25 November, 2019
Vivid Microsoft 70-410 Interactive Bootcamp
It is more faster and easier to pass the Microsoft 70-410 exam by using Downloadable Microsoft Installing and Configuring Windows Server 2012 questuins and answers. Immediate access to the Most up-to-date 70-410 Exam and find the same core area 70-410 questions with professionally verified answers, then PASS your exam with a high score now.
Question 1
- (Topic 1)
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed.
Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.
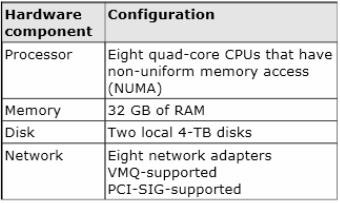
You plan to schedule a complete backup of Server1 by using Windows Server Backup. You need to ensure that the state of VM1 is saved before the backup starts.
What should you configure?
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed.
Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.

You plan to schedule a complete backup of Server1 by using Windows Server Backup. You need to ensure that the state of VM1 is saved before the backup starts.
What should you configure?
Question 2
- (Topic 2)
You perform a Server Core Installation of Windows Server 2012 R2 on a server named Server1.
You need to add a graphical user interface (GUI) to Server1. Which tool should you use?
You perform a Server Core Installation of Windows Server 2012 R2 on a server named Server1.
You need to add a graphical user interface (GUI) to Server1. Which tool should you use?
Question 3
- (Topic 2)
Your network contains an Active Directory domain named contoso.com. The network contains 500 client computers that run Windows 8. All of the client computers connect to the Internet by using a web proxy.
You deploy a server named Server1 that runs Windows Server 2012 R2. Server1 has the DNS Server server role installed.
You configure all of the client computers to use Server1 as their primary DNS server. You need to prevent Server1 from attempting to resolve Internet host names for the client
computers.
What should you do on Server1?
Your network contains an Active Directory domain named contoso.com. The network contains 500 client computers that run Windows 8. All of the client computers connect to the Internet by using a web proxy.
You deploy a server named Server1 that runs Windows Server 2012 R2. Server1 has the DNS Server server role installed.
You configure all of the client computers to use Server1 as their primary DNS server. You need to prevent Server1 from attempting to resolve Internet host names for the client
computers.
What should you do on Server1?
Question 4
- (Topic 1)
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1. Server1 runs Windows Server 2012 R2. You need to create a 3-TB virtual hard disk (VHD) on Server1.
Which tool should you use?
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1. Server1 runs Windows Server 2012 R2. You need to create a 3-TB virtual hard disk (VHD) on Server1.
Which tool should you use?
Question 5
- (Topic 2)
Your network contains an Active Directory forest named contoso.com. The forest contains five domains. All domain controllers run Windows Server 2012 R2.
The contoso.com domain contains two user accounts named Admin1 and Admin2.
You need to ensure that Admin1 and Admin2 can configure hardware and services on all of the member servers in the forest. The solution must minimize the number of privileges granted to Admin1 and Admin2.
Which built-in groups should you use?
Your network contains an Active Directory forest named contoso.com. The forest contains five domains. All domain controllers run Windows Server 2012 R2.
The contoso.com domain contains two user accounts named Admin1 and Admin2.
You need to ensure that Admin1 and Admin2 can configure hardware and services on all of the member servers in the forest. The solution must minimize the number of privileges granted to Admin1 and Admin2.
Which built-in groups should you use?
Question 6
DRAG DROP - (Topic 4)
You plan to deploy a DHCP server that will support four subnets. The subnets will be configured as shown in the following table:
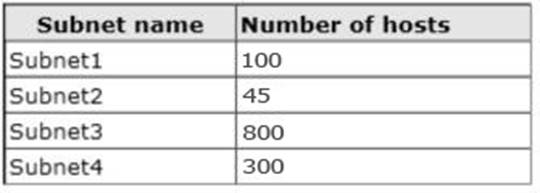
You need to identify which network ID you should use for each subnet. What should you identify? To answer, drag the appropriate network ID to the each subnet in the answer area.
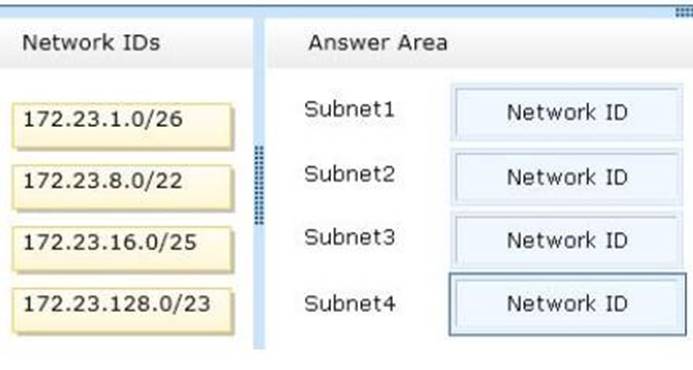
Solution:
Does this meet the goal?
You plan to deploy a DHCP server that will support four subnets. The subnets will be configured as shown in the following table:

You need to identify which network ID you should use for each subnet. What should you identify? To answer, drag the appropriate network ID to the each subnet in the answer area.

Solution:

Does this meet the goal?
Question 7
- (Topic 4)
You only want to share a printer with Group1, administrators, central owner and operators (pick 2 answers).
You only want to share a printer with Group1, administrators, central owner and operators (pick 2 answers).
Question 8
- (Topic 2)
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. The domain contains a standalone server named Server2 that is located in a perimeter network. Both servers run the default installation of Windows Server 2012 R2.
You need to manage Server2 remotely from Server1. What should you do?
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. The domain contains a standalone server named Server2 that is located in a perimeter network. Both servers run the default installation of Windows Server 2012 R2.
You need to manage Server2 remotely from Server1. What should you do?
Question 9
HOTSPOT - (Topic 1)
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 hosts 40 virtual machines that run Windows Server 2008 R2. The virtual machines connect to a private virtual switch.
You have a file that you want to copy to all of the virtual machines.
You need to identify to which servers you can copy files by using the Copy-VmFile cmdlet. What command should you run? To answer, select the appropriate options in the answer
area.
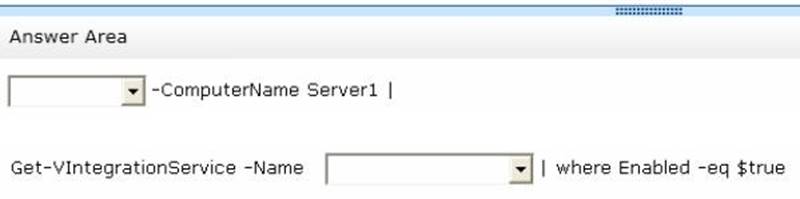
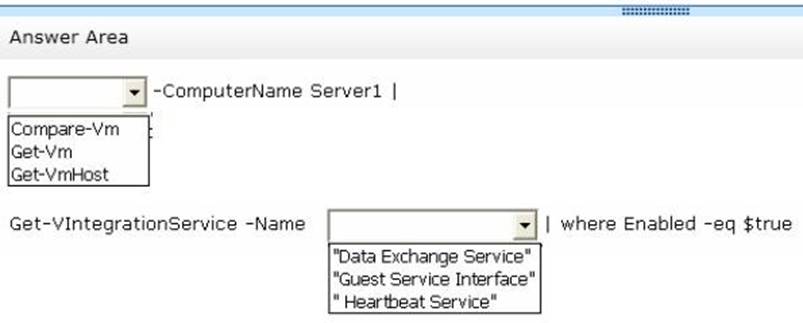
Solution:
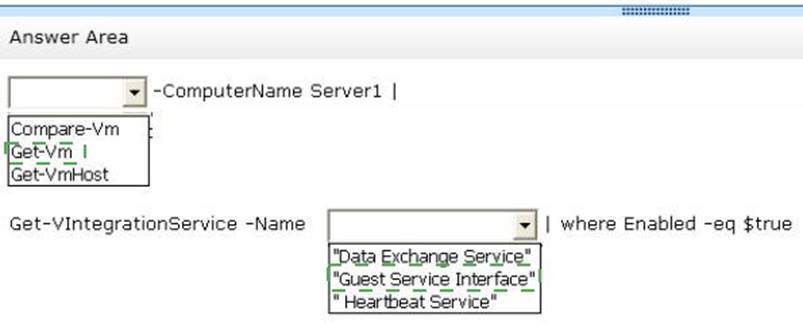
Does this meet the goal?
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 hosts 40 virtual machines that run Windows Server 2008 R2. The virtual machines connect to a private virtual switch.
You have a file that you want to copy to all of the virtual machines.
You need to identify to which servers you can copy files by using the Copy-VmFile cmdlet. What command should you run? To answer, select the appropriate options in the answer
area.


Solution:

Does this meet the goal?
Question 10
- (Topic 5)
Your network contains one Active Directory domain named contoso.com. The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
The domain contains an administrator account named Admin1.
You need to prevent Admin1 from creating more than 100 objects in the domain partition. Which tool should you use?
Your network contains one Active Directory domain named contoso.com. The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
The domain contains an administrator account named Admin1.
You need to prevent Admin1 from creating more than 100 objects in the domain partition. Which tool should you use?
Question 11
- (Topic 1)
Your network contains an Active Directory domain named contoso.com. You have a DHCP server named Server1 that runs Windows Server 2008.
You install Windows Server 2012 R2 on a server named Server2. You install the DHCP Server server role on Server2.
You need to migrate the DHCP services from Server1 to Server2. The solution must meet the following requirements:
✑ Ensure that existing leases are migrated.
✑ Prevent lease conflicts.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
Your network contains an Active Directory domain named contoso.com. You have a DHCP server named Server1 that runs Windows Server 2008.
You install Windows Server 2012 R2 on a server named Server2. You install the DHCP Server server role on Server2.
You need to migrate the DHCP services from Server1 to Server2. The solution must meet the following requirements:
✑ Ensure that existing leases are migrated.
✑ Prevent lease conflicts.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
Question 12
- (Topic 2)
Your network contains an Active Directory domain named contoso.com.
An administrator provides you with a file that contains the information to create user accounts for 200 temporary employees. The file is shown in the exhibit. (Click the Exhibit button.)
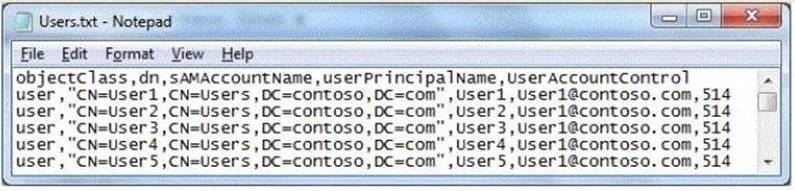
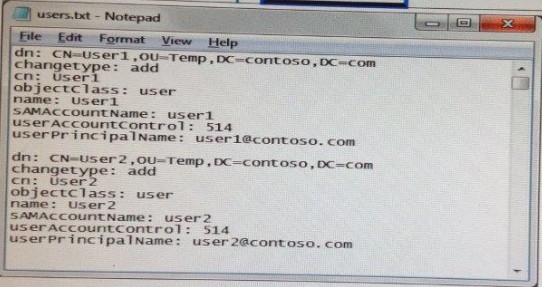
You need to automate the creation of the user accounts. You must achieve this goal by using the minimum amount of administrative effort.
Which tool should you use?
Your network contains an Active Directory domain named contoso.com.
An administrator provides you with a file that contains the information to create user accounts for 200 temporary employees. The file is shown in the exhibit. (Click the Exhibit button.)


You need to automate the creation of the user accounts. You must achieve this goal by using the minimum amount of administrative effort.
Which tool should you use?
Question 13
HOTSPOT - (Topic 5)
Your network contains an Active Directory domain named contoso.com. The domain contains 25 servers. All servers run Windows Server 2012 R2.
You need to create a Windows Firewall rule to prevent administrators from connecting to Remote Assistance requests while they are logged on interactively to the servers.
How should you configure the rule?
To answer, select the appropriate options in the answer area.
Solution:
Does this meet the goal?
Your network contains an Active Directory domain named contoso.com. The domain contains 25 servers. All servers run Windows Server 2012 R2.
You need to create a Windows Firewall rule to prevent administrators from connecting to Remote Assistance requests while they are logged on interactively to the servers.
How should you configure the rule?
To answer, select the appropriate options in the answer area.

Solution:

Does this meet the goal?
Question 14
HOTSPOT - (Topic 3)
Your network contains a domain controller named dc5.adatum.com that runs Windows Server 2012 R2.
You discover that you can connect successfully to DC5 over the network, but you receive a request timed out message when you attempt to ping DC5.
You need to configure DC5 to respond to ping request.
Which firewall rule should you modify on DC5? To answer, select the appropriate rule in the answer area.
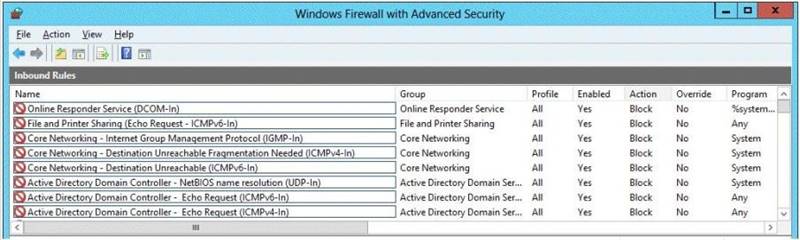
Solution:
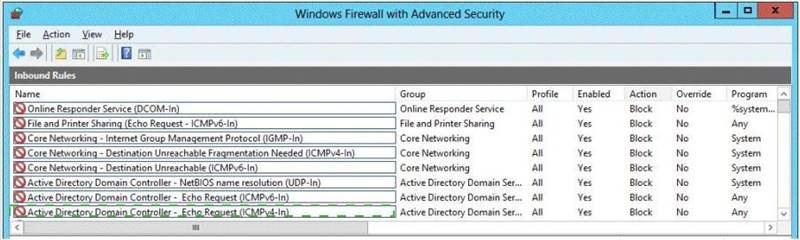
Does this meet the goal?
Your network contains a domain controller named dc5.adatum.com that runs Windows Server 2012 R2.
You discover that you can connect successfully to DC5 over the network, but you receive a request timed out message when you attempt to ping DC5.
You need to configure DC5 to respond to ping request.
Which firewall rule should you modify on DC5? To answer, select the appropriate rule in the answer area.

Solution:

Does this meet the goal?
Question 15
HOTSPOT - (Topic 3)
Your network contains an Active Directory domain named contoso.com.
Technicians use Windows Deployment Services (WDS) to deploy Windows Server 2012 R2.
The network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed.
You need to ensure that you can use WDS to deploy Windows Server 2012 R2 to a virtual machine named VM1.
Which settings should you configure?
To answer, select the appropriate settings in the answer area.
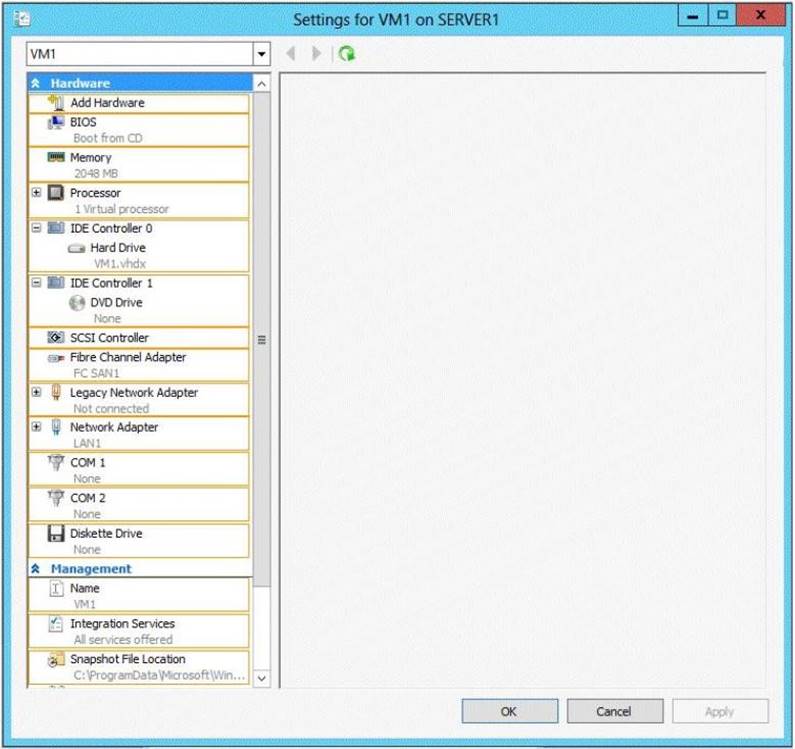
Solution:
WDS Allows network-based installation of Windows operating systems, which reduces the complexity and cost when compared to manual installations. Thus you should configure the appropriate network settings.
Does this meet the goal?
Your network contains an Active Directory domain named contoso.com.
Technicians use Windows Deployment Services (WDS) to deploy Windows Server 2012 R2.
The network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed.
You need to ensure that you can use WDS to deploy Windows Server 2012 R2 to a virtual machine named VM1.
Which settings should you configure?
To answer, select the appropriate settings in the answer area.

Solution:
WDS Allows network-based installation of Windows operating systems, which reduces the complexity and cost when compared to manual installations. Thus you should configure the appropriate network settings.
Does this meet the goal?
Question 16
- (Topic 5)
Your network contains an Active Directory domain named contoso.com. The domain contains two standalone servers named Serverl and Server2 that are located in a perimeter network. Both servers run the default installation of Windows Server 2012 R2.
You need to manage Serverl remotely from Server2. What should you do?
Your network contains an Active Directory domain named contoso.com. The domain contains two standalone servers named Serverl and Server2 that are located in a perimeter network. Both servers run the default installation of Windows Server 2012 R2.
You need to manage Serverl remotely from Server2. What should you do?
Question 17
HOTSPOT - (Topic 1)
You have a Hyper-V host named Hyperv1 that runs Windows Server 2012 R2. Hyperv1 hosts a virtual machine named Server1. Server1 uses a disk named Server1.vhdx that is stored locally on Hyperv1.
You stop Server1, and then you move Server1.vhdx to an iSCSI target that is located on another server.
You need to configure Server1 to meet the following requirements:
✑ Ensure that Server1 can start by using Server1.vhdx.
✑ Prevent Server1.vhdx from consuming more than 500 IOPS on the iSCSI target.
Which two objects should you configure? To answer, select the appropriate two objects in the answer area.
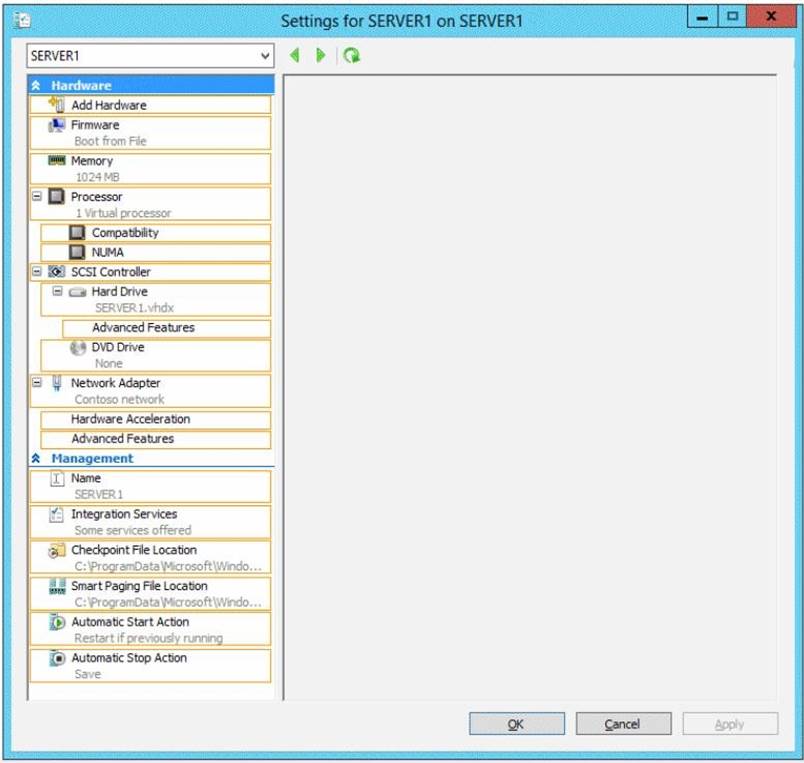
Solution:
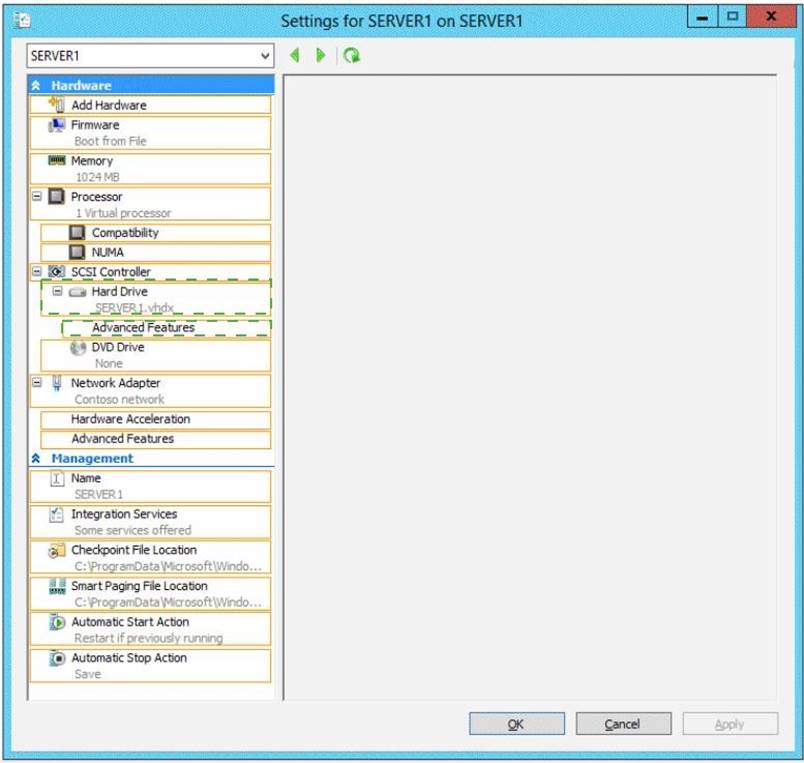
Does this meet the goal?
You have a Hyper-V host named Hyperv1 that runs Windows Server 2012 R2. Hyperv1 hosts a virtual machine named Server1. Server1 uses a disk named Server1.vhdx that is stored locally on Hyperv1.
You stop Server1, and then you move Server1.vhdx to an iSCSI target that is located on another server.
You need to configure Server1 to meet the following requirements:
✑ Ensure that Server1 can start by using Server1.vhdx.
✑ Prevent Server1.vhdx from consuming more than 500 IOPS on the iSCSI target.
Which two objects should you configure? To answer, select the appropriate two objects in the answer area.

Solution:

Does this meet the goal?
Question 18
- (Topic 1)
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. All servers run Windows Server 2012 R2. The domain contains two domain controllers named DC1 and DC2. Both domain controllers are virtual machines on a Hyper-V host.
You plan to create a cloned domain controller named DC3 from an image of DC1. You need to ensure that you can clone DC1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. All servers run Windows Server 2012 R2. The domain contains two domain controllers named DC1 and DC2. Both domain controllers are virtual machines on a Hyper-V host.
You plan to create a cloned domain controller named DC3 from an image of DC1. You need to ensure that you can clone DC1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
Question 19
HOTSPOT - (Topic 2)
You deploy a Server with a GUI installation of Windows Server 2012 R2 Datacenter. From Windows PowerShell, you run the following command:
Remove-WindowsFeature Server-Gui-Shell.
In the table below, identify which tools are available on Server1 and which tools are unavailable on Server1.
Make only one selection in each row. Each correct selection is worth one point.
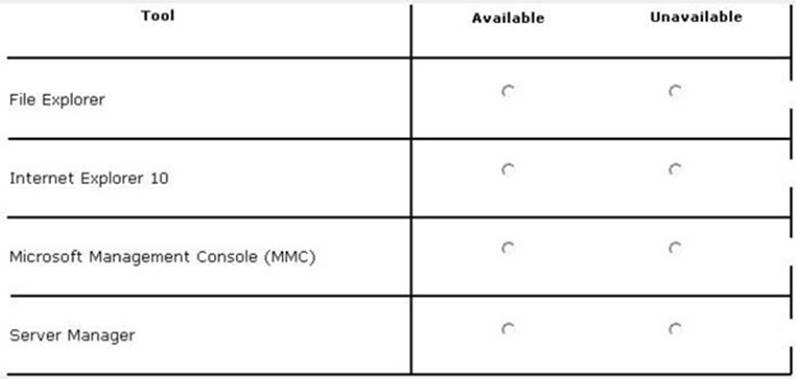
Solution:
When you uninstall "Server-GUI-Shell" you are left with a "Minimal Server Interface" server. So, File Explorer and IE10 are unavailable, but MMC and Server Manager work.
References:
Training Guide: Installing and Configuring Windows Server 2012 R2: Chapter 2: Deploying Servers, p.44
Exam Ref 70-410: Installing and Configuring Windows Server 2012 R2: Chapter 1: Installing and Configuring Servers, p.19-22
Does this meet the goal?
You deploy a Server with a GUI installation of Windows Server 2012 R2 Datacenter. From Windows PowerShell, you run the following command:
Remove-WindowsFeature Server-Gui-Shell.
In the table below, identify which tools are available on Server1 and which tools are unavailable on Server1.
Make only one selection in each row. Each correct selection is worth one point.

Solution:
When you uninstall "Server-GUI-Shell" you are left with a "Minimal Server Interface" server. So, File Explorer and IE10 are unavailable, but MMC and Server Manager work.
References:
Training Guide: Installing and Configuring Windows Server 2012 R2: Chapter 2: Deploying Servers, p.44
Exam Ref 70-410: Installing and Configuring Windows Server 2012 R2: Chapter 1: Installing and Configuring Servers, p.19-22
Does this meet the goal?
Question 20
- (Topic 1)
Your network contains an Active Directory forest named contoso.com. All domain controllers currently run Windows Server 2008 R2.
You plan to install a new domain controller named DC4 that runs Windows Server 2012 R2.
The new domain controller will have the following configurations:
✑ Schema master
✑ Global catalog server
✑ Active Directory Federation Services server role
✑ Active Directory Certificate Services server role
You need to identify which configuration can be fulfilled by using the Active Directory Domain Services Configuration Wizard.
Which configuration should you identify?
Your network contains an Active Directory forest named contoso.com. All domain controllers currently run Windows Server 2008 R2.
You plan to install a new domain controller named DC4 that runs Windows Server 2012 R2.
The new domain controller will have the following configurations:
✑ Schema master
✑ Global catalog server
✑ Active Directory Federation Services server role
✑ Active Directory Certificate Services server role
You need to identify which configuration can be fulfilled by using the Active Directory Domain Services Configuration Wizard.
Which configuration should you identify?
Question 21
HOTSPOT - (Topic 2)
You have a file server named Server1 that runs Windows Server 2012 R2. Server1 contains a folder named Folder1.
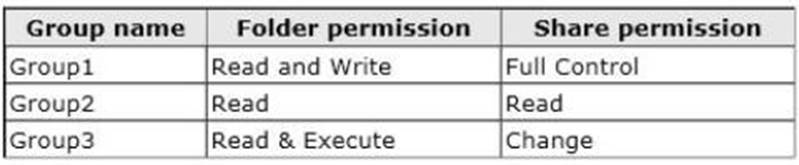
A user named User1 is a member of Group1 and Group2. A user named User2 is a member of Group2 and Group3.
You need to identify which actions the users can perform when they access the files in Share1.
What should you identify?
To answer, select the appropriate actions for each user in the answer area.
Solution:
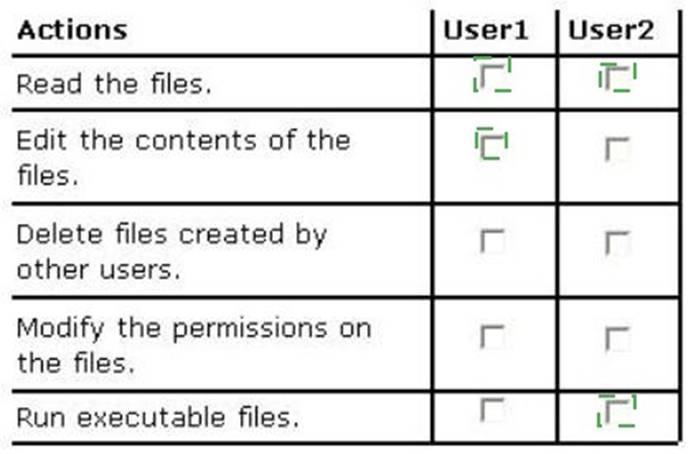
Does this meet the goal?
You have a file server named Server1 that runs Windows Server 2012 R2. Server1 contains a folder named Folder1.

A user named User1 is a member of Group1 and Group2. A user named User2 is a member of Group2 and Group3.
You need to identify which actions the users can perform when they access the files in Share1.
What should you identify?
To answer, select the appropriate actions for each user in the answer area.

Solution:

Does this meet the goal?
Question 22
- (Topic 1)
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
You create a security template named Template1 by using the security template snap-in. You need to apply Template1 to Server2.
Which tool should you use?
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
You create a security template named Template1 by using the security template snap-in. You need to apply Template1 to Server2.
Which tool should you use?
Question 23
DRAG DROP - (Topic 3)
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named File1. All servers in the domain run Windows Server 2012 R2.
You need to create a new volume on File1.
The new volume must have the following configurations:
✑ Have the drive letter T
✑ Have the FAT32 file system
✑ Be stored on a new virtual hard disk
In which order should you run the Diskpart commands?
To answer, move all the Diskpart commands from the list of commands to the answer area and arrange them in the correct order.
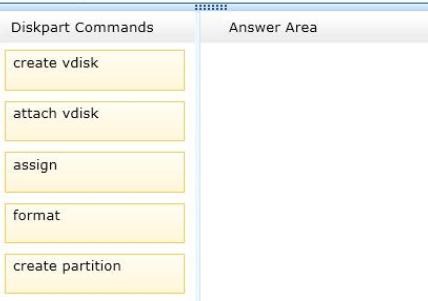
Solution:
Box 1: create vdisk Box 2: attach vdisk Box 3: create partition Box 4: assign
Box 5: format
Note: Example:
createvdisk file="C:\vdisks\disk1.vhd" maximum=16000 attachvdisk
create partition primary assign letter=g
format
References:
http://technet.microsoft.com/en-us/library/gg252576.aspx http://technet.microsoft.com/en-us/library/hh831487.aspx
Does this meet the goal?
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named File1. All servers in the domain run Windows Server 2012 R2.
You need to create a new volume on File1.
The new volume must have the following configurations:
✑ Have the drive letter T
✑ Have the FAT32 file system
✑ Be stored on a new virtual hard disk
In which order should you run the Diskpart commands?
To answer, move all the Diskpart commands from the list of commands to the answer area and arrange them in the correct order.

Solution:
Box 1: create vdisk Box 2: attach vdisk Box 3: create partition Box 4: assign
Box 5: format
Note: Example:
createvdisk file="C:\vdisks\disk1.vhd" maximum=16000 attachvdisk
create partition primary assign letter=g
format
References:
http://technet.microsoft.com/en-us/library/gg252576.aspx http://technet.microsoft.com/en-us/library/hh831487.aspx
Does this meet the goal?
Question 24
HOTSPOT - (Topic 5)
Your network contains an Active Directory domain named fabrikam.com. You implement DirectAccess and an IKEv2 VPN.
You need to view the properties of the VPN connection.
Which connection properties should you view? To answer, select the appropriate connection properties in the answer area.
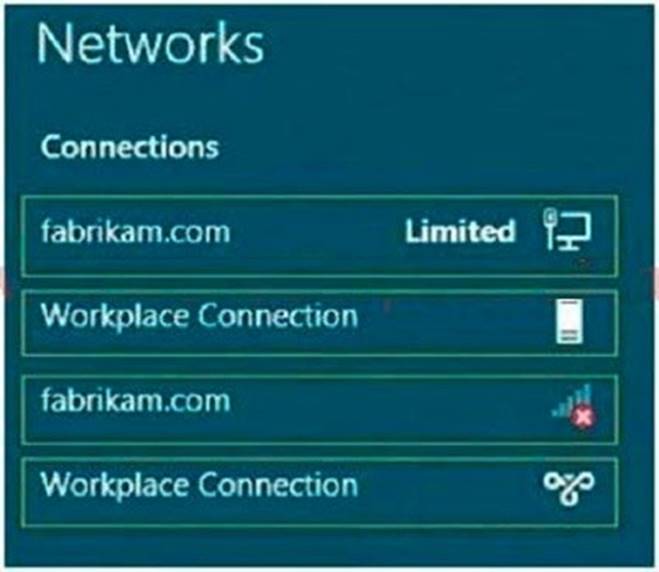
Solution:
WorkPlace Connection
Does this meet the goal?
Your network contains an Active Directory domain named fabrikam.com. You implement DirectAccess and an IKEv2 VPN.
You need to view the properties of the VPN connection.
Which connection properties should you view? To answer, select the appropriate connection properties in the answer area.

Solution:
WorkPlace Connection
Does this meet the goal?
Question 25
- (Topic 4)
You work as a senior administrator at Contoso.com. The Contoso.com network consists of a single domain named Contoso.com. All servers in the Contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators. You are currently discussing the Virtual Fibre Channel SAN feature.
Which of the following is TRUE with regards to the Virtual Fibre Channel SAN feature? (Choose all that apply.)
You work as a senior administrator at Contoso.com. The Contoso.com network consists of a single domain named Contoso.com. All servers in the Contoso.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators. You are currently discussing the Virtual Fibre Channel SAN feature.
Which of the following is TRUE with regards to the Virtual Fibre Channel SAN feature? (Choose all that apply.)
Question 26
- (Topic 5)
In a domain running at the Windows Server 2012 R2 domain functional level, which of the following security principals can be members of a global group? (Choose all answers that are correct.)
In a domain running at the Windows Server 2012 R2 domain functional level, which of the following security principals can be members of a global group? (Choose all answers that are correct.)
Question 27
HOTSPOT - (Topic 1)
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
You need to add a user named User1 to a group named ServerAdmins.
What command should you run? To answer, select the appropriate options in the answer area.
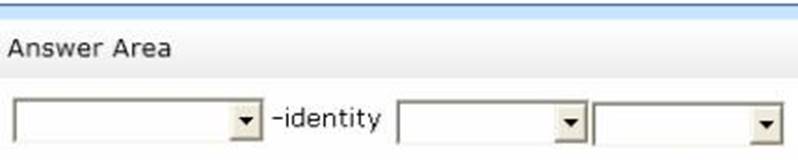
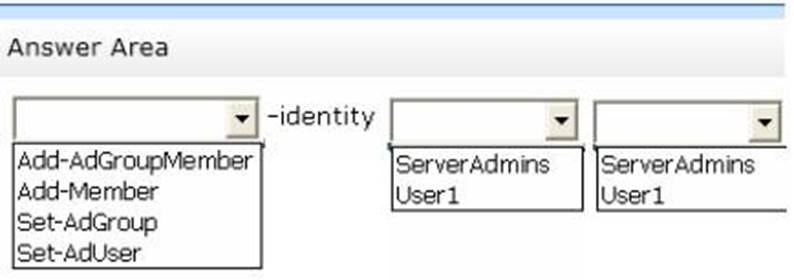
Solution:
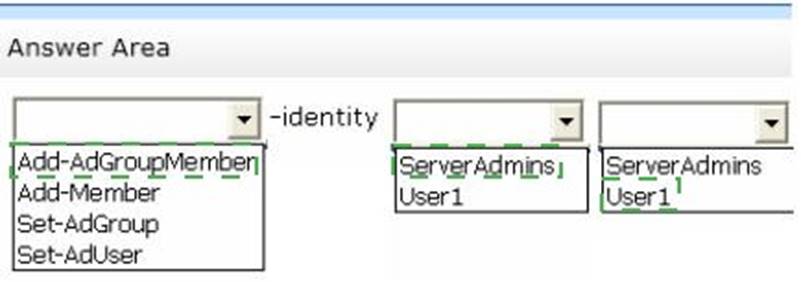
Does this meet the goal?
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
You need to add a user named User1 to a group named ServerAdmins.
What command should you run? To answer, select the appropriate options in the answer area.


Solution:

Does this meet the goal?
Question 28
- (Topic 5)
You work as a senior administrator at Contoso.com. The Contoso.com network consists of a single domain named Contoso.com. All servers on the Contoso.com network have Windows Server 2012 installed.
You are running a training exercise for junior administrators. You are currently discussing spanned volumes.
Which of the following is TRUE with regards to spanned volumes? (Choose all that apply.)
You work as a senior administrator at Contoso.com. The Contoso.com network consists of a single domain named Contoso.com. All servers on the Contoso.com network have Windows Server 2012 installed.
You are running a training exercise for junior administrators. You are currently discussing spanned volumes.
Which of the following is TRUE with regards to spanned volumes? (Choose all that apply.)
Question 29
- (Topic 5)
You have a Hyper-V host named server1 that runs windows server 2012 R2. Server1 host 50 virtual machines that run Windows Server 2012 R2.
You enable and configure enhanced session mode on Server1.
You need to identify a new functionality available for the virtual machines hosted on server1.
What should you identify?
You have a Hyper-V host named server1 that runs windows server 2012 R2. Server1 host 50 virtual machines that run Windows Server 2012 R2.
You enable and configure enhanced session mode on Server1.
You need to identify a new functionality available for the virtual machines hosted on server1.
What should you identify?
