23 September, 2020
Rebirth C9510-401 Practice Exam For IBM WebSphere Application Server Network Deployment V8.5.5 And Liberty Profile, System Administration Certification
Master the C9510-401 IBM WebSphere Application Server Network Deployment V8.5.5 and Liberty Profile, System Administration content and be ready for exam day success quickly with this Exambible C9510-401 testing engine. We guarantee it!We make it a reality and give you real C9510-401 questions in our IBM C9510-401 braindumps.Latest 100% VALID IBM C9510-401 Exam Questions Dumps at below page. You can use our IBM C9510-401 braindumps and pass your exam.
Online C9510-401 free questions and answers of New Version:
Question 1
A system administrator needs to trigger a javacore only when a java,net.SocketTimeoutException is encountered in real time.
What does the administrator have to configure to trigger the javacore dump?
What does the administrator have to configure to trigger the javacore dump?
Question 2
Which one of the following options describes the runtime flow starting from the client browser in a clustered WebSphere Application Server Network Deployment topology?
Question 3
A system administrator needs to set a new Liberty profile environment to support an application.
What should the administrator do to enable this environment for high availability and scalability of the application?
What should the administrator do to enable this environment for high availability and scalability of the application?
Question 4
A system administrator has added a server cluster as a member of a service integration bus (SIB). The administrator needs to configure one messaging engine for each server in this cluster and to have a failover location for each messaging engine.
What should the administrator do to achieve the required design?
What should the administrator do to achieve the required design?
Question 5
Which of the following comprises an initial Liberty profile server process?
Question 6
The application placement controller has been configured with elasticity mode enabled. Intermittently, all instances of a dynamic cluster are removed. After further review, the system administrator noticed that it occurs during peak load on another dynamic cluster.
The administrator wants to keep at least one instance available. Which configuration is needed in the dynamic clusters?
The administrator wants to keep at least one instance available. Which configuration is needed in the dynamic clusters?
Question 7
A system administrator has configured a network deployment cell containing multiple nodes and global security enabled with an LDAP repository. To increase capacity, the administrator needs to add additional nodes to the cell. After adding the nodes by using both scripts and the Integrated Solutions Console (ISC), the administrator examines the System.out log for the deployment manager and notices the following message:
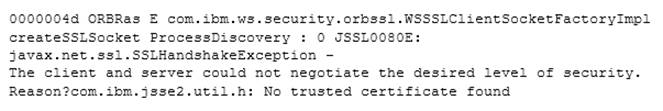
How can the administrator resolve this problem?

How can the administrator resolve this problem?
Question 8
A system administrator has created a Jython script that will run in WebSphere Network cell where administrative security is enabled. This script is named doUpdate.py and will be run by using the following:
wsadmin –connType RMI –f doUpdate.py
How can the administrator suppress a user/password prompt from appearing when this script is run?
Set the user and password in the:
wsadmin –connType RMI –f doUpdate.py
How can the administrator suppress a user/password prompt from appearing when this script is run?
Set the user and password in the:
Question 9
A system administrator wants to learn some of the Python scripting commands for the administration of the environment.
Which product feature should the administrator use?
Which product feature should the administrator use?
Question 10
A system administrator decides to use the advice from the Performance and Diagnostic Advisor to identify the optimum connection pool settings for data sources. In a cell, the data source db2datasource is defined under node scope and used by two servers from that node. The administrator receives two different sets of advice for db2datasource.
How should the administrator configure the data sources before reusing the Performance and Diagnostic Advisor?
How should the administrator configure the data sources before reusing the Performance and Diagnostic Advisor?
Question 11
A system administrator needs to create a cell for a test environment. The administrator uses the Profile Management Tool (PMT) to create the deployment manager profile using the advanced profile creation option and creates a custom profile using the typical profile creation option. The administrator examines the log files for the custom profile creation and sees an INSTCONFFAIL message indicating the deployment manager was not running during the custom profile creation.
How should the administrator fix this?
How should the administrator fix this?
Question 12
A system administrator has added a server cluster as a member of a service integration bus (SIB). The administrator needs to configure one messaging engine for each server in this cluster and to have a failover location for each messaging engine.
What should the administrator do to achieve the required design?
What should the administrator do to achieve the required design?
Question 13
The computer where a federated node was running had a failure and cannot be recovered. A system administrator wants to recreate the node with the same configurations in another computer.
Which steps should the administrator execute in order to recover the damaged node?
Which steps should the administrator execute in order to recover the damaged node?
Question 14
A system administrator is configuring the security of a new environment. The administrator has been asked to configure one LDAP server that has different sub-trees for business users and administration users.
What should the administrator do to implement the required security configuration?
What should the administrator do to implement the required security configuration?
Question 15
A system administrator has installed WebSphere Application Server Network Deployment V8.5.5 using the silent installation process and needs the verify that the installation completed successfully.
What does the administrator need to do to verify a successful installation?
What does the administrator need to do to verify a successful installation?
Question 16
How can a system administrator secure a WebSphere Application Server environment to ensure that an application code will not be allowed to access any files in the server’s file system?
Question 17
The administrator needs to identify any security role references and security constraints in a web application.
How can the administrator identify these roles and constraints?
How can the administrator identify these roles and constraints?
Question 18
A system administrator has created a Python script that will run in WebSphere Network cell where administrative security is enabled. This script is named doUpdate.py and will be run by using the following:
wsadmin -connType RMI -f doUpdate.py
How can the administrator suppress a user/password prompt from appearing when this script is run?
Set the user and password in the:
wsadmin -connType RMI -f doUpdate.py
How can the administrator suppress a user/password prompt from appearing when this script is run?
Set the user and password in the:
Question 19
A newly deployed application has authorization errors when invoking EJB methods from a servlet. An additional review indicates that users are authenticated, but do not have the correct authorization.
How can a system administrator fix the issue ensuring only authorized access?
How can a system administrator fix the issue ensuring only authorized access?
Question 20
A customer has enabled LTPA as their authentication mechanism and has web resources that are not secured by proper security constraints. A system administrator is required to ensure that all web resources are secured.
How should the administrator accomplish this?
How should the administrator accomplish this?
Question 21
A JAX-WS EJB stateless session bean web service needs to be accessed by consumers outside the corporate domain.
Which configuration will help a system administrator meet the requirement?
Which configuration will help a system administrator meet the requirement?
Question 22
A system administrator ran the backup Config command to backup the configuration using the -nostop option. The administrator changed the properties for the service integration environment by modifying the sib.properties file. During testing the administrator noticed Service Integration Bus related errors and wanted to restore the service integration environment. The administrator used the restore config command, but the tuning properties for the service integration environment were not restored.
How can the administrator prevent this issue?
How can the administrator prevent this issue?
Question 23
The installation of WebSphere Application Server did not complete successfully, and a system administrator needs to troubleshoot the installation.
What can the administrator do to identify the cause of the installation failure?
What can the administrator do to identify the cause of the installation failure?
Question 24
A system administrator has created a cluster containing two servers in a same node. The administrator did not select the option Generate unique HTTP ports during the creation of the cluster members. After the cluster creation, the administrator changed the HTTP port of the second cluster member to 9081.
Testing the servers using the snoop servlet directly to the server’s HTTP port, the administrator got the following error message for the second server:

How can the administrator fix this problem?
Testing the servers using the snoop servlet directly to the server’s HTTP port, the administrator got the following error message for the second server:

How can the administrator fix this problem?
