07 November, 2023
Top Tips Of Down To Date CCST-Networking Free Dumps
we provide Tested Cisco CCST-Networking exams which are the best for clearing CCST-Networking test, and to get certified by Cisco Cisco Certified Support Technician (CCST) NetworkingExam. The CCST-Networking Questions & Answers covers all the knowledge points of the real CCST-Networking exam. Crack your Cisco CCST-Networking Exam with latest dumps, guaranteed!
Question 1
Which two statements are true about the IPv4 address of the default gateway configured on a host? (Choose 2.)
Note: You will receive partial credit for each correct selection.
Note: You will receive partial credit for each correct selection.
Question 2
A Cisco PoE switch is shown in the following image. Which type of port will provide both data connectivity and power to an IP phone?


Question 3
DRAG DROP
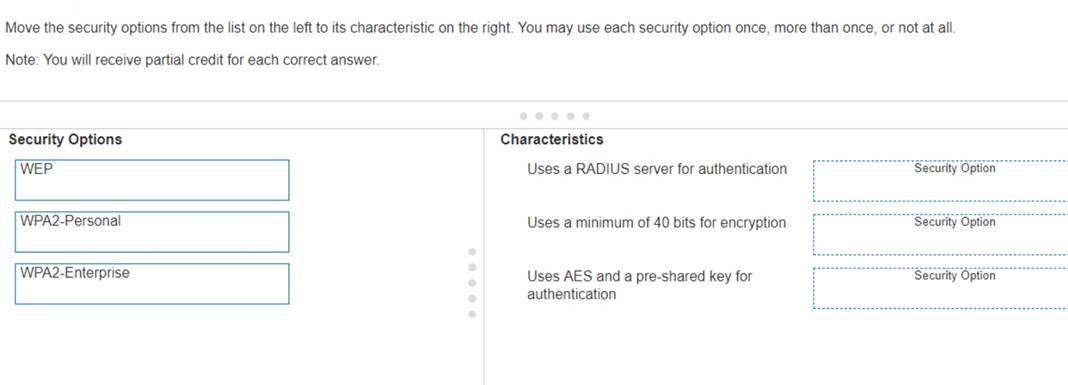
Move the security options from the list on the left to its characteristic on the right. You may use each security option once, more than once, or not at all.
Note: You will receive partial credit for each correct answer.
Solution:
The correct matching of the security options to their characteristics is as follows:
✑ WPA2-Enterprise: Uses a RADIUS server for authentication
✑ WEP: Uses a minimum of 40 bits for encryption
✑ WPA2-Personal: Uses AES and a pre-shared key for authentication Here??s why each security option matches the characteristic:
✑ WPA2-Enterpriseuses a RADIUS server for authentication, which provides centralized Authentication, Authorization, and Accounting (AAA) management for users who connect and use a network service.
✑ WEP (Wired Equivalent Privacy)is an outdated security protocol that uses a minimum of 40 bits for encryption (and up to 104 bits), which is relatively weak by today??s standards.
✑ WPA2-Personal(Wi-Fi Protected Access 2 - Personal) uses the Advanced Encryption Standard (AES) for encryption and a pre-shared key (PSK) for authentication, which is shared among users to access the network.
These security options are essential for protecting wireless networks from unauthorized access and ensuring data privacy.
Does this meet the goal?
Move the security options from the list on the left to its characteristic on the right. You may use each security option once, more than once, or not at all.
Note: You will receive partial credit for each correct answer.

Solution:
The correct matching of the security options to their characteristics is as follows:
✑ WPA2-Enterprise: Uses a RADIUS server for authentication
✑ WEP: Uses a minimum of 40 bits for encryption
✑ WPA2-Personal: Uses AES and a pre-shared key for authentication Here??s why each security option matches the characteristic:
✑ WPA2-Enterpriseuses a RADIUS server for authentication, which provides centralized Authentication, Authorization, and Accounting (AAA) management for users who connect and use a network service.
✑ WEP (Wired Equivalent Privacy)is an outdated security protocol that uses a minimum of 40 bits for encryption (and up to 104 bits), which is relatively weak by today??s standards.
✑ WPA2-Personal(Wi-Fi Protected Access 2 - Personal) uses the Advanced Encryption Standard (AES) for encryption and a pre-shared key (PSK) for authentication, which is shared among users to access the network.
These security options are essential for protecting wireless networks from unauthorized access and ensuring data privacy.
Does this meet the goal?
Question 4
DRAG DROP
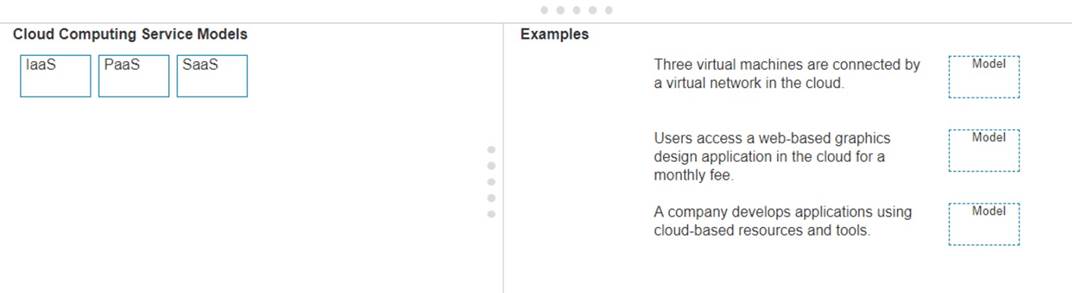
Move each cloud computing service model from the list on the left to the correct example on the right
Note: You will receive partial credit for each correct answer.
Solution:
✑ Three virtual machines are connected by a virtual network in the cloud.
✑ Users access a web-based graphics design application in the cloud for a monthly fee.
✑ A company develops applications using cloud-based resources and tools.
✑ IaaS (Infrastructure as a Service): Provides virtualized hardware resources that customers can use to build their own computing environments.
✑ PaaS (Platform as a Service): Offers a platform with tools and services to develop,
test, and deploy applications.
✑ SaaS (Software as a Service): Delivers fully functional applications over the internet that users can access and use without managing the underlying infrastructure.
References:
✑ Cloud Service Models: Understanding IaaS, PaaS, SaaS
✑ NIST Definition of Cloud Computing:NIST Cloud Computing
Does this meet the goal?
Move each cloud computing service model from the list on the left to the correct example on the right
Note: You will receive partial credit for each correct answer.

Solution:
✑ Three virtual machines are connected by a virtual network in the cloud.
✑ Users access a web-based graphics design application in the cloud for a monthly fee.
✑ A company develops applications using cloud-based resources and tools.
✑ IaaS (Infrastructure as a Service): Provides virtualized hardware resources that customers can use to build their own computing environments.
✑ PaaS (Platform as a Service): Offers a platform with tools and services to develop,
test, and deploy applications.
✑ SaaS (Software as a Service): Delivers fully functional applications over the internet that users can access and use without managing the underlying infrastructure.
References:
✑ Cloud Service Models: Understanding IaaS, PaaS, SaaS
✑ NIST Definition of Cloud Computing:NIST Cloud Computing
Does this meet the goal?
Question 5
An engineer configured a new VLAN named VLAN2 for the Data Center team. When the teamtries to ping addresses outside VLAN2 from a computer in
VLAN2, they are unable to reach them. What should the engineer configure?
VLAN2, they are unable to reach them. What should the engineer configure?
Question 6
DRAG DROP
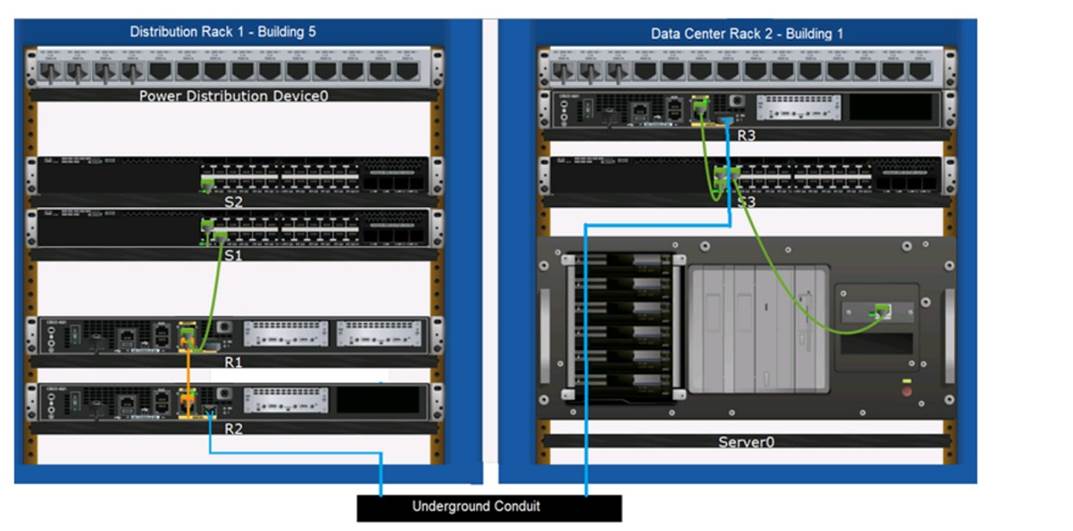
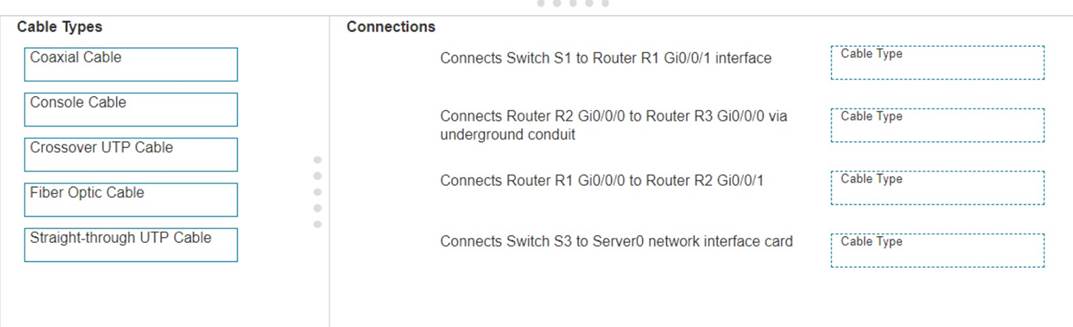
Examine the connections shown in the following image. Move the cable types on the right to the appropriate connection description on the left. You may
use each cable type more than once or not at all.
Solution:
Based on the image description provided, here are the cable types matched with the appropriate connection descriptions:
Connects Switch S1 to Router R1 Gi0/0/1 interfaceCable Type: = Straight-through UTP Cable
Connects Router R2 Gi0/0/0 to Router R3 Gi0/0/0 via underground conduitCable Type
: = Fiber Optic Cable
Connects Router R1 Gi0/0/0 to Router R2 Gi0/0/1Cable Type: = Crossover UTP Cable
Connects Switch S3 to Server0 network interface cardCable Type: = Straight-through UTP Cable
The choices are based on standard networking practices where:
✑ Straight-through UTP cablesare typically used to connect a switch to a router or a network interface card.
✑ Fiber optic cablesare ideal for long-distance, high-speed data transmission, such as connections through an underground conduit.
✑ Crossover UTP cablesare used to connect similar devices, such as router-to-router connections.
These matches are consistent with the color-coded cables in the image: green for switch connections, yellow for router-to-router connections within the same rack, and blue for inter-rack connections. The use of these cables follows the Ethernet cabling standards.
✑ Connects Switch S1 to Router R1 Gi0/0/1 interface:
✑ Connects Router R2 Gi0/0/0 to Router R3 Gi0/0/0 via underground conduit:
✑ Connects Router R1 Gi0/0/0 to Router R2 Gi0/0/1:
✑ Connects Switch S3 to Server0 network interface card:
✑ Straight-through UTP Cable: Used to connect different devices (e.g., switch to router, switch to server).
✑ Crossover UTP Cable: Used to connect similar devices directly (e.g., router to
router, switch to switch).
✑ Fiber Optic Cable: Used for long-distance and high-speed connections, often between buildings or data centers.
References:
✑ Network Cable Types and Uses: Cisco Network Cables
✑ Understanding Ethernet Cabling: Ethernet Cable Guide
Does this meet the goal?
Examine the connections shown in the following image. Move the cable types on the right to the appropriate connection description on the left. You may
use each cable type more than once or not at all.


Solution:
Based on the image description provided, here are the cable types matched with the appropriate connection descriptions:
Connects Switch S1 to Router R1 Gi0/0/1 interfaceCable Type: = Straight-through UTP Cable
Connects Router R2 Gi0/0/0 to Router R3 Gi0/0/0 via underground conduitCable Type
: = Fiber Optic Cable
Connects Router R1 Gi0/0/0 to Router R2 Gi0/0/1Cable Type: = Crossover UTP Cable
Connects Switch S3 to Server0 network interface cardCable Type: = Straight-through UTP Cable
The choices are based on standard networking practices where:
✑ Straight-through UTP cablesare typically used to connect a switch to a router or a network interface card.
✑ Fiber optic cablesare ideal for long-distance, high-speed data transmission, such as connections through an underground conduit.
✑ Crossover UTP cablesare used to connect similar devices, such as router-to-router connections.
These matches are consistent with the color-coded cables in the image: green for switch connections, yellow for router-to-router connections within the same rack, and blue for inter-rack connections. The use of these cables follows the Ethernet cabling standards.
✑ Connects Switch S1 to Router R1 Gi0/0/1 interface:
✑ Connects Router R2 Gi0/0/0 to Router R3 Gi0/0/0 via underground conduit:
✑ Connects Router R1 Gi0/0/0 to Router R2 Gi0/0/1:
✑ Connects Switch S3 to Server0 network interface card:
✑ Straight-through UTP Cable: Used to connect different devices (e.g., switch to router, switch to server).
✑ Crossover UTP Cable: Used to connect similar devices directly (e.g., router to
router, switch to switch).
✑ Fiber Optic Cable: Used for long-distance and high-speed connections, often between buildings or data centers.
References:
✑ Network Cable Types and Uses: Cisco Network Cables
✑ Understanding Ethernet Cabling: Ethernet Cable Guide
Does this meet the goal?
Question 7
Examine the following output:
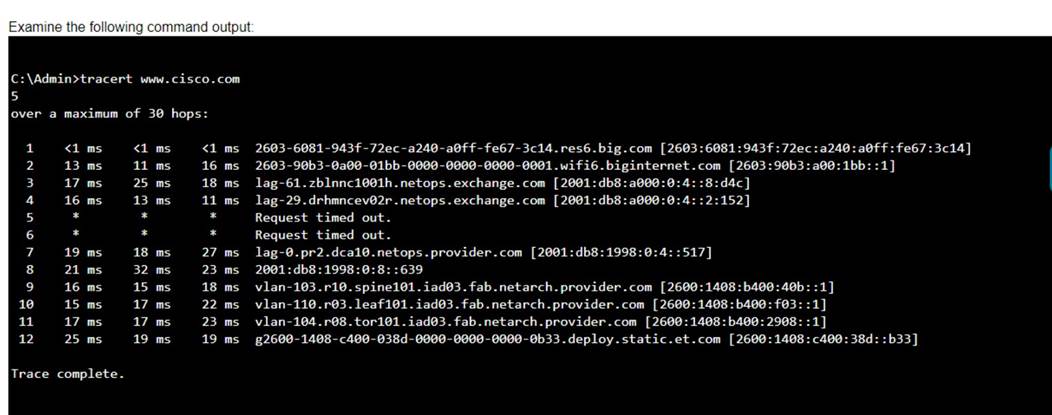
Which two conclusions can you make from the output of the tracert command? (Choose 2.) Note: You will receive partial credit for each correct answer.

Which two conclusions can you make from the output of the tracert command? (Choose 2.) Note: You will receive partial credit for each correct answer.
Question 8
Which standard contains the specifications for Wi-Fi networks?
Question 9
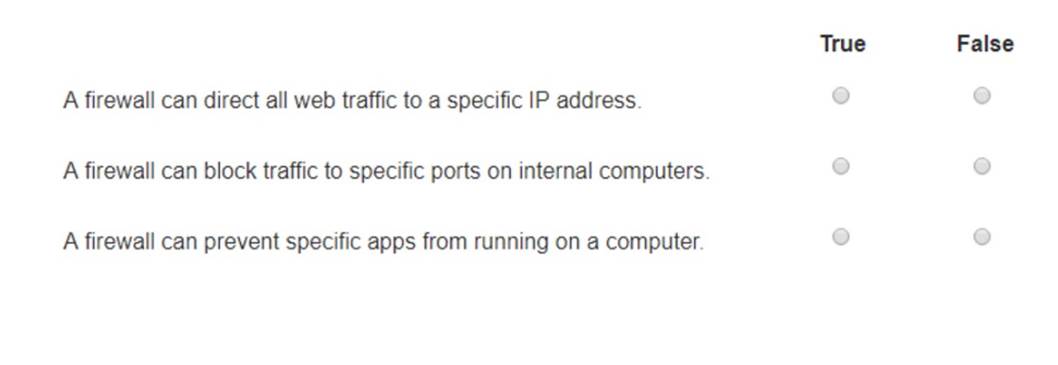
HOTSPOT
You plan to use a network firewall to protect computers at a small office. For each statement about firewalls, select True or False.
Note: You will receive partial credit for each correct selection.
Solution:
✑ A firewall can direct all web traffic to a specific IP address.
✑ A firewall can block traffic to specific ports on internal computers.
✑ A firewall can prevent specific apps from running on a computer.
✑ Directing Web Traffic: Firewalls can manage traffic redirection using NAT and port forwarding rules to route web traffic to designated servers or devices within the network.
✑ Blocking Specific Ports: Firewalls can enforce security policies by blocking or
allowing traffic based on port numbers, ensuring that only permitted traffic reaches internal systems.
✑ Application Control: While firewalls manage network traffic, preventing applications
from running typically requires software specifically designed for endpoint protection and application management.
References:
✑ Understanding Firewalls: Firewall Capabilities
✑ Network Security Best Practices: Network Security Guide
Does this meet the goal?
You plan to use a network firewall to protect computers at a small office. For each statement about firewalls, select True or False.
Note: You will receive partial credit for each correct selection.

Solution:
✑ A firewall can direct all web traffic to a specific IP address.
✑ A firewall can block traffic to specific ports on internal computers.
✑ A firewall can prevent specific apps from running on a computer.
✑ Directing Web Traffic: Firewalls can manage traffic redirection using NAT and port forwarding rules to route web traffic to designated servers or devices within the network.
✑ Blocking Specific Ports: Firewalls can enforce security policies by blocking or
allowing traffic based on port numbers, ensuring that only permitted traffic reaches internal systems.
✑ Application Control: While firewalls manage network traffic, preventing applications
from running typically requires software specifically designed for endpoint protection and application management.
References:
✑ Understanding Firewalls: Firewall Capabilities
✑ Network Security Best Practices: Network Security Guide
Does this meet the goal?
Question 10
You want to store files that will be accessible by every user on your network. Which endpoint device do you need?
Question 11
A local company requires two networks in two new buildings. The addresses used in these networksmust be in the private network range.
Which two address ranges should the company use? (Choose 2.) Note: You will receive partial credit for each correct selection.
Which two address ranges should the company use? (Choose 2.) Note: You will receive partial credit for each correct selection.
Question 12
Which protocol allows you to securely upload files to another computer on the internet?
