24 August, 2021
The Most Recent Guide To 156-215.80 Training Materials
It is more faster and easier to pass the Check-Point 156-215.80 exam by using Exact Check-Point Check Point Certified Security Administrator questuins and answers. Immediate access to the Renewal 156-215.80 Exam and find the same core area 156-215.80 questions with professionally verified answers, then PASS your exam with a high score now.
Free 156-215.80 Demo Online For Check-Point Certifitcation:
Question 1
- (Exam Topic 3)
A Cleanup rule:
A Cleanup rule:
Question 2
- (Exam Topic 1)
Fill in the blank: The ____ collects logs and sends them to the ____.
Fill in the blank: The ____ collects logs and sends them to the ____.
Question 3
- (Exam Topic 4)
Which SmartConsole tab is used to monitor network and security performance?
Which SmartConsole tab is used to monitor network and security performance?
Question 4
- (Exam Topic 4)
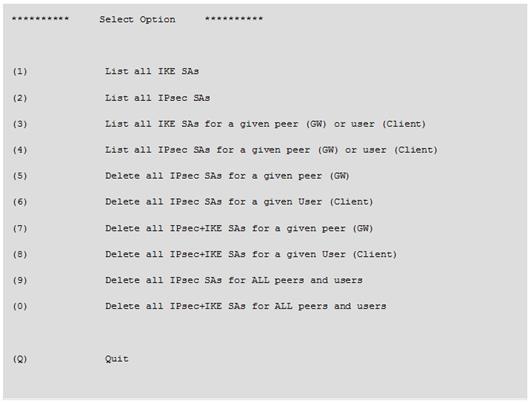
What does it mean if Deyra sees the gateway status
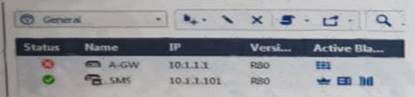
Choose the BEST answer.
What does it mean if Deyra sees the gateway status

Choose the BEST answer.
Question 5
- (Exam Topic 4)
When using Monitored circuit VRRP, what is a priority delta?
When using Monitored circuit VRRP, what is a priority delta?
Question 6
- (Exam Topic 4)
What is the difference between SSL VPN and IPSec VPN?
What is the difference between SSL VPN and IPSec VPN?
Question 7
- (Exam Topic 3)
You are about to test some rule and object changes suggested in an R77 news group. Which backup solution should you use to ensure the easiest restoration of your Security Policy to its previous configuration after testing the changes?
You are about to test some rule and object changes suggested in an R77 news group. Which backup solution should you use to ensure the easiest restoration of your Security Policy to its previous configuration after testing the changes?
Question 8
- (Exam Topic 2)
What statement is true regarding Visitor Mode?
What statement is true regarding Visitor Mode?
Question 9
- (Exam Topic 4)
Fill in the blank: An LDAP server holds one or more ______.
Fill in the blank: An LDAP server holds one or more ______.
Question 10
- (Exam Topic 1)
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ____.
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ____.
Question 11
- (Exam Topic 1)
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
Question 12
- (Exam Topic 2)
After the initial installation the First Time Configuration Wizard should be run. Select the BEST answer.
After the initial installation the First Time Configuration Wizard should be run. Select the BEST answer.
Question 13
- (Exam Topic 4)
Fill in the blank: In Security Gateways R75 and above, SIC uses _____ for encryption.
Fill in the blank: In Security Gateways R75 and above, SIC uses _____ for encryption.
Question 14
- (Exam Topic 3)
The CPD daemon is a Firewall Kernel Process that does NOT do which of the following?
The CPD daemon is a Firewall Kernel Process that does NOT do which of the following?
Question 15
- (Exam Topic 3)
What are types of Check Point APIs available currently as part of R80.10 code?
What are types of Check Point APIs available currently as part of R80.10 code?
Question 16
- (Exam Topic 1)
Which of the following is NOT an integral part of VPN communication within a network?
Which of the following is NOT an integral part of VPN communication within a network?
Question 17
- (Exam Topic 3)
Which remote Access Solution is clientless?
Which remote Access Solution is clientless?
Question 18
- (Exam Topic 1)
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server. While configuring the VPN community to specify the pre-shared secret the administrator found that the check box to enable pre-shared secret is shared and cannot be enabled. Why does it not allow him to specify the pre-shared secret?
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server. While configuring the VPN community to specify the pre-shared secret the administrator found that the check box to enable pre-shared secret is shared and cannot be enabled. Why does it not allow him to specify the pre-shared secret?
Question 19
- (Exam Topic 1)
Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
Question 20
- (Exam Topic 4)
Which two Identity Awareness commands are used to support identity sharing?
Which two Identity Awareness commands are used to support identity sharing?
Question 21
- (Exam Topic 3)
Your company enforces a strict change control policy. Which of the following would be MOST effective for quickly dropping an attacker's specific active connection?
Your company enforces a strict change control policy. Which of the following would be MOST effective for quickly dropping an attacker's specific active connection?
Question 22
- (Exam Topic 1)
What does ExternalZone represent in the presented rule?
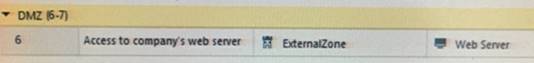
What does ExternalZone represent in the presented rule?

Question 23
- (Exam Topic 1)
Which feature is NOT provided by all Check Point Mobile Access solutions?
Which feature is NOT provided by all Check Point Mobile Access solutions?