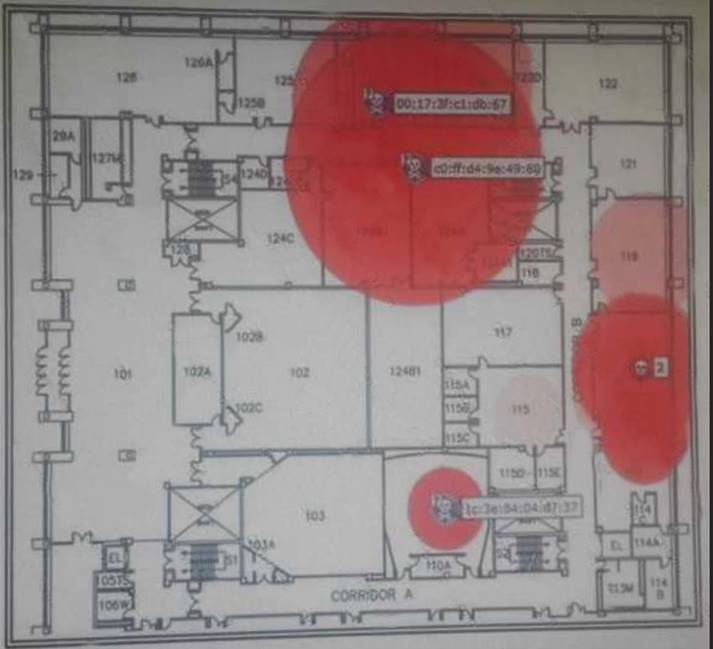
Refer to the exhibit. What do the red circles represent in the exhibit?

Question 3
An engineer is troubleshooting rogue access points that are showing up in Cisco Prime Infrastructure. What is the maximum number of Aps the engineer can use to contain an identified rogue access point in the WLC?
Question 4
When you configure BYOD access to the network, you face increased security risks and challenges. Which challenge is resolved by deploying digital client certificates?
Question 5
Which option determines which RADIUS server is preferred the most by the Cisco WLC?
Question 6
Which configuration step is necessary to enable Visitor Connect on an SSID?
Question 7
Which security method does a Cisco guest wireless deployment that relies on Cisco ISE guest portal for user authentication use?
Question 8
802.1X AP supplicant credentials have been enabled and configured on a Cisco WLC v7.0 in both the respective Wireless>AP>Global Configuration location and AP>Credentials tab locations. What describes the 802.1X AP authentication process when connected via Ethernet to a switch?
Question 9
Scenario
Local Web Auth has been configured on the East-WLC-2504A, but it is not working. Determine which actions must be taken to restore the Local Web Auth service. The Local Web Auth service must operate only with the Contractors WLAN.
Contractors WLAN ID – 10 Employees WLAN ID - 2
Note, not all menu items, text boxes, or radio buttons are active.
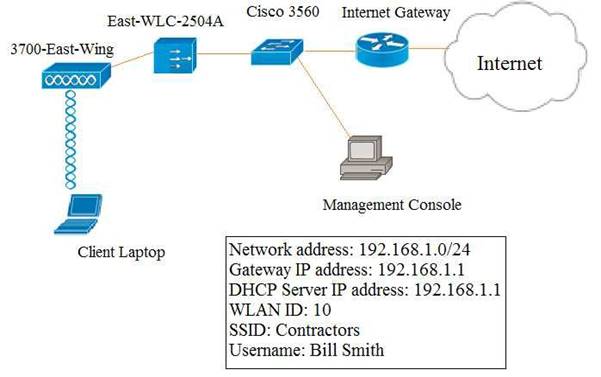
Virtual Terminal
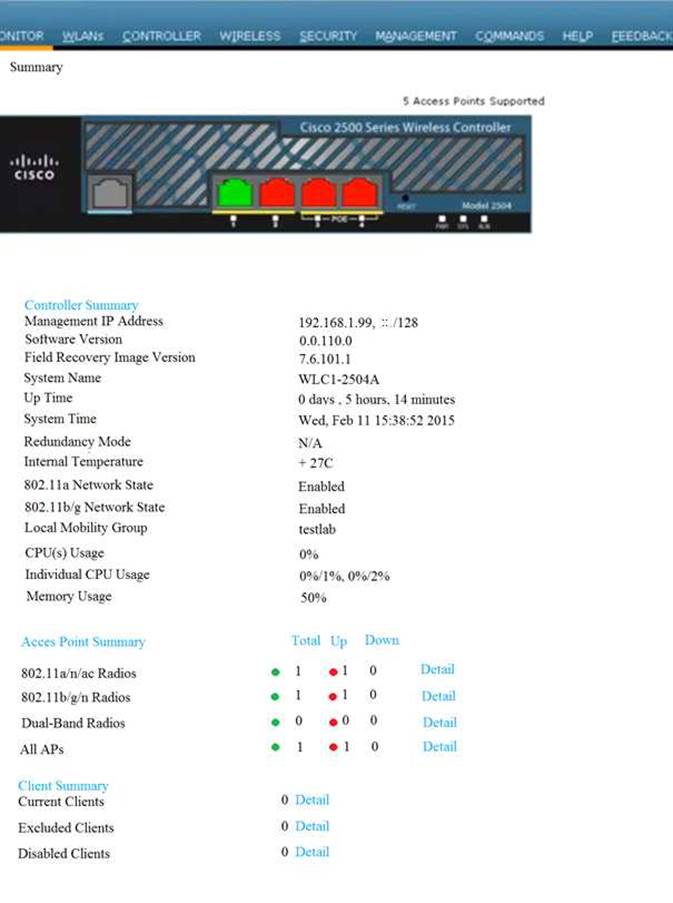
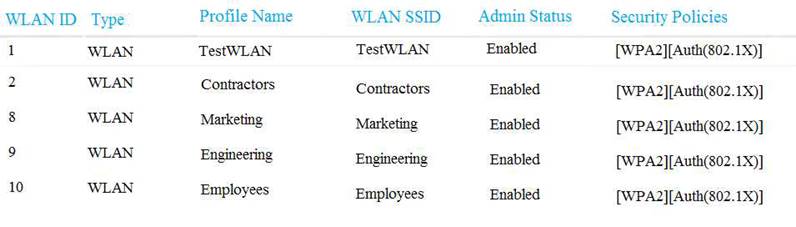
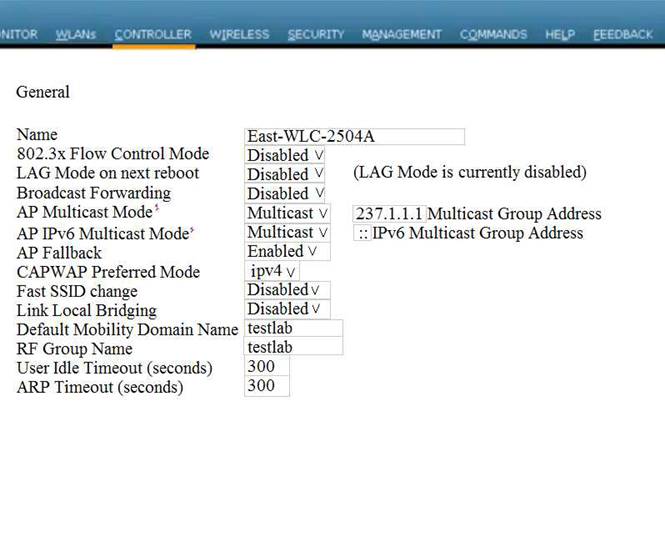
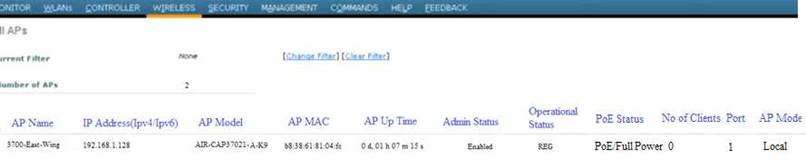
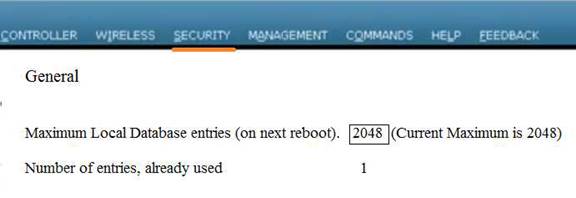
Which four changes must be made to configuration parameters to restore the Local Web Auth feature on the East-WLC-2504A? Assume the passwords are correctly entered as “ciscotest”. (Choose four.)
Local Web Auth has been configured on the East-WLC-2504A, but it is not working. Determine which actions must be taken to restore the Local Web Auth service. The Local Web Auth service must operate only with the Contractors WLAN.
Contractors WLAN ID – 10 Employees WLAN ID - 2
Note, not all menu items, text boxes, or radio buttons are active.

Virtual Terminal





Which four changes must be made to configuration parameters to restore the Local Web Auth feature on the East-WLC-2504A? Assume the passwords are correctly entered as “ciscotest”. (Choose four.)
Question 10
Which attribute on the Cisco WLC v7.0 does RADIUS IETF attribute "Tunnel-Private-Group ID" assign?
Question 11
Which client roam is considered the fastest in a wireless deployment using Cisco IOS XE mobility controllers and mobility agents?
Question 12
Refer to the exhibit.
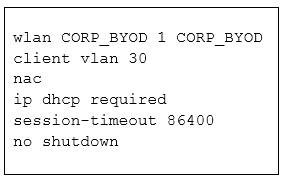
A network engineer must configure a WLAN on a Cisco IOS-XE controller to support corporate devices (using VLAN 30) and BYOD (using VLAN 40) on the same secure SSID. The security team has built an ISE deployment to be used for VLAN assignment and to restrict access based on policy and posture compliance.
Given the existing WLAN configuration, which configuration change must be made?

A network engineer must configure a WLAN on a Cisco IOS-XE controller to support corporate devices (using VLAN 30) and BYOD (using VLAN 40) on the same secure SSID. The security team has built an ISE deployment to be used for VLAN assignment and to restrict access based on policy and posture compliance.
Given the existing WLAN configuration, which configuration change must be made?
Question 13
An engineer must enable EAP on a new WLAN and is ensuring that the necessary components are available. Which component uses EAP and 802.1x to pass user authentication to the authenticator?
Question 14
Which of the following user roles can access CMX Visitor Connect?
Question 15
WPA2 Enterprise with 802.1x is being used for clients to authenticate to a wireless network through
an ACS server. For security reasons, the network engineer wants to ensure only PEAP authentication can be used. The engineer sent instructions to clients on how to configure their supplicants, but users are still in the ACS logs authentication using EAP-FAST. Which option describes the most efficient way the engineer can ensure these users cannot access the network unless the correct authentication mechanism is configured?
an ACS server. For security reasons, the network engineer wants to ensure only PEAP authentication can be used. The engineer sent instructions to clients on how to configure their supplicants, but users are still in the ACS logs authentication using EAP-FAST. Which option describes the most efficient way the engineer can ensure these users cannot access the network unless the correct authentication mechanism is configured?
Question 16
Which command is an SNMPv3-specific command that an engineer can use only in Cisco IOS XE?
Question 17
An engineer has configured the wireless controller to authenticate clients on the employee SSID against Microsoft Active Directory using PEAP authentication. Which protocol does the controller use to communicate with the authentication server?
Question 18
During the EAP process and specifically related to the logon session, which encrypted key is sent from the RADIUS server to the access point?
Question 19
An engineer is designing a high availability wireless network. What mechanism should be the focus for high availability?
Question 20
How should the Cisco Secure ACS v4.2 and the Cisco WLC v7.0 be configured to support wireless client authentication?
Question 21
An engineer must change the wireless authentication from WPA2-Personal to WPA2-Enterprise. Which three requirements are necessary? (Choose three.)
Question 22
Which two events are possible outcomes of a successful RF jamming attack? (Choose two.)
