12 December, 2023
Simulation Fortinet FCP_FCT_AD-7.2 Questions Pool Online
Master the FCP_FCT_AD-7.2 FCP-FortiClient EMS 7.2 Administrator content and be ready for exam day success quickly with this Pass4sure FCP_FCT_AD-7.2 practice. We guarantee it!We make it a reality and give you real FCP_FCT_AD-7.2 questions in our Fortinet FCP_FCT_AD-7.2 braindumps.Latest 100% VALID Fortinet FCP_FCT_AD-7.2 Exam Questions Dumps at below page. You can use our Fortinet FCP_FCT_AD-7.2 braindumps and pass your exam.
Question 1
Which statement about the FortiClient enterprise management server is true?
Question 2
What is the function of the quick scan option on FortiClient?
Question 3
An administrator configures ZTNA configuration on the FortiGate. Which statement is true about the firewall policy?
Question 4
Which three features does FortiClient endpoint security include? (Choose three.)
Question 5
Refer to the exhibit.
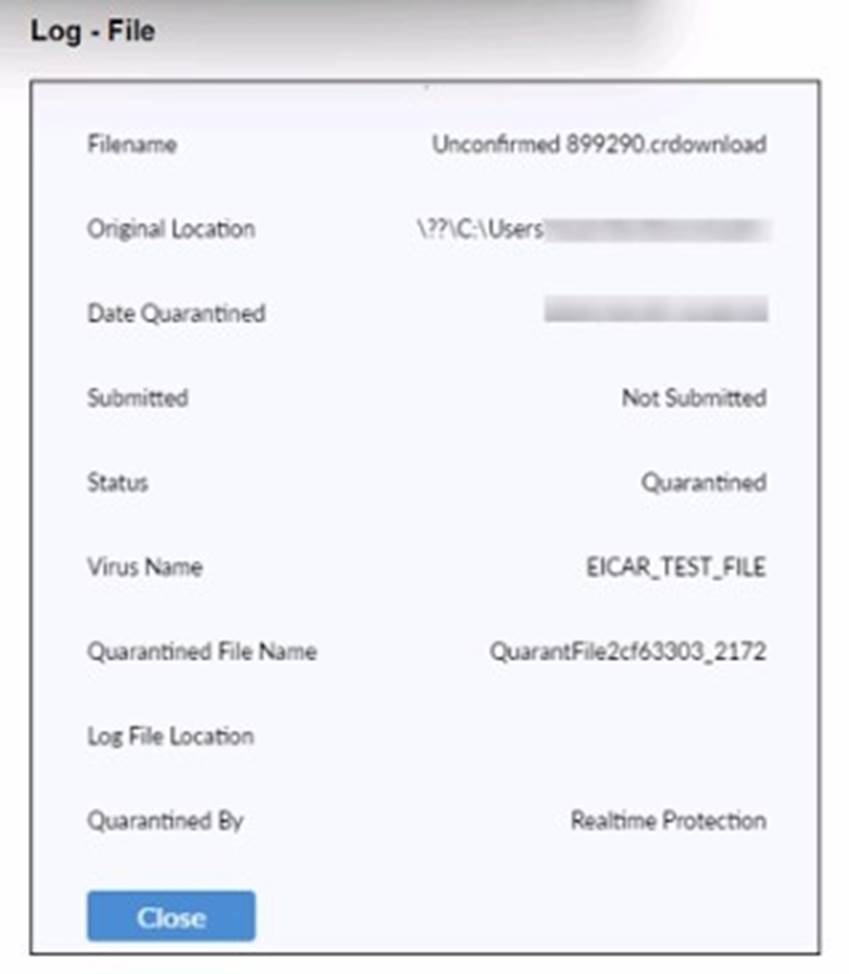
Based on the FortiClient tog details shown in the exhibit, which two statements ace true? (Choose two.)

Based on the FortiClient tog details shown in the exhibit, which two statements ace true? (Choose two.)
Question 6
A FortiClient EMS administrator has enabled the compliance rule for the sales department Which Fortinet device will enforce compliance with dynamic access control?
Question 7
Which component or device shares device status information through ZTNA telemetry?
Question 8
Which two statements about ZTNA destinations are true? (Choose two.)
Question 9
Which component or device shares ZTNA tag information through Security Fabric integration?
Question 10
Refer to the exhibits.
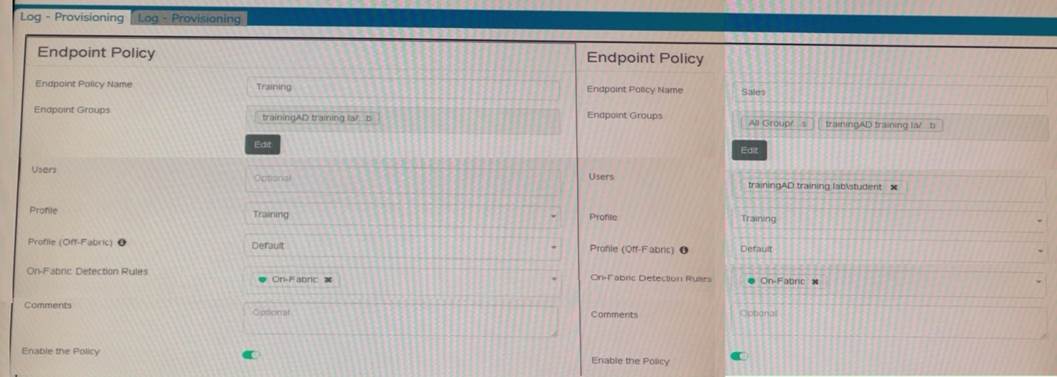
Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account student on an endpoint in the trainingAD domain?


Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account student on an endpoint in the trainingAD domain?
Question 11
Refer to the exhibits.
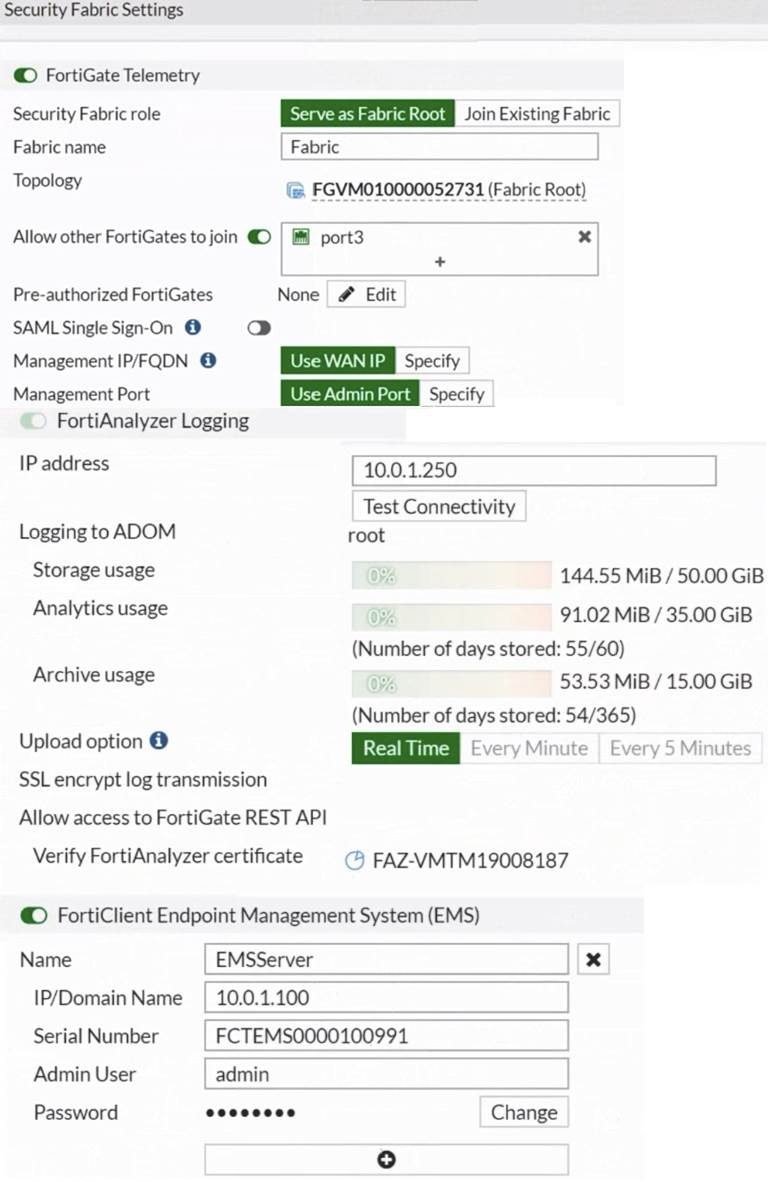
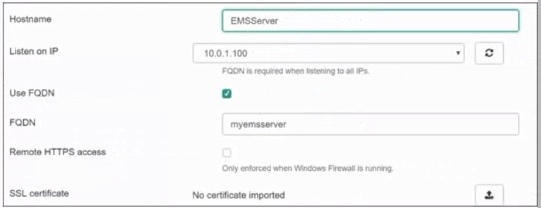
Based on the FortiGate Security Fabric settings shown in the exhibits, what must an administrator do on the EMS server to successfully quarantine an endpoint. when it is detected as a compromised host (loC)?


Based on the FortiGate Security Fabric settings shown in the exhibits, what must an administrator do on the EMS server to successfully quarantine an endpoint. when it is detected as a compromised host (loC)?
Question 12
Refer to the exhibit.
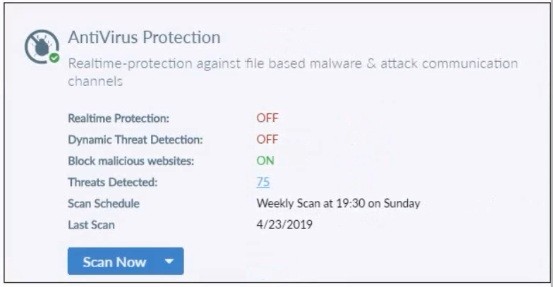
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?

Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
Question 13
Refer to the exhibit.
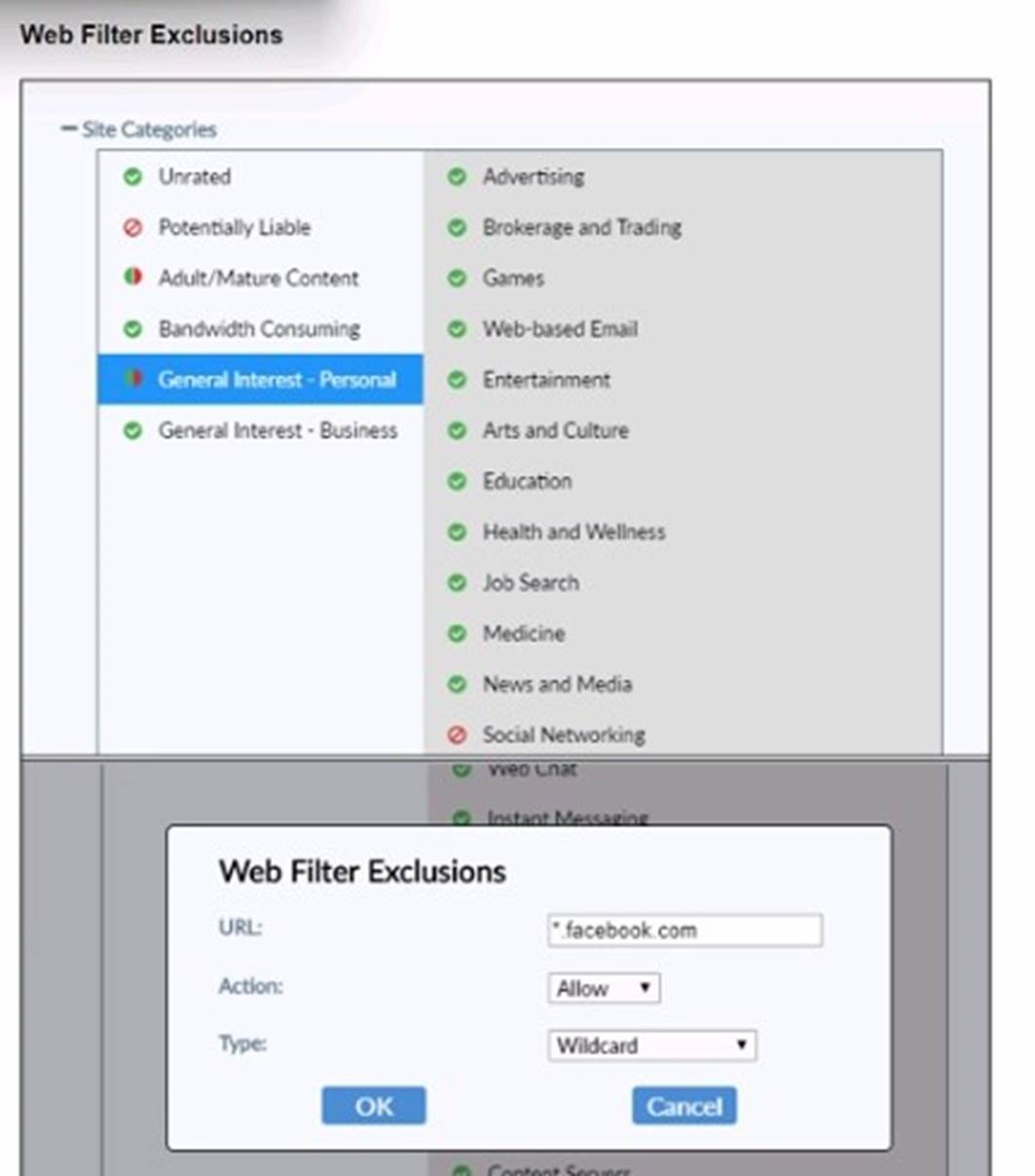
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www facebook com?

Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www facebook com?
Question 14
ZTNA Network Topology
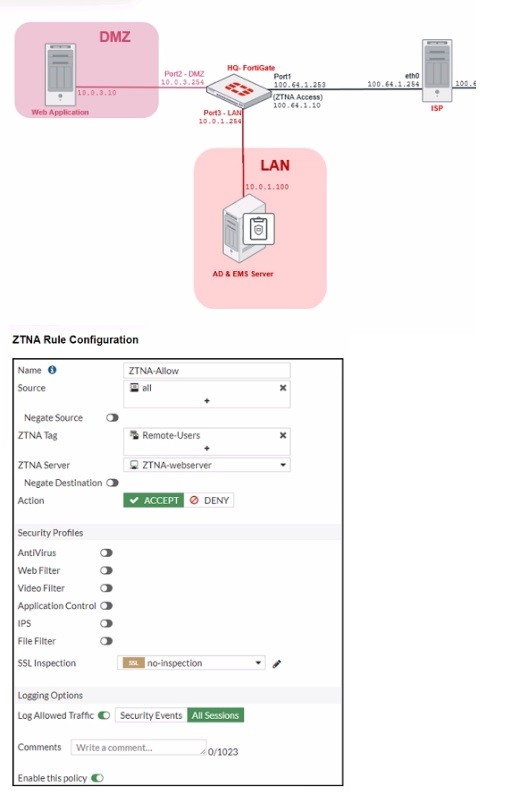
Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-Client endpoint information, however Remote-Client is not showing up in the
endpoint record list.
What is the cause of this issue?

Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-Client endpoint information, however Remote-Client is not showing up in the
endpoint record list.
What is the cause of this issue?
Question 15
Refer to the exhibit.
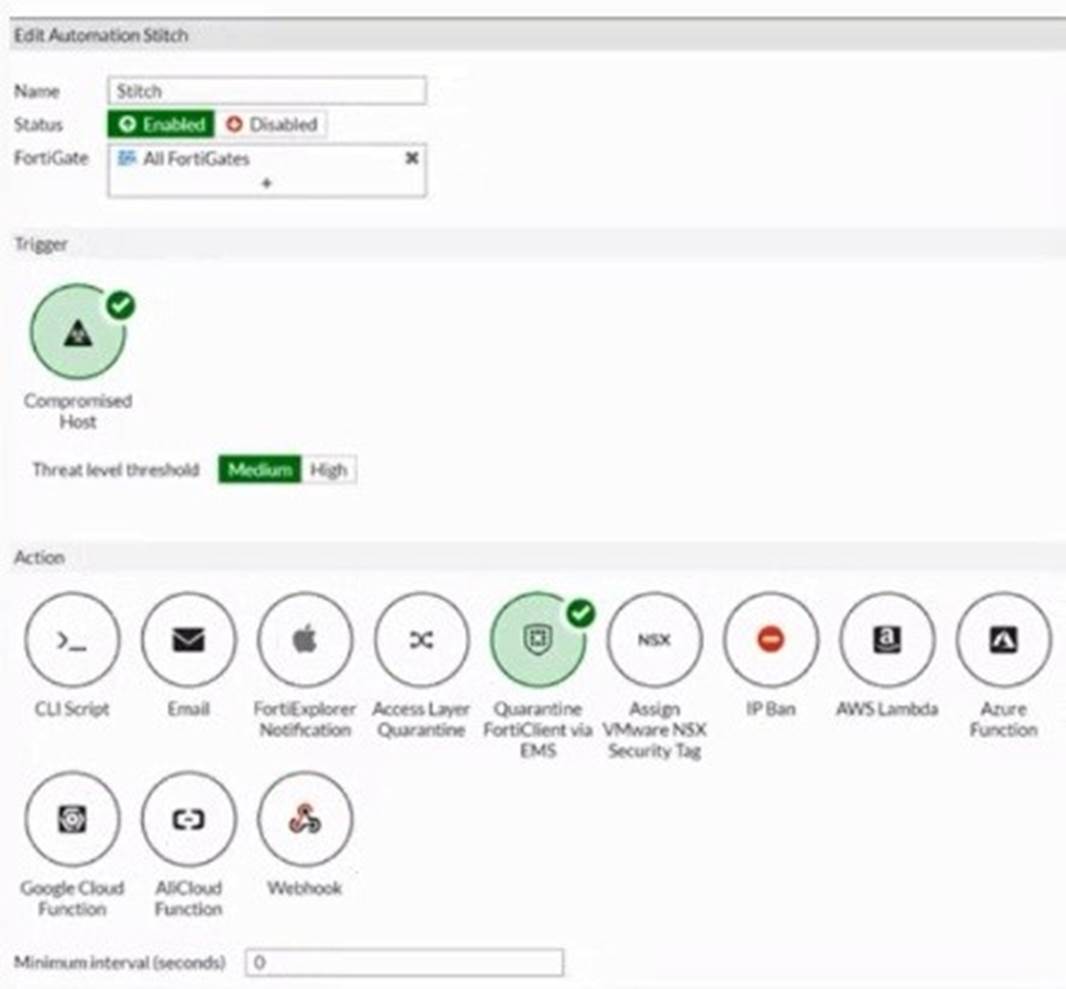
Based on the Security Fabric automation settings, what action will be taken on compromised endpoints?

Based on the Security Fabric automation settings, what action will be taken on compromised endpoints?
Question 16
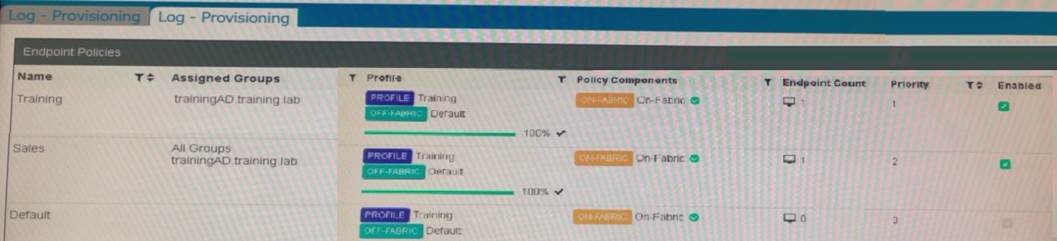
FortiClient EMS endpoint policies
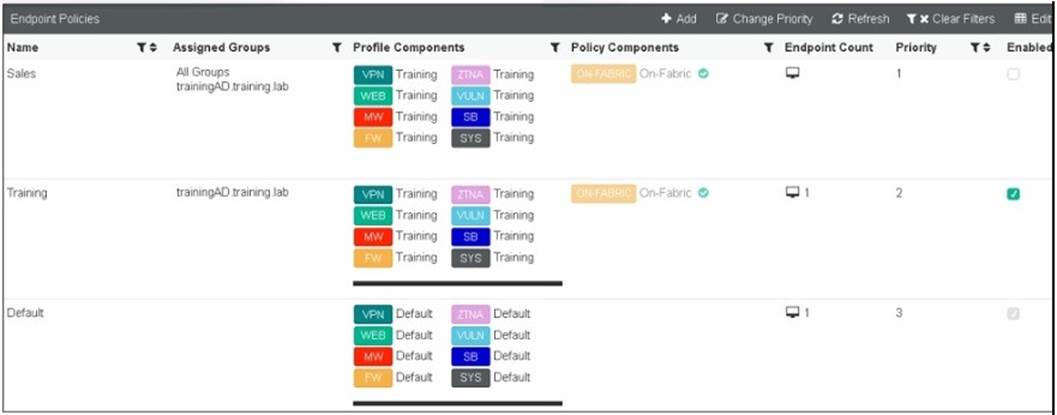
Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS. Which policy is applied to the endpoint in the AD group trainingAD

Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS. Which policy is applied to the endpoint in the AD group trainingAD
