25 July, 2021
Updated Implementing And Operating Cisco Security Core Technologies 350-701 Question
Want to know Testking 350-701 Exam practice test features? Want to lear more about Cisco Implementing and Operating Cisco Security Core Technologies certification experience? Study High quality Cisco 350-701 answers to Up to date 350-701 questions at Testking. Gat a success with an absolute guarantee to pass Cisco 350-701 (Implementing and Operating Cisco Security Core Technologies) test on your first attempt.
Free demo questions for Cisco 350-701 Exam Dumps Below:
Question 1
An engineer needs a solution for TACACS+ authentication and authorization for device administration. The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
Question 2
Refer to the exhibit.
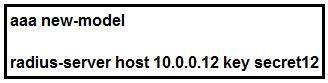
Which statement about the authentication protocol used in the configuration is true?

Which statement about the authentication protocol used in the configuration is true?
Question 3
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
Question 4
DRAG DROP
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.
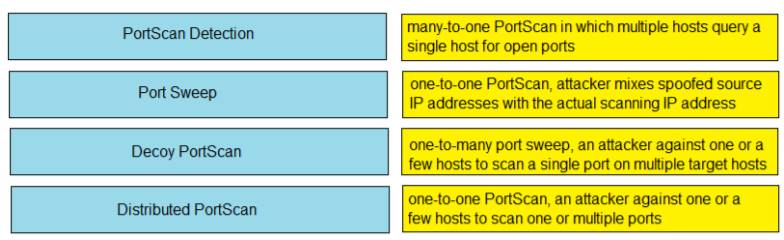
Solution:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
Does this meet the goal?
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.

Solution:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
Does this meet the goal?
Question 5
Which two capabilities does TAXII support? (Choose two.)
Question 6
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform?
Question 7
Which VPN technology can support a multivendor environment and secure traffic between sites?
Question 8
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
Question 9
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic?
Question 10
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
Question 11
Which deployment model is the most secure when considering risks to cloud adoption?
Question 12
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
Question 13
How does Cisco Umbrella archive logs to an enterprise- owned storage?
Question 14
Which API is used for Content Security?
Question 15
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
