16 November, 2020
The Secret Of Fortinet NSE7_EFW-6.0 Free Practice Exam
Master the NSE7_EFW-6.0 Fortinet NSE 7 - Enterprise Firewall 6.0 content and be ready for exam day success quickly with this Exambible NSE7_EFW-6.0 exam answers. We guarantee it!We make it a reality and give you real NSE7_EFW-6.0 questions in our Fortinet NSE7_EFW-6.0 braindumps.Latest 100% VALID Fortinet NSE7_EFW-6.0 Exam Questions Dumps at below page. You can use our Fortinet NSE7_EFW-6.0 braindumps and pass your exam.
Online Fortinet NSE7_EFW-6.0 free dumps demo Below:
Question 1
An LDAP user cannot authenticate against a FortiGate device. Examine the real time debug output shown in the exhibit when the user attempted the authentication; then answer the question below.


Based on the output in the exhibit, what can cause this authentication problem?


Based on the output in the exhibit, what can cause this authentication problem?
Question 2
An administrator has decreased all the TCP session timers to optimize the FortiGate memory usage. However, after the changes, one network application started to have problems. During the troubleshooting, the administrator noticed that the FortiGate deletes the sessions after the clients send the SYN packets, and before the arrival of the SYN/ACKs. When the SYN/ACK packets arrive to the FortiGate, the unit has already deleted the respective sessions. Which TCP session timer must be increased to fix this problem?
Question 3
An administrator has configured two FortiGate devices for an HA cluster. While testing the HA failover, the administrator noticed that some of the switches in the network continue to send traffic to the former primary unit. The administrator decides to enable the setting link-failed-signal to fix the problem. Which statement is correct regarding this command?
Question 4
When does a RADIUS server send an Access-Challenge packet?
Question 5
Which real time debug should an administrator enable to troubleshoot RADIUS authentication problems?
Question 6
What events are recorded in the crashlogs of a FortiGate device? (Choose two.)
Question 7
The CLI command set intelligent-mode controls the IPS engine’s adaptive scanning behavior. Which of the following statements describes IPS adaptive scanning?
Question 8
Examine the output from the BGP real time debug shown in the exhibit, then the answer the question below:

Which statements are true regarding the output in the exhibit? (Choose two.)

Which statements are true regarding the output in the exhibit? (Choose two.)
Question 9
Which statement is true regarding File description (FD) conserve mode?
Question 10
View the exhibit, which contains a session entry, and then answer the question below.

Which statement is correct regarding this session?

Which statement is correct regarding this session?
Question 11
What configuration settings change the behavior for content-inspected traffic while FortiGate is in conserve mode? (Choose two.)
Question 12
An administrator has configured a FortiGate device with two VDOMs: root and internal. The administrator has also created and inter-VDOM link that connects both VDOMs. The objective is to have each VDOM advertise some routes to the other VDOM via OSPF through the inter-VDOM link. What OSPF configuration settings must match in both VDOMs to have the OSPF adjacency successfully forming? (Choose three.)
Question 13
What global configuration setting changes the behavior for content-inspected traffic while FortiGate is in system conserve mode?
Question 14
What does the dirty flag mean in a FortiGate session?
Question 15
View the exhibit, which contains the output of a BGP debug command, and then answer the question below.

Which of the following statements about the exhibit are true? (Choose two.)

Which of the following statements about the exhibit are true? (Choose two.)
Question 16
Which the following events can trigger the election of a new primary unit in a HA cluster? (Choose two.)
Question 17
View the following FortiGate configuration.

All traffic to the Internet currently egresses from port1. The exhibit shows partial session information for Internet traffic from a user on the internal network:
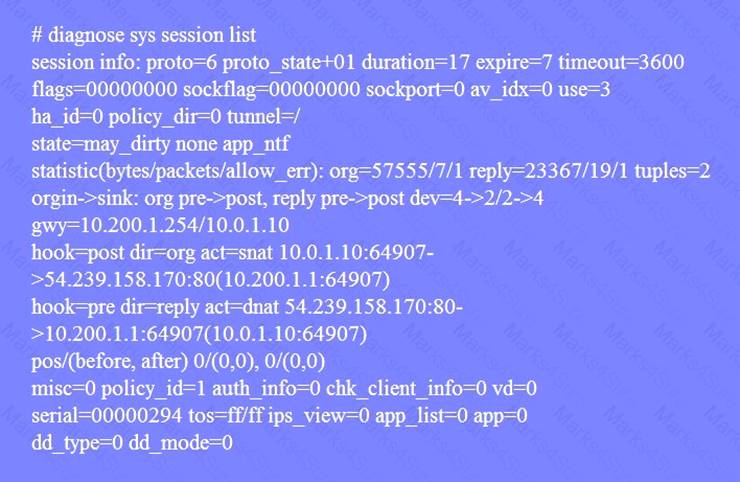
If the priority on route ID 1 were changed from 5 to 20, what would happen to traffic matching that user’s session?

All traffic to the Internet currently egresses from port1. The exhibit shows partial session information for Internet traffic from a user on the internal network:

If the priority on route ID 1 were changed from 5 to 20, what would happen to traffic matching that user’s session?
Question 18
View the exhibit, which contains the partial output of an IKE real-time debug, and then answer the question below.
ike 0: comes 10.0.0.2:500->10.0.0.1:500, ifindex=7....
ike 0: IKEv1 exchange=Aggressive id=baf47d0988e9237f/2f405ef3952f6fda len=430 ike 0: in
BAF47D0988E9237F2F405EF3952F6FDA0110040000000000000001AE0400003C0000000100000001000000
ike 0:RemoteSite:4: initiator: aggressive mode get 1st response...
ike 0:RemoteSite:4: VID RFC 3947 4A131c81070358455C5728F20E95452F ike 0:RemoteSite:4: VID DPD AFCAD71368A1F1C96B8696FC77570100
ike 0:RemoteSite:4: VID FORTIGATE 8299031757A36082C6A621DE000502D7
ike 0:RemoteSite:4: peer is FortiGate/Fortios (v5 b727)
ike 0:RemoteSite:4: VID FRAGMENTATION 4048B7D56EBCE88525E7DE7F00D6C2D3
ike 0:RemoteSite:4: VID FRAGMENTATION 4048B7D56EBCE88525E7DE7F00D6C2D3C0000000
ike 0:RemoteSite:4: received peer identifier FQDN ‘remore’ ike 0:RemoteSite:4: negotiation result
ike 0:RemoteSite:4: proposal id = 1:
ike 0:RemoteSite:4: protocol id = ISAKMP: ike 0:RemoteSite:4: trans_id = KEY_IKE.
ike 0:RemoteSite:4: encapsulation = IKE/none
ike 0:RemoteSite:4: type=OAKLEY_ENCRYPT_ALG, val=AES_CBC, key –len=128 ike 0:RemoteSite:4: type=OAKLEY_HASH_ALG, val=SHA.
ike 0:RemoteSite:4: type-AUTH_METHOD, val=PRESHARED_KEY. ike 0:RemoteSite:4: type=OAKLEY_GROUP, val=MODP1024.
ike 0:RemoteSite:4: ISAKMP SA lifetime=86400
ike 0:RemoteSite:4: ISAKMP SA baf47d0988e9237f/2f405ef3952f6fda key 16:
B25B6C9384D8BDB24E3DA3DC90CF5E73
ike 0:RemoteSite:4: PSK authentication succeeded ike 0:RemoteSite:4: authentication OK
ike 0:RemoteSite:4: add INITIAL-CONTACT
ike 0:RemoteSite:4: enc BAF47D0988E9237F405EF3952F6FDA081004010000000000000080140000181F2E48BFD8E9D603F
ike 0:RemoteSite:4: out BAF47D0988E9237F405EF3952F6FDA08100401000000000000008C2E3FC9BA061816A396F009A12
ike 0:RemoteSite:4: sent IKE msg (agg_i2send): 10.0.0.1:500-10.0.0.2:500, len=140, id=baf47d0988e9237f/2 ike 0:RemoteSite:4: established IKE SA baf47d0988e9237f/2f405ef3952f6fda
Which statements about this debug output are correct? (Choose two.)
ike 0: comes 10.0.0.2:500->10.0.0.1:500, ifindex=7....
ike 0: IKEv1 exchange=Aggressive id=baf47d0988e9237f/2f405ef3952f6fda len=430 ike 0: in
BAF47D0988E9237F2F405EF3952F6FDA0110040000000000000001AE0400003C0000000100000001000000
ike 0:RemoteSite:4: initiator: aggressive mode get 1st response...
ike 0:RemoteSite:4: VID RFC 3947 4A131c81070358455C5728F20E95452F ike 0:RemoteSite:4: VID DPD AFCAD71368A1F1C96B8696FC77570100
ike 0:RemoteSite:4: VID FORTIGATE 8299031757A36082C6A621DE000502D7
ike 0:RemoteSite:4: peer is FortiGate/Fortios (v5 b727)
ike 0:RemoteSite:4: VID FRAGMENTATION 4048B7D56EBCE88525E7DE7F00D6C2D3
ike 0:RemoteSite:4: VID FRAGMENTATION 4048B7D56EBCE88525E7DE7F00D6C2D3C0000000
ike 0:RemoteSite:4: received peer identifier FQDN ‘remore’ ike 0:RemoteSite:4: negotiation result
ike 0:RemoteSite:4: proposal id = 1:
ike 0:RemoteSite:4: protocol id = ISAKMP: ike 0:RemoteSite:4: trans_id = KEY_IKE.
ike 0:RemoteSite:4: encapsulation = IKE/none
ike 0:RemoteSite:4: type=OAKLEY_ENCRYPT_ALG, val=AES_CBC, key –len=128 ike 0:RemoteSite:4: type=OAKLEY_HASH_ALG, val=SHA.
ike 0:RemoteSite:4: type-AUTH_METHOD, val=PRESHARED_KEY. ike 0:RemoteSite:4: type=OAKLEY_GROUP, val=MODP1024.
ike 0:RemoteSite:4: ISAKMP SA lifetime=86400
ike 0:RemoteSite:4: ISAKMP SA baf47d0988e9237f/2f405ef3952f6fda key 16:
B25B6C9384D8BDB24E3DA3DC90CF5E73
ike 0:RemoteSite:4: PSK authentication succeeded ike 0:RemoteSite:4: authentication OK
ike 0:RemoteSite:4: add INITIAL-CONTACT
ike 0:RemoteSite:4: enc BAF47D0988E9237F405EF3952F6FDA081004010000000000000080140000181F2E48BFD8E9D603F
ike 0:RemoteSite:4: out BAF47D0988E9237F405EF3952F6FDA08100401000000000000008C2E3FC9BA061816A396F009A12
ike 0:RemoteSite:4: sent IKE msg (agg_i2send): 10.0.0.1:500-10.0.0.2:500, len=140, id=baf47d0988e9237f/2 ike 0:RemoteSite:4: established IKE SA baf47d0988e9237f/2f405ef3952f6fda
Which statements about this debug output are correct? (Choose two.)
Question 19
Examine the output of the ‘diagnose ips anomaly list’ command shown in the exhibit; then answer the question below.

Which IP addresses are included in the output of this command?

Which IP addresses are included in the output of this command?
Question 20
A FortiGate device has the following LDAP configuration:

The LDAP user student cannot authenticate. The exhibit shows the output of the authentication real time debug while testing the student account:

Based on the above output, what FortiGate LDAP settings must the administer check? (Choose two.)

The LDAP user student cannot authenticate. The exhibit shows the output of the authentication real time debug while testing the student account:

Based on the above output, what FortiGate LDAP settings must the administer check? (Choose two.)
Question 21
View the exhibit, which contains the partial output of an IKE real time debug, and then answer the question below.

The administrator does not have access to the remote gateway. Based on the debug output, what configuration changes can the administrator make to the local gateway to resolve the phase 1 negotiation error?

The administrator does not have access to the remote gateway. Based on the debug output, what configuration changes can the administrator make to the local gateway to resolve the phase 1 negotiation error?
Question 22
View the exhibit, which contains a screenshot of some phase-1 settings, and then answer the question below.
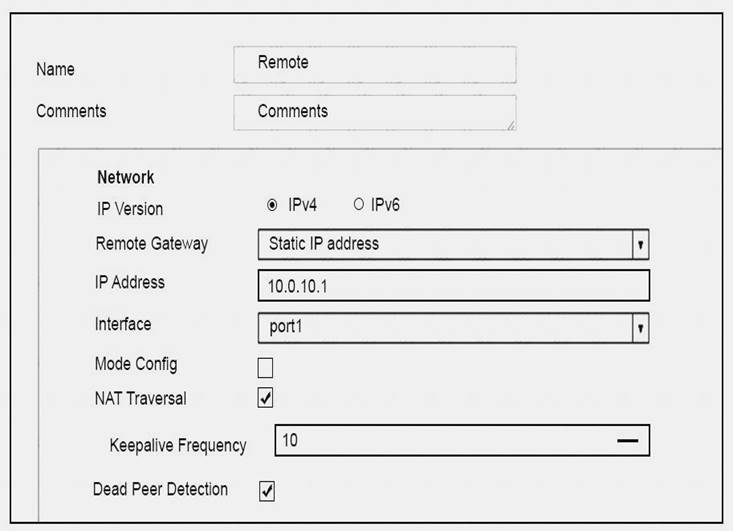
The VPN is up, and DPD packets are being exchanged between both IPsec gateways; however, traffic cannot pass through the tunnel. To diagnose, the administrator enters these CLI commands:

However, the IKE real time debug does not show any output. Why?

The VPN is up, and DPD packets are being exchanged between both IPsec gateways; however, traffic cannot pass through the tunnel. To diagnose, the administrator enters these CLI commands:

However, the IKE real time debug does not show any output. Why?
