16 October, 2020
What Accurate PCNSE Free Question Is
We provide real PCNSE exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Paloalto-Networks PCNSE Exam quickly & easily. The PCNSE PDF type is available for reading and printing. You can print more and practice many times. With the help of our Paloalto-Networks PCNSE dumps pdf and vce product and material, you can easily pass the PCNSE exam.
Free demo questions for Paloalto-Networks PCNSE Exam Dumps Below:
Question 1
If an administrator wants to decrypt SMTP traffic and possesses the server’s certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic to the server?
Solution:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/decryption/configure-ssl-inbound-inspection
Does this meet the goal?
Solution:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/decryption/configure-ssl-inbound-inspection
Does this meet the goal?
Question 2
Which authentication source requires the installation of Palo Alto Networks software, other than PAN-OS 7x, to obtain a username-to-IP-address mapping?
Question 3
Which GlobalProtect Client connect method requires the distribution and use of machine certificates?
Question 4
Which feature can provide NGFWs with User-ID mapping information?
Question 5
Which Security Policy Rule configuration option disables antivirus and anti-spyware scanning of server-to-client flows only?
Question 6
Only two Trust to Untrust allow rules have been created in the Security policy Rule1 allows google-base
Rule2 allows youtube-base
The youtube-base App-ID depends on google-base to function. The google-base App-ID implicitly uses SSL and web-browsing. When user try to accesss https://www.youtube.com in a web browser, they get an error indecating that the server cannot be found.
Which action will allow youtube.com display in the browser correctly?
Rule2 allows youtube-base
The youtube-base App-ID depends on google-base to function. The google-base App-ID implicitly uses SSL and web-browsing. When user try to accesss https://www.youtube.com in a web browser, they get an error indecating that the server cannot be found.
Which action will allow youtube.com display in the browser correctly?
Question 7
A Palo Alto Networks firewall is being targeted by an NTP Amplification attack and is being flooded with tens thousands of bogus UDP connections per second to a single destination IP address and post.
Which option when enabled with the correction threshold would mitigate this attack without dropping legitirnate traffic to other hosts insides the network?
Which option when enabled with the correction threshold would mitigate this attack without dropping legitirnate traffic to other hosts insides the network?
Question 8
Which CLI command enables an administrator to view details about the firewall including uptime, PAN-OS® version, and serial number?
Question 9
An administrator has left a firewall to use the default port for all management services. Which three
functions are performed by the dataplane? (Choose three.)
functions are performed by the dataplane? (Choose three.)
Question 10
Refer to the exhibit.

An administrator is using DNAT to map two servers to a single public IP address. Traffic will be
steered to the specific server based on the application, where Host A (10.1.1.100) received HTTP traffic and host B(10.1.1.101) receives SSH traffic.
Which two security policy rules will accomplish this configuration? (Choose two)

An administrator is using DNAT to map two servers to a single public IP address. Traffic will be
steered to the specific server based on the application, where Host A (10.1.1.100) received HTTP traffic and host B(10.1.1.101) receives SSH traffic.
Which two security policy rules will accomplish this configuration? (Choose two)
Question 11
Which CLI command can be used to export the tcpdump capture?
Solution:
Reference: https://live.paloaltonetworks.com/t5/Management-Articles/How-To-Packet-Capture-tcpdump-On-Management-Interface/ta-p/55415
Does this meet the goal?
Solution:
Reference: https://live.paloaltonetworks.com/t5/Management-Articles/How-To-Packet-Capture-tcpdump-On-Management-Interface/ta-p/55415
Does this meet the goal?
Question 12
An administrator is defining protection settings on the Palo Alto Networks NGFW to guard against resource exhaustion. When platform utilization is considered, which steps must the administrator take to configure and apply packet buffer protection?
Question 13
A network design calls for a "router on a stick" implementation with a PA-5060 performing inter- VLAN routing All VLAN-tagged traffic will be forwarded to the PA-5060 through a single dot1q trunk interface
Which interface type and configuration setting will support this design?
Which interface type and configuration setting will support this design?
Question 14
Site-A and Site-B need to use IKEv2 to establish a VPN connection. Site A connects directly to the internet using a public IP address. Site-B uses a private IP address behind an ISP router to connect to the internet.
How should NAT Traversal be implemented for the VPN connection to be established between Site-A and Site-B?
How should NAT Traversal be implemented for the VPN connection to be established between Site-A and Site-B?
Question 15
An administrator deploys PA-500 NGFWs as an active/passive high availability pair. The devices are not participating in dynamic routing and preemption is disabled.
What must be verified to upgrade the firewalls to the most recent version of PAN-OS software?
Solution:
Dependencies : Before upgrade, make sure the firewall is running a version of app + threat (content version) that meets the minimum requirement of the new PAN-OS Upgrade. Reference: https://live.paloaltonetworks.com/t5/Featured-Articles/Best-Practices-for-PAN-OS- Upgrade/ta-p/111045
Does this meet the goal?
What must be verified to upgrade the firewalls to the most recent version of PAN-OS software?
Solution:
Dependencies : Before upgrade, make sure the firewall is running a version of app + threat (content version) that meets the minimum requirement of the new PAN-OS Upgrade. Reference: https://live.paloaltonetworks.com/t5/Featured-Articles/Best-Practices-for-PAN-OS- Upgrade/ta-p/111045
Does this meet the goal?
Question 16
An administrator creates an SSL decryption rule decrypting traffic on all ports. The administrator also creates a Security policy rule allowing only the applications DNS, SSL, and web-browsing.
The administrator generates three encrypted BitTorrent connections and checks the Traffic logs. There are three entries. The first entry shows traffic dropped as application Unknown. The next two entries show traffic allowed as application SSL.
Which action will stop the second and subsequent encrypted BitTorrent connections from being allowed as SSL?
The administrator generates three encrypted BitTorrent connections and checks the Traffic logs. There are three entries. The first entry shows traffic dropped as application Unknown. The next two entries show traffic allowed as application SSL.
Which action will stop the second and subsequent encrypted BitTorrent connections from being allowed as SSL?
Question 17
Which three settings are defined within the Templates object of Panorama? (Choose three.)
Question 18
People are having intermittent quality issues during a live meeting via web application.
Question 19
An administrator needs to optimize traffic to prefer business-critical applications over non-critical applications. QoS natively integrates with which feature to provide service quality?
Question 20
The certificate information displayed in the following image is for which type of certificate? Exhibit:
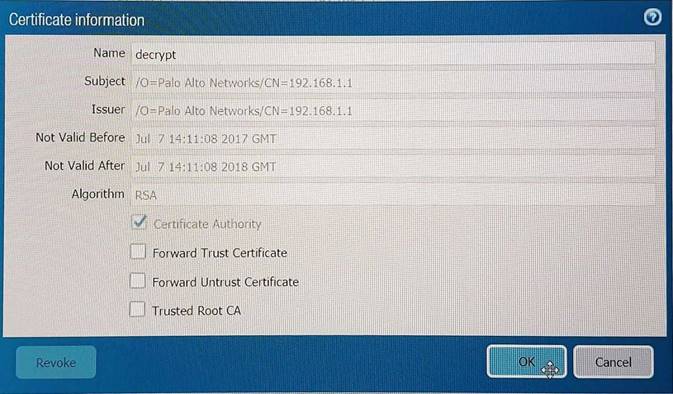

Question 21
Which two benefits come from assigning a Decryption Profile to a Decryption policy rule with a “No Decrypt” action? (Choose two.)
Question 22
A network security engineer is asked to perform a Return Merchandise Authorization (RMA) on a firewall
Which part of files needs to be imported back into the replacement firewall that is using Panorama?
Which part of files needs to be imported back into the replacement firewall that is using Panorama?
Question 23
An administrator logs in to the Palo Alto Networks NGFW and reports that the WebUI is missing the Policies tab. Which profile is the cause of the missing Policies tab?
Question 24
A web server is hosted in the DMZ, and the server is configured to listen for incoming connections only on TCP port 8080. A Security policy rule allowing access from the Trust zone to the DMZ zone need to be configured to enable we browsing access to the server.
Which application and service need to be configured to allow only cleartext web-browsing traffic to thins server on tcp/8080.
Which application and service need to be configured to allow only cleartext web-browsing traffic to thins server on tcp/8080.
Question 25
VPN traffic intended for an administrator’s Palo Alto Networks NGFW is being maliciously intercepted and retransmitted by the interceptor. When creating a VPN tunnel, which protection profile can be enabled to prevent this malicious behavior?
Question 26
A network security engineer is asked to provide a report on bandwidth usage. Which tab in the ACC provides the information needed to create the report?
Question 27
A network engineer has revived a report of problems reaching 98.139.183.24 through vr1 on the firewall. The routing table on this firewall is extensive and complex.
Which CLI command will help identify the issue?
Which CLI command will help identify the issue?
Question 28
An administrator needs to upgrade an NGFW to the most current version of PAN-OS® software. The following is occurring:
•Firewall has Internet connectivity through e1/1.
•Default security rules and security rules allowing all SSL and web-browsing traffic to and from any zone.
•Service route is configured, sourcing update traffic from e1/1.
•A communication error appears in the System logs when updates are performed.
•Download does not complete.
What must be configured to enable the firewall to download the current version of PAN-OS software?
•Firewall has Internet connectivity through e1/1.
•Default security rules and security rules allowing all SSL and web-browsing traffic to and from any zone.
•Service route is configured, sourcing update traffic from e1/1.
•A communication error appears in the System logs when updates are performed.
•Download does not complete.
What must be configured to enable the firewall to download the current version of PAN-OS software?
