30 June, 2020
Up To The Minute 350-901 Braindumps For Developing Applications Using Cisco Core Platforms & APIs Certification
It is impossible to pass Cisco 350-901 exam without any help in the short term. Come to Passleader soon and find the most advanced, correct and guaranteed Cisco 350-901 practice questions. You will get a surprising result by our Far out Developing Applications using Cisco Core Platforms & APIs practice guides.
Online Cisco 350-901 free dumps demo Below:
Question 1
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
Question 2
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct. Which action accomplishes this task?
Question 3
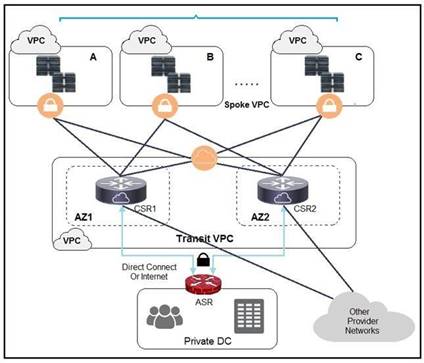
Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC. Which two statements describe the benefits of this approach? (Choose two.)
Question 4
An application is hosted on Google Kubernetes Engine. A new JavaScript module is created to work with the existing application. Which task is mandatory to make the code ready to deploy?
Question 5
User report that they can no longer process transactions with the online ordering application, and the logging dashboard is displaying these messages.
Fri Jan 10 19:37:31.123 EST 2020 [FRONTEND] INFO: Incoming request to add item to cart from user 45834534858 Fri Jan 10 19:37:31 247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31 250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused What is causing the problem seen in these log messages?
Fri Jan 10 19:37:31.123 EST 2020 [FRONTEND] INFO: Incoming request to add item to cart from user 45834534858 Fri Jan 10 19:37:31 247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31 250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused What is causing the problem seen in these log messages?
Question 6
A container running a Python script is failing when it reaches the integration testing phase of the CI/CD process. The code has been reviewed thoroughly and the build process works on this container and all other containers pass unit and integration testing.
What should be verified to resolve the issue?
What should be verified to resolve the issue?
Question 7
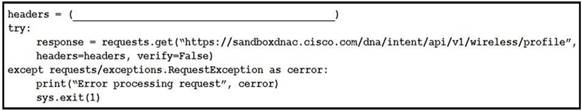
Refer to the exhibit. Which code snippet is required in the headers to successfully authorize wireless information from Cisco DNA Center?
Question 8
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances.
Which two actions can improve the design of the application to identify the faults? (Choose two.)
Which two actions can improve the design of the application to identify the faults? (Choose two.)
Question 9
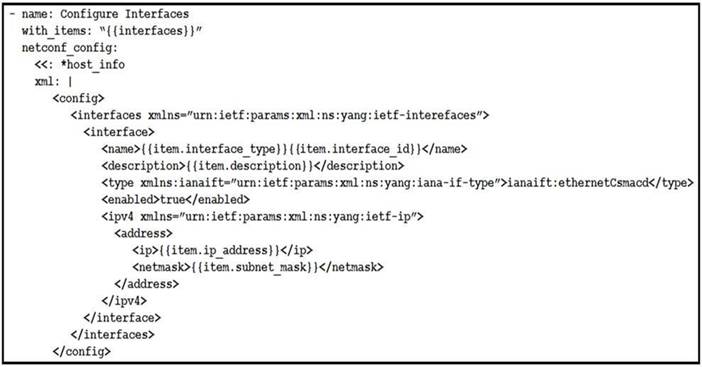
Refer to the exhibit. The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?
Question 10
Refer to the exhibit. Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
Question 11
Which two statements about a stateless application are true? (Choose two.)
Question 12
On a Cisco Catalyst 9300 Series Switch, the guest shell is being used to create a service within a container. Which change is needed to allow the service to have external access?
Question 13
The response from a server includes the header ETag: W/”7eb8b94419e371767916ef13e0d6e63d”. Which statement is true?
Question 14
An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
Question 15
Which database type should be used with highly structured data and provides support for ACID transactions?
Question 16
AppGigabitEthernet interface is used as data port for a container on a Cisco Catalyst 9000 Series Switch. Which two interface configuration options should be used? (Choose two.)
Question 17
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority. Which approach must be taken to secure API keys and passwords?
Question 18
DRAG DROP
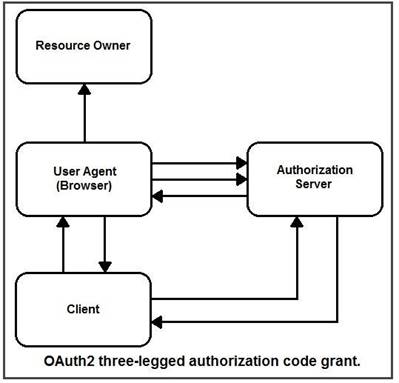
Refer to the exhibit. Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
Select and Place:
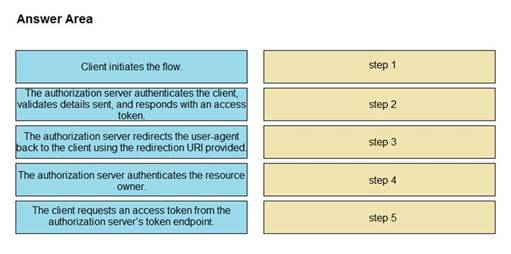
Solution:
Does this meet the goal?

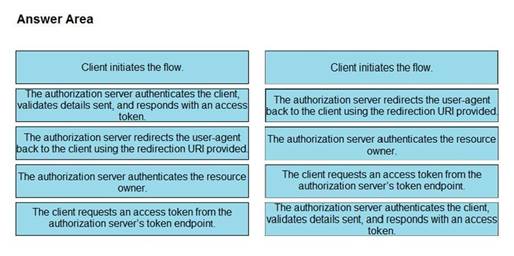
Refer to the exhibit. Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
Select and Place:

Solution:

Does this meet the goal?
Question 19
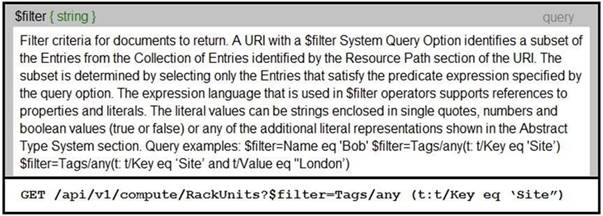
Refer to the exhibit. An Intersight API is being used to query RackUnit resources that have a tag keyword set to “Site”. What is the expected output of this command?
Question 20
Into which two areas are AppDynamics APIs categorized? (Choose two.)
Question 21
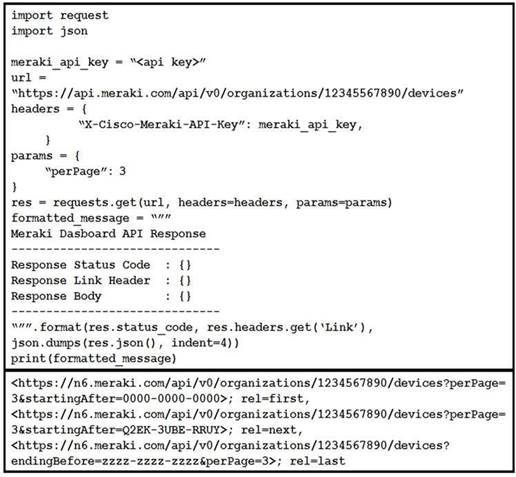
Refer to the exhibit. Which line of code must be added to this code snippet to allow an application to pull the next set of paginated items?
Question 22
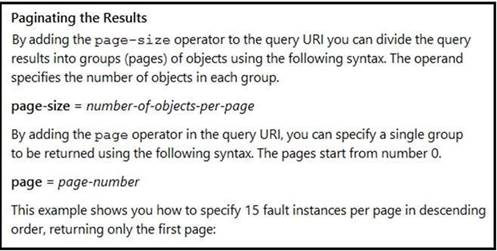
Refer to the exhibit. Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
Question 23
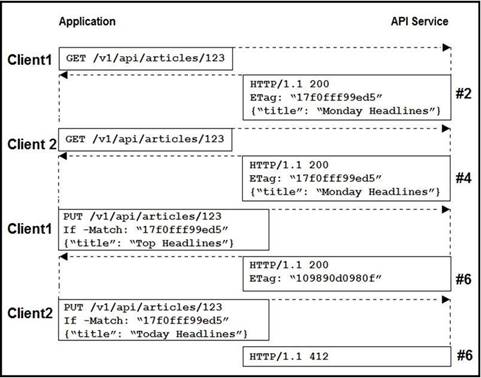
Refer to the exhibit. Two editors are concurrently updating an article’s headline from their mobile devices. What results from this scenario based on this REST API sequence?
Question 24
Which two strategies are used to protect personally identifiable information? (Choose two.)
Question 25
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
