30 October, 2021
The Secret Of Check-Point 156-315.80 Free Question
It is impossible to pass Check-Point 156-315.80 exam without any help in the short term. Come to Certleader soon and find the most advanced, correct and guaranteed Check-Point 156-315.80 practice questions. You will get a surprising result by our Avant-garde Check Point Certified Security Expert - R80 practice guides.
Question 1
Why would an administrator see the message below?
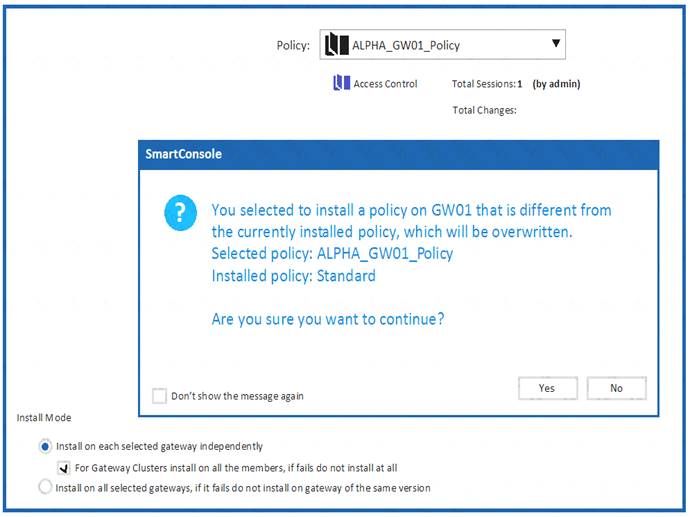

Question 2
Which command is used to set the CCP protocol to Multicast?
Question 3
To fully enable Dynamic Dispatcher on a Security Gateway:
Question 4
Your manager asked you to check the status of SecureXL, and its enabled templates and features. What command will you use to provide such information to manager?
Question 5
You are investigating issues with to gateway cluster members are not able to establish the first initial cluster synchronization. What service is used by the FWD daemon to do a Full Synchronization?
Question 6
From SecureXL perspective, what are the tree paths of traffic flow:
Question 7
Fill in the blank: The command _______ provides the most complete restoration of a R80 configuration.
Question 8
When gathering information about a gateway using CPINFO, what information is included or excluded when using the “-x” parameter?
Question 9
In SmartConsole, objects are used to represent physical and virtual network components and also some logical components. These objects are divided into several categories. Which of the following is NOT an objects category?
Question 10
To help SmartEvent determine whether events originated internally or externally you must define using the Initial Settings under General Settings in the Policy Tab. How many options are available to calculate the traffic direction?
Question 11
What is correct statement about Security Gateway and Security Management Server failover in Check Point R80.X in terms of Check Point Redundancy driven solution?
Question 12
The Event List within the Event tab contains:
Question 13
On R80.10 the IPS Blade is managed by:
Question 14
Under which file is the proxy arp configuration stored?
Question 15
Which of the following describes how Threat Extraction functions?
Question 16
What is the minimum amount of RAM needed for a Threat Prevention Appliance?
Question 17
SandBlast has several functional components that work together to ensure that attacks are prevented in real-time. Which the following is NOT part of the SandBlast component?
Question 18
The _______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
