01 January, 2021
What Practical 1Z0-821 Exam Question Is
Passleader offers free demo for 1Z0-821 exam. "Oracle Solaris 11 System Administrator", also known as 1Z0-821 exam, is a Oracle Certification. This set of posts, Passing the Oracle 1Z0-821 exam, will help you answer those questions. The 1Z0-821 Questions & Answers covers all the knowledge points of the real exam. 100% real Oracle 1Z0-821 exams and revised by experts!
Check 1Z0-821 free dumps before getting the full version:
Question 1
To confirm the IP address and netmask have been correctly configured on the network interfaces which command should you use?
Question 2
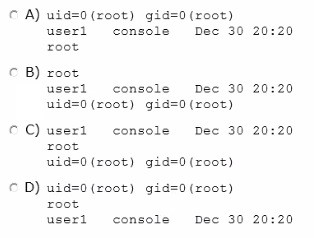
You log in to the system as user1, then switch user to root by using the su - command. After entering the correct password, yon enter the following commands:
whoami;who am i;id
Which option correctly represents the output?
whoami;who am i;id
Which option correctly represents the output?

Question 3
You have installed the SMF notification framework to monitor services. Which command is used to set up the notifications for a particular service?
Question 4
Which two statements are true concerning the creation of user accounts by using the useradd command?
Question 5
You have been tasked with creating a dedicated virtual network between two local zones within a single system, in order to isolate the network traffic from other zones on that system.
To accomplish this, you will create .
To accomplish this, you will create .
Question 6
Your users are experiencing delay issues while using their main application that requires connections to remote hosts. You run the command uptime and get the flowing output:
1:07am up 346 day(s), 12:03, 4 users, load average: 0.02, 0.02, 0.01 Which command will be useful in your next step of troubleshooting?
1:07am up 346 day(s), 12:03, 4 users, load average: 0.02, 0.02, 0.01 Which command will be useful in your next step of troubleshooting?
Question 7
The su command by default makes an entry into the log file for every su command attempt. The following is a single line from the file:
SU 12/18 23:20 + pts/1 user1-root What does the + sign represent?
SU 12/18 23:20 + pts/1 user1-root What does the + sign represent?
Question 8
Which three statements accurately describe the Automated Installation (AI) client?
Question 9
You are having an issue with the shutdown command. You wish to determine if the file is a script or an executable program. Which command would you use to determine this?
Question 10
Which modification needs to be made to the Service Management Facility before you publish a new package to the IPS repository?
Question 11
Which two are implemented using the Internet Control Message Protocol (ICMP)?
Question 12
Identify three options that describe the new Oracle Solaris 11 zone features.
Question 13
How are operating system updates distributed in the Oracle Solaris 11 environment?
Question 14
You want to deploy Oracle Solaris 11 with the Automated Installer (AI). You need to make sure that your server and network meet the requirements for using AI.
Choose the three options that describe the requirements for using AI.
Choose the three options that describe the requirements for using AI.
Question 15
You want to display network interface information. Which command should you use?
Question 16
View the Exhibit to see the information taken from the installation log file.
Based on the information presented in the Exhibit, which two options describe the state of the system when the server is booted for the first time after the installation is complete?

Based on the information presented in the Exhibit, which two options describe the state of the system when the server is booted for the first time after the installation is complete?

Question 17
You start to execute a program by using the following command:
~/bigscript &
You then determine that the process is not behaving as expected, and decide that you need to terminate the process.
Based on the information shown below, what is the process number you should terminate?

~/bigscript &
You then determine that the process is not behaving as expected, and decide that you need to terminate the process.
Based on the information shown below, what is the process number you should terminate?

Question 18
You are setting up an automated installer (AI) install server and issue the following command:
installadm create-service -n prod_ai -s /repo/prod_ai.iso
-i 192.168.1.100 -c 5 -d /export/repo
Which four options describe the install server that you have configured?
installadm create-service -n prod_ai -s /repo/prod_ai.iso
-i 192.168.1.100 -c 5 -d /export/repo
Which four options describe the install server that you have configured?
Question 19
Which statement is correct about shudown and init commands?
Question 20
You have already generated a 256-bit AES raw key and named the keystore file /mykey. You need to use the key to create an encrypted file system.
Which command should you use to create a ZFS encrypted file system named pool1/encrypt using the /mykey keystore?
Which command should you use to create a ZFS encrypted file system named pool1/encrypt using the /mykey keystore?
