11 February, 2020
Understanding Cisco Cybersecurity Fundamentals 210-250 Practice Exam
Act now and download your Cisco 210-250 test today! Do not waste time for the worthless Cisco 210-250 tutorials. Download Most recent Cisco Understanding Cisco Cybersecurity Fundamentals exam with real questions and answers and begin to learn Cisco 210-250 with a classic professional.
Also have 210-250 free dumps questions for you:
Question 1
which security principle is violated by running all processes as root/admin
Question 2
In which case should an employee return his laptop to the organization?
Question 3
Which definition of a process in Windows is true?
Question 4
Which term represents the chronological record of how evidence was collected- analyzed, preserved, and transferred?
Question 5
According to the common vulnerability scoring system, which term is associated with scoring multiple vulnerabilities that are exploit in the course of a single attack?
Question 6
Which hash algorithm is the weakest?
Question 7
Which term represents a weakness in a system that could lead to the system being compromised?
Question 8
Which purpose of a security risk assessment is true?
Question 9
Which option is a purpose of port scanning?
Question 10
What are two Features of NGFW:
Question 11
Which definition of a Linux daemon is true?
Question 12
How many broadcast domains are created if three hosts are connected to a Layer 2 switch in full-duplex mode?
Question 13
which protocol helps to synchronizes and correlate events across multiple network devices:
Question 14
Which of the following is true about heuristic-based algorithms?
Question 15
Refer to the exhibit.
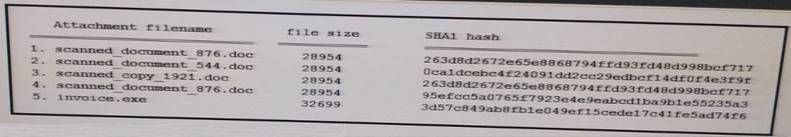
During an analysis this list of email attachments is found. Which files contain the same content?

During an analysis this list of email attachments is found. Which files contain the same content?
Question 16
What does the sum of the risks presented by an application represent for that application?
Question 17
What is one of the advantages of the mandatory access control (MAC) model?
Question 18
What Does the sum of the risk presented by an application represent for that application ?
Question 19
Which two options are recognized forms of phishing? (Choose two)
Question 20
Which statement about digitally signing a document is true?
Question 21
Which protocol is expected to have NTP a user agent, host, and referrer headers in a packet capture?
Question 22
Which two protocols are often used for DDoS amplification attacks (choose two)
Question 23
Which option is true when using the traffic mirror feature in a switch?
