09 July, 2024
What Exact GISF Sample Question Is
Your success in GIAC GISF is our sole target and we develop all our GISF braindumps in a way that facilitates the attainment of this target. Not only is our GISF study material the best you can find, it is also the most detailed and the most updated. GISF Practice Exams for GIAC GISF are written to the highest standards of technical accuracy.
Question 1
- (Topic 2)
Which of the following federal laws are related to hacking activities? Each correct answer represents a complete solution. Choose three.
Which of the following federal laws are related to hacking activities? Each correct answer represents a complete solution. Choose three.
Question 2
- (Topic 2)
Which of the following is the purpose of employing DMZ (Demilitarized zone) in a network?
Which of the following is the purpose of employing DMZ (Demilitarized zone) in a network?
Question 3
- (Topic 2)
Which of the following statements are true about security risks? Each correct answer represents a complete solution. Choose three.
Which of the following statements are true about security risks? Each correct answer represents a complete solution. Choose three.
Question 4
- (Topic 1)
Andrew works as a Network Administrator for NetTech Inc. The company has a Windows Server 2008 domain-based network. The network contains five Windows 2008 member servers and 120 Windows XP Professional client computers. Andrew is concerned about the member servers that are not meeting the security requirements as mentioned in the security policy of the company. Andrew wants to compare the current security settings of the member servers with the security template that is configured according to the security policy of the company. Which of the following tools will Andrew use to accomplish this?
Andrew works as a Network Administrator for NetTech Inc. The company has a Windows Server 2008 domain-based network. The network contains five Windows 2008 member servers and 120 Windows XP Professional client computers. Andrew is concerned about the member servers that are not meeting the security requirements as mentioned in the security policy of the company. Andrew wants to compare the current security settings of the member servers with the security template that is configured according to the security policy of the company. Which of the following tools will Andrew use to accomplish this?
Question 5
- (Topic 1)
You work as the Senior Project manager in Dotcoiss Inc. Your company has started a software project using configuration management and has completed 70% of it. You need to ensure that the network infrastructure devices and networking standards used in this project are installed in accordance with the requirements of its detailed project design documentation. Which of the following procedures will you employ to accomplish the task?
You work as the Senior Project manager in Dotcoiss Inc. Your company has started a software project using configuration management and has completed 70% of it. You need to ensure that the network infrastructure devices and networking standards used in this project are installed in accordance with the requirements of its detailed project design documentation. Which of the following procedures will you employ to accomplish the task?
Question 6
- (Topic 1)
Tom works as the project manager for BlueWell Inc. He is working with his project to ensure timely and appropriate generation, retrieval, distribution, collection, storage, and ultimate disposition of project information. What is the process in which Tom is working?
Tom works as the project manager for BlueWell Inc. He is working with his project to ensure timely and appropriate generation, retrieval, distribution, collection, storage, and ultimate disposition of project information. What is the process in which Tom is working?
Question 7
- (Topic 2)
You and your project team want to perform some qualitative analysis on the risks you have identified and documented in Project Web Access for your project. You would like to create a table that captures the likelihood and affect of the risk on the project. What type of a chart or table would you like to create for the project risks?
You and your project team want to perform some qualitative analysis on the risks you have identified and documented in Project Web Access for your project. You would like to create a table that captures the likelihood and affect of the risk on the project. What type of a chart or table would you like to create for the project risks?
Question 8
- (Topic 1)
You are working as a project manager in your organization. You are nearing the final stages of project execution and looking towards the final risk monitoring and controlling activities. For your project archives, which one of the following is an output of risk monitoring and control?
You are working as a project manager in your organization. You are nearing the final stages of project execution and looking towards the final risk monitoring and controlling activities. For your project archives, which one of the following is an output of risk monitoring and control?
Question 9
- (Topic 2)
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases.
The email header of the suspicious email is given below:
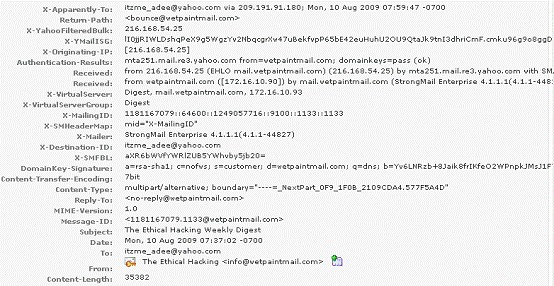
What is the IP address of the sender of this email?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases.
The email header of the suspicious email is given below:

What is the IP address of the sender of this email?
Question 10
- (Topic 2)
Mark works as a Customer Support Technician for uCertify Inc. The company provides troubleshooting support to users. Mark is troubleshooting a computer of a user who is working on Windows Vista. The user reports that his sensitive data is being accessed by someone because of security vulnerability in the component of Windows Vista. Which of the following features of Windows Security Center should Mark configure to save the user's data?
Mark works as a Customer Support Technician for uCertify Inc. The company provides troubleshooting support to users. Mark is troubleshooting a computer of a user who is working on Windows Vista. The user reports that his sensitive data is being accessed by someone because of security vulnerability in the component of Windows Vista. Which of the following features of Windows Security Center should Mark configure to save the user's data?
Question 11
- (Topic 1)
Which of the following does an anti-virus program update regularly from its manufacturer's Web site?
Which of the following does an anti-virus program update regularly from its manufacturer's Web site?
Question 12
- (Topic 2)
Which of the following is the best approach to conflict resolution?
Which of the following is the best approach to conflict resolution?
Question 13
- (Topic 2)
Which of the following types of firewall functions by creating two different communications, one between the client and the firewall, and the other between the firewall and the end server?
Which of the following types of firewall functions by creating two different communications, one between the client and the firewall, and the other between the firewall and the end server?
Question 14
- (Topic 1)
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system. He wants to sniff the weare- secure network and intercept a conversation between two employees of the company through session hijacking. Which of the following tools will John use to accomplish the task?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system. He wants to sniff the weare- secure network and intercept a conversation between two employees of the company through session hijacking. Which of the following tools will John use to accomplish the task?
Question 15
- (Topic 1)
Which U.S. government agency is responsible for establishing standards concerning cryptography for nonmilitary use?
Which U.S. government agency is responsible for establishing standards concerning cryptography for nonmilitary use?
Question 16
- (Topic 3)
Which of the following types of attack can guess a hashed password?
Which of the following types of attack can guess a hashed password?
Question 17
- (Topic 1)
Which of the following cryptographic algorithm uses public key and private key to encrypt or
decrypt data?
Which of the following cryptographic algorithm uses public key and private key to encrypt or
decrypt data?
Question 18
- (Topic 2)
Your computer continues to operate even if its disk drive has failed. This ability is known as _____.
Your computer continues to operate even if its disk drive has failed. This ability is known as _____.
Question 19
- (Topic 3)
You are the Network Administrator for a bank. You discover that someone has logged in with a user account access, but then used various techniques to obtain access to other user accounts. What is this called?
You are the Network Administrator for a bank. You discover that someone has logged in with a user account access, but then used various techniques to obtain access to other user accounts. What is this called?
